2.6 Compare Cisco Wireless Architectures and AP modes
You can think of a wireless access point like a switch in that it allows multiple devices to connect to it and it moves their traffic to the wired network. When an access point is equipped with both wireless and wired connections, it is considered autonomous.
The autonomous WAP broadcasts one or more SSIDs which are mapped to VLANs. We call each of these SSIDs a Wireless LAN or WLAN.
What really makes a WAP autonomous is that when two wireless clients are connected to the same access point and attempt to exchange traffic, the access point can directly transfer data between them. It doesn’t have to route the traffic through a switch (to a switch and back).
Autonomous WAPs become a problem when we have many access points. Why?
- We need to configure a management IP address on each access point so that we can log in and configure it remotely. Failing that, we would need to connect a console cable to each access point and configure it manually, which would be a hassle.
- That means we need to create a management VLAN that each access point can access. We should put the management IP on a management VLAN so that unauthorized users cannot access it.
- Each time a client associates and disassociates (roams), it should be able to keep the same IP address. That means that if I’m walking around a large building, my wireless devices should remain connected to the Wi-Fi.
- If we create a new VLAN, we must set it up on every access point and switch. That requires us to manually reconfigure each WAP.
How do we solve these problems? In the past, the solution was to purchase a device called a wireless controller. The wireless controller is part of a set of tools called Cisco Prime Infrastructure and helps us configure and manage WAPs automatically.
We install the controller on our network and configure our Wi-Fi on the controller. When a WAP connects to the network, it looks for a controller. The controller configures the WAP automatically from a template.
If we log in to the controller and change the network configuration, the controller automatically changes the configuration on each connected WAP.
Controllers are less popular now – they are being replaces with cloud-based WAPs. The WAP management is no longer on a physical controller in your network, but in the cloud. You configure the network through a web-based control panel. Each time a WAP is connected to the network, it reaches out to a cloud server and downloads its configuration.
The Cisco cloud is called Meraki and it can configure more than just WAPs. The beauty of Meraki is that it allows us to configure networks across multiple buildings and countries from the same interface. When you purchase a new WAP, you register its serial number on the Meraki cloud. You tell the cloud how the WAP fits into your network. When the WAP connects to the cloud, it knows what configuration to download. We might also call this zero-touch provisioning.
Some things that the cloud can do
- Configure the WAPs without a management VLAN
- Upgrade the firmware on each WAP
- Upgrade the configuration on each WAP
- Change the channel and transmit power that each WAP uses based on the conditions and detected interference
- Monitor device statistics
- Monitor and report on rogue devices
The cloud does not see the actual Wi-Fi data. That passes from the WAP to the physical local network or to the internet as required. The cloud only provides the management. User data travelling over the network takes a route called the data plane, while configuration data and statistics take a route called the control plane.
Some of the tasks that the WAP does in real time
- Transmit and Receive data
- Manage MAC addresses of connected devices
- Encrypt and decrypt traffic
Some of the management tasks that the WAP must do
- Manage the power and channel use
- Allow devices to roam and associate
- Authenticate clients
- Manage Quality of Service
- Manage security
We can create a WAP that just handles the real time tasks. This type of WAP is called called the lightweight access point. The management tasks are then outsourced to a controller known as a Wireless LAN Controller, or WLC. It is better if these management tasks are handled centrally because they involve more than one access point. Forcing each WAP to handle these tasks would consume unnecessary resources or be inefficient.
The lightweight WAP (LAP) handles only Layer 1 and Layer 2 functions, while the other functions are handled by the WLC. Unlike an autonomous WAP, the LAP cannot function on its own. We call this a split-MAC architecture.
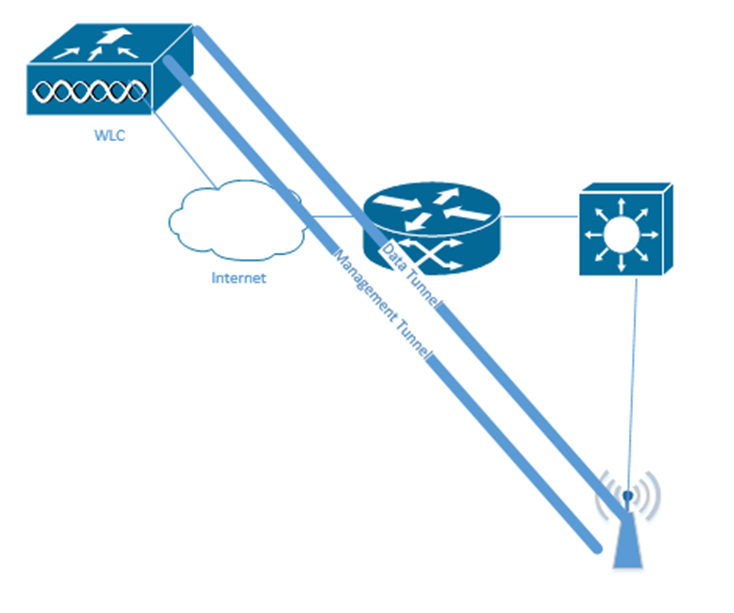
The LAP and WLC communicate through a tunnel. When I say tunnel, I mean that the LAP and WLC package all their traffic and transport it over the normal network, but they do so in a way that encapsulates all their traffic. This tunnel can operate over different networks and VLANs. We could put the controller in a central location and use it to manage LAPs that are in different physical locations.
How does the LAP communicate with the WLC? It uses the Control and Provisioning of Wireless Access Points protocol, or CAPWAP. If each LAP and WLC has a valid IP address, and the underlying network is working properly, management data is encapsulated inside an IP packet and then transported.
The CAPWAP creates two tunnels
- CAPWAP control messages are used to configure the LAP and manage its operation. The WLC and LAP encrypt the messages so that a rogue WLC cannot change the LAP’s configuration.
The management traffic is encapsulated, so we don’t need to create a separate management VLAN. - CAPWAP data travel between the clients and the LAPs. This data is not encrypted.by default but can be. Thus, the data travels from the host device to the LAP and then to the WLC and then to the destination.
The data is encapsulated in an IP Packet. This is important because we no longer need to configure VLANs on the switches that the LAPs are connected to. We only configure the VLANs on the WLC, and the WLC configures the VLANs on the LAPs.
How do we ensure that the LAP and WLC trust each other? From the factory, each LAP and WLC comes with a certificate. The LAP checks the certificate on the WLC to ensure that it is legitimate, and the WLC checks the certificate on each LAP to ensure that they are legitimate. This prevents a hacker from installing a rogue LAP on your network.
Some of the things that the WLC does for us
- It automatically changes the channel each LAP is using so that neighboring LAPs have different channels
- It adjusts the transmit power of each LAP so that their signals do not interfere
- It allows a client to roam from one LAP to another without disruption to its connection
- If there are multiple LAPs in the same area and one is overloaded (has too many clients), it can force some of those clients onto another LAP. This is known as client load balancing.
- It monitors the radio frequencies being transmitted by devices in the coverage area. This allows it to detect rogue APs, ad hoc devices, and interference.
- It authenticates clients so that only authorized devices can connect to the network.
- It redirects clients to a DHCP server so that they can obtain an IP address before connecting to the network.
Think about the tunnels. We want each tunnel to be approximately the same length. If we put the WLC at the edge of the network, some tunnels will be short, and some will be long. Traffic over the long tunnels would experience more latency. We should install the WLC in a central location. This is called a centralized WLC deployment.
The WLC should connect to a switch in the core layer. We should think about how many access points we have and how many we plan to purchase in the future. We should also think about how many clients we have and how many we plan to add. That allows us to purchase a WLC that has enough capacity to support the network. We may need to purchase more than one WLC if our network is large enough or if we want to add redundancy.
It is possible to set up a WLC as a virtual machine, which can be installed in the cloud. We call this a cloud-based WLC deployment. We can deploy multiple virtual machines if we need multiple WLCs.
Some Cisco switches come with built in WLCs, each of which can each handle a small number of LAPs. In a small network, or a distributed network where each location has a small number of LAPs, we can install Cisco switches with built in WLCs instead of purchasing a large standalone WLC. We call this an embedded WLC deployment. The LAP does not have to be directly connected to the switch that is running the WLC, it just has to be reachable by the switch.
If we have a very small office, we can install one AP that has a built in WLC. Other LAPs in the office connect to this AP’s controller. We call this the Cisco Mobility Express WLC deployment.
A WLC can support up to 6000 LAPs and 64,000 clients. A VM-based WLC can support up to 3000 LAPs and 32,000 clients. A Cisco switch-based WLC can support up to 200 LAPs and 4000 clients. An AP with a built-in WLC can support up to 100 LAPs and 2000 clients.
When the LAP powers on, it can operate in one of several modes
- Local. The LAP is broadcasting at least one BSS (SSID) on one channel. The LAP is also scanning the other channels and reporting the noise, interference, and rogue devices to the WLC. The LAP can only scan the other channels when it is not transmitting data.
The Local mode is the default mode. If we change the LAP’s mode to one of the other modes, the local mode is disabled, and the AP stops broadcasting the BSS. - Monitor. The LAP will not transmit any data, but it is monitoring the wireless environment for noise, interference, and rogue devices. The LAP is also predicting where the other LAPs are located.
- FlexConnect. If we install a LAP in a site that does not physically contain a WLC, then there is a risk that the LAP loses connectivity with the WLC. When the CAPWAP tunnel loses connectivity, the LAP acts like a Layer 3 switch and moves traffic between an SSID and its respective VLAN, without having to send it to the WLC.
- Sniffer. A sniffer is when the LAP captures traffic that is sent from other devices. The LAP is secretly capturing wireless traffic that is being broadcast in its coverage area. This traffic can be sent to a packet analysis program or a server.
- Rogue Detector. The AP listens for traffic and collects the MAC addresses of devices on the network that are transmitting data. If we see a MAC address that is on the wireless network and on the wired network, then we can assume it is a rogue device.
- Bridge. The LAP connects two networks together. We can put multiple LAPs in bridge mode to create a mesh network, or a point-to-multipoint network. We can put two LAPs in bridge mode to create a point-to-point network (such as those in Part 1).
- Flex+Bridge. This combines the FlexConnect feature with the Bridge feature, so that we can enable VLAN switching on a mesh network.
- SE-Connect. The LAP collects wireless spectrum data to determine if there are sources of interference. We need to use a spectrum analysis program to analyse the data.
