1.1 Explain the role and function of network components
1.1.a Routers
1.1.b L2 and L3 switches
1.1.c Next-generation firewalls and IPS
1.1.d Access points
1.1.e Controllers (Cisco DNA Center and WLC)
1.1.f Endpoints
1.1.g Servers
What is a router? What is a L2 switch? What is an L3 switch? What is all this stuff and what does it do? We are already too deep into the material. Let’s take a step back and figure something out here.
A network is a bunch of connected devices. Think about your home or office. I have an office downtown, which has a network. All my office devices – laptops, servers, printers, etc. can connect. I also have a home. All my home devices – laptops, phones, printers, cameras can connect. If I’m working from home, I can still connect to my office network.
Google has a big network. I can connect to Google’s network from my home or office.
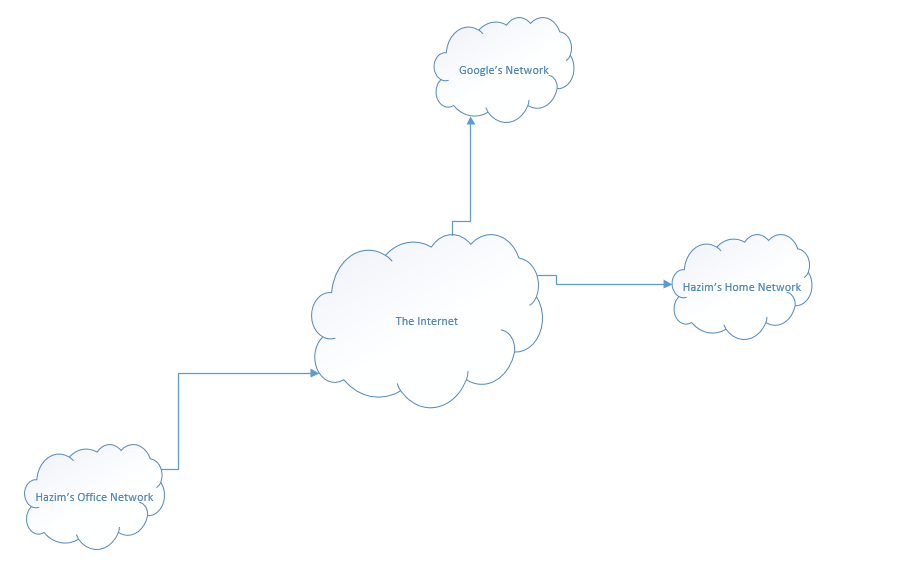
In the world, there are millions, or hundreds of millions of networks, all connected somehow. How does it all work?
Well, at the edge of each network is a router. We’re going to learn more about these routers later. But for now, we should understand that a router moves traffic between one network and another. It might move traffic between your home network and the internet. Or it might move traffic between your work network and your home network.
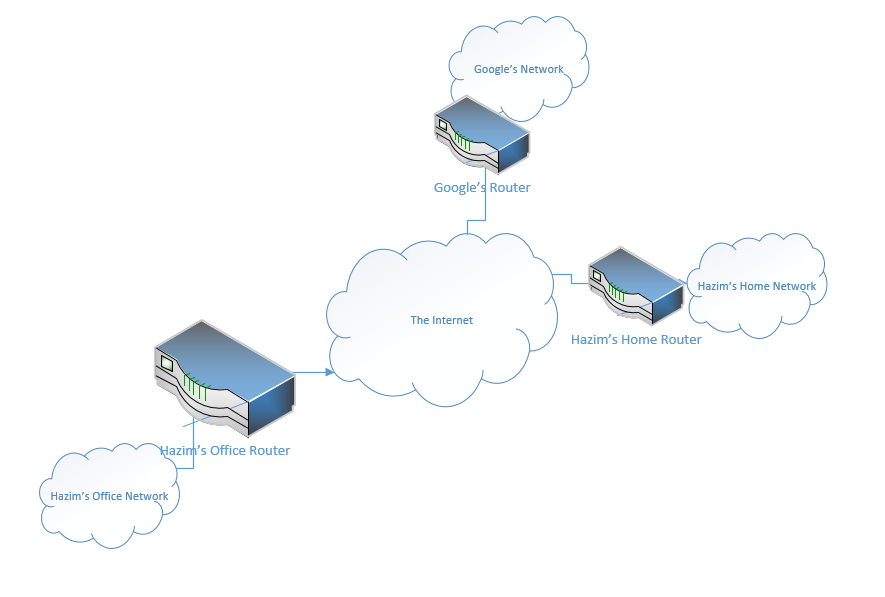
In each office, I also have a switch, or maybe I have several switches. Let’s take a closer look at my home network. I connected all my devices to a switch, like my TV, my desktop computer, and my printer. The switch forwards traffic between the devices on my network. If I want to print something, the traffic goes from my computer, to the switch, and then to the printer. We might call the network in my home a Local Area Network. That is, any equipment behind the router is a Local Area Network, or LAN.
If I want to access something on the internet (on another network – outside my LAN), the traffic must pass through the router.
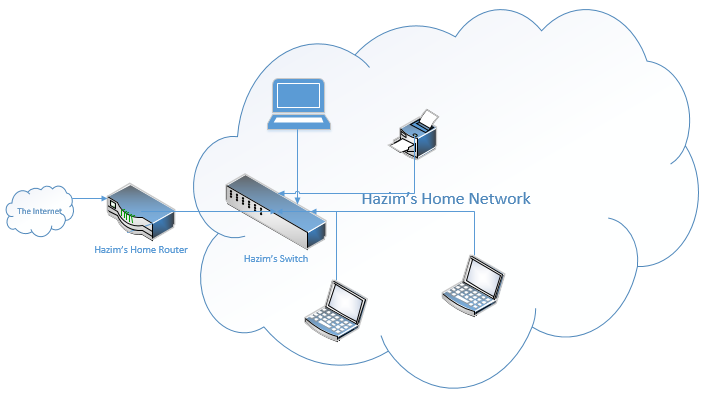
Going back to my switch – we call this type of Switch a Layer 2 Switch. More advanced switches are known as Layer 3 Switches (or multi-layer Switches). We’ll come back to the difference later, when it makes more sense.
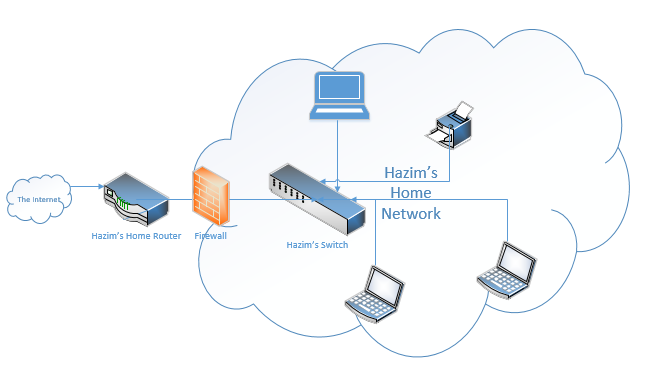
I also need to keep bad people out of my network. So, I add a firewall between the router and the rest of my network.
There are many types of firewalls. The most basic ones ask only a few questions
- Where is the traffic coming from? What is the source IP address of the traffic?
- Where is the traffic going? What is the destination IP address of the traffic?
The firewall has some rules. It compares the source and destination of the traffic to the rules and decides whether to let it through. It’s like looking at the to and from fields on an envelope before deciding whether to mail it.
Newer firewalls – known as Next Generation Firewalls – take a deeper look. They look at the contents of the traffic to decide if it’s good or bad. A Next Generation Firewall can ask some more questions
- What type of traffic is it? What is the port number? Is it HTTP traffic, VoIP traffic, FTP traffic, etc?
- If it’s HTTP or HTTPs traffic, what is the URL of the website? Is this a safe website?
- What is the state of the traffic? Did the connection originate from inside the network or from outside the network? This is known as stateful inspection.
For example, if you’re visiting a website, we would expect the connection to originate from inside the network. If a website originates the traffic, it’s probably from an imposter. - How many packets did this host send? A sudden surge of traffic from a specific source could be a symptom of an attack. If the firewall notices that we’re receiving a lot of traffic from a specific source, it could throttle it or slow it down.
A firewall can also use security zones. A security zone is a set of hosts (which could be internal or external). We might call each device on our network a “host”. Each zone can have different rules for what its hosts can access. For example, we could have trusted internal servers in one zone, trusted external webservers in a second zone, and untrusted sites in a third zone.
The most important zone in our network is the DMZ or Demilitarized Zone. We put servers that must access both the internal network and the internet in the DMZ. These could include web servers and e-mail servers. We need to access our e-mail from inside the network, and people on the internet need to access our e-mail server to send us e-mails.
Cisco next generation firewalls were called Cisco Adaptive Security Appliances or ASAs. The newer firewalls are called Cisco Firepower. The Firepower firewalls take a deeper look at each packet. It’s like opening each envelope and reading the contents before deciding whether to send it.
Why do we need to take a deeper look? A hacker can hide malicious information inside a legitimate-looking piece of data. For example, legitimate web traffic might come in disguised as legitimate web traffic. If a legitimate web server is compromised (through a virus or trojan), the hacker could use it to send malicious traffic.
This deep packet inspection is performed with a tool called Cisco Application Visibility and Control (AVC). The firewall can predict the application that is running inside the data.
We also use Intrusion Prevention Systems, or IPSs. The IPS is like a firewall, but more advanced. It checks every packet against a signature database to determine what to do with it. The IPS can detect viruses, worms, and DDoS attacks. Usually, the IPS comes preloaded with a signature database, and no configuration is required. The IPS might connect to the cloud and download new threat signatures to its database in real time. It might also share threats that it detects with other IPSs; if one IPS detects an early threat, it can share it with other IPSs, so that they all benefit.
In addition to its database, the IPS uses heuristics, or artificial intelligence to detect threats. If it detects a packet that might be a threat, but it’s not sure, it sends it to the cloud for further analysis. Researchers take a closer look at the packet and decide whether to include it in the database.
Cisco has created Next Generation IPSs, which can look deeper inside the hosts on the internal network. The Next Generation IPS will identify the types of operating systems, applications, and protocols running on the internal network. They also identify the ports in use on the internal network. This is known as Contextual Awareness.
With this information, the NGIPS can do two things
- Detect abnormalities in the network, such as devices with unrecognized or non-typical operating systems and applications
- Avoid spending time looking for threats against devices that do not exist in the network
Like the firewall, the Cisco NGIPS provides Application Visibility and Control. It also provides Reputation-Based Filtering. Cisco tracks bad people on the internet based on their domain names, IP addresses, and names. Cisco assigns each network resource (web server, website, etc.) a reputation score. With this information, your NGIPS can block traffic that has a bad reputation.
Each time the IPS matches a packet, it creates a security alert. Over time, an IPS can create millions of security alerts; it’s not possible for a human to read all of them. The NGIPS also uses Event Impact Levels to help rank each alert, so that an administrator can focus on the issues that could cause the most harm.
In summary, a Cisco Next Generation Firewall/IPS can do the following
- All the functions of a traditional firewall
- Application Visibility and Control
- Blocking specific URLs (websites) based on the reputation of the website. This is called Reputation-Based Filtering.
- Detection of malware
- All the functions of a standard Intrusion Protection System
Going back to my network, I have many laptops. Some of these laptops don’t want to sit in one spot. I want to sit on the patio and do some work. So, I install a Wireless Access Point, or WAP. The WAP connects to the switch and broadcasts a Wi-Fi signal, which all my (wireless-capable) devices can connect to.
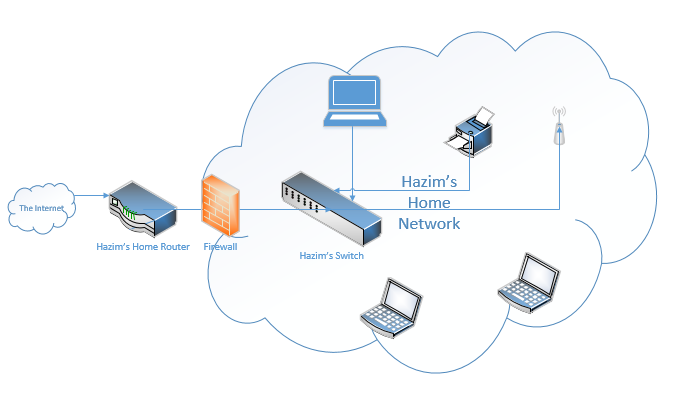
If I have lots of WAPs, then I need to add a controller. If I had an office with 20 or 30 or 100 access points, I wouldn’t want to manually configure each one. The controller configures and monitors the WAPs automatically. The controller is known as a WLC or Wireless Controller. A more advanced Cisco controller is called the Cisco DNA Center. We will learn more about it later.
My network might also have a server. Servers are computers that serve multiple users. For example, I might have a server for sharing important files with multiple users. Or I might have a server that handles my e-mail.
Each of the end user devices (printers, laptops, desktops, phones, etc.) is known as an endpoint or an end-user device.
In a home network, we might have one physical device that performs all the functions: router, firewall, switch, and wireless access point all in one. It doesn’t have a wireless controller, but the access point functions independently.
The home network device also functions as a modem and connects to a cable, DSL, fiber optic, or 4G connection.
We will learn more about the different devices and how to configure them later in this book.
