4.9 Describe the capabilities and function of TFTP/FTP in the network
FTP is an important protocol for transferring files over the internet. An FTP server holds files and accepts incoming connections from FTP clients. FTP clients connect to the FTP server and download files. During the connection, the client and the server complete a three-way handshake. The client and server authenticate with each other. Once the FTP server has authenticated the client and the client has optionally authenticated the server, they can issue commands to each other.
The FTP protocol has a standard set of commands that allow us to do the following
- List the contents of a directory or move to a new directory (folder).
- Create a new directory.
- Delete an existing directory.
- Transfer a file from the server to the client (via a Get command).
- Transfer a file from the client to the server (via a Put command).
Once a connection has been established, the client can perform these commands on the server and the server can perform these commands on the client.
It is possible to access an FTP server via a command line, but most people prefer to use an FTP client application with a graphical user interface. The GUI provides an interface like Windows Explorer/Mac Finder so that we can browse directories and drag/drop files.
The FTP server is built in to Windows Server Operating systems but must be enabled and configured. We can also install a commercial FTP server application that provides advanced features such as logging and user authentication.
When configuring an FTP server, it is important to ensure that each user only has access to the specific files and directories that he requires.
During an FTP session, there are two sub-connections. A Control Connection is used to exchange FTP commands. A Data Connection is used to send and receive data. This data includes lists of files and directories and the actual transfer of files.
The Control Connection is created when the client connects to the FTP server. An FTP connection’s three-way handshake is like that of any other TCP Connection.
- The client sends a TCP SYN message to the server.
- The server acknowledges the TCP SYN with a TCP ACK and sends its own TCP SYN to the client.
- The client replies with a TCP ACK message to the server.
Once the handshake is established, the client chooses a port to communicate over. The FTP server uses Port 21. The client can choose any dynamic port that is not in use. It must inform the server of the port that it selected via the FTP PORT command. For example, if our client selected port 49876, it would tell the FTP server that it wants to communicate on 49876.
Once the server receives the FTP PORT command, it tries to establish a connection with the client over port 49876. This system is called Active FTP.
If the FTP server is on a local network, Active FTP can operate without any issues. If the FTP server and FTP client are separated by a router and/or a firewall, the connection might be blocked due to the strange port selected by the client. The firewall will typically block incoming connections.
We can get around this issue with Passive FTP. The client doesn’t know that a firewall is blocking the connection. But if it doesn’t receive a connection from the FTP server, after successfully establishing a connection, it assumes that something is blocking it.
The client sends the server an FTP PASV command. The server chooses a dynamic port to listen on. For example, the server might choose port 49876. The FTP server tells the client that it chose port 49876 with the FTP PORT command. The client connects to the FTP server over port 49876. The firewall will probably not block this connection because it originated inside the network.
FTP is not secure. Usernames, passwords, and files are sent over the internet in plaintext. But we can implement a secure FTP called FTP over TLS or FTP Secure (FTPS). We create the same three-way handshake as before. During the handshake, the client informs the server that it would like to use TLS by providing the FTP AUTH command. When the client chooses to send data to the FTP server, it does so via port 21 over TLS.
TFTP, or Trivial File Transfer Protocol is a stripped-down version of FTP that uses port 69. TFTP is used on devices that have limited resources. We can use the Get and Put commands to download and upload files, but we can’t authenticate with the server or list directories. That means that a client must know the exact name of the file that it wants to download and sends the server a command telling it to provide it with a specific file.
Since anybody can access the TFTP server without a password, we should only use it to store files that are available to the public.
One use of FTP and TFTP is to transfer a copy of the IOS operating system. Unlike Windows, IOS (the Cisco router and switch operating system) is stored as a single file.
Some background on Cisco file storage systems. A Cisco router or switch stores data on a flash memory, which has no moving parts, and can continue to store data even after the router has been powered off. Some Cisco devices allow you to remove the flash memory.
Some Cisco devices also include USB ports. When we have a USB port, we can store data on a removable USB flash drive.
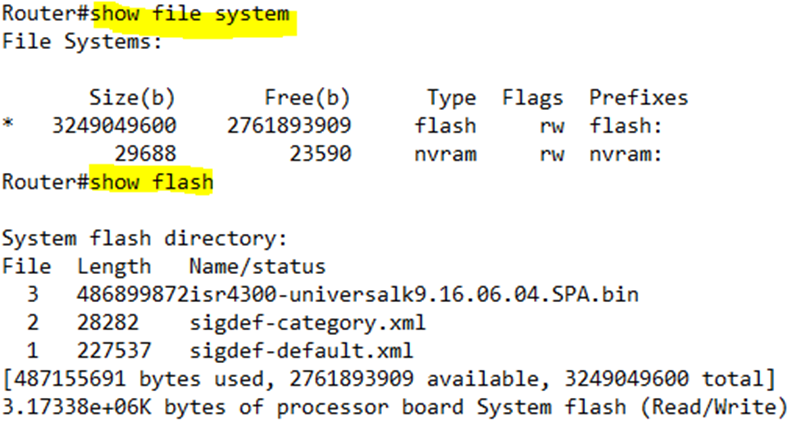
We can view the device file system by typing show file systems. A Cisco device will have multiple file systems. The main types of file systems are
- Disk. The disk is the flash memory and is present in every device.
- Usbflash. The USB Flash drive that may be inserted into the device (if the device has this capability)
- NVRAM. A portion of the flash memory that stores the startup-config file.
- Opaque. An internal file system that the router uses to run internal processes.
- Network. External file systems that are located on external servers, if the device can connect to them.
I can type show flash to view the files in the flash file system. I can also type dir flash. Both commands tell us the amount of space in use and the amount of space available.
Remember again that if I type show running-config, I can view the contents of the configuration in the memory. If I type show startup-config, I can view the contents of the startup configuration.
If we make changes to the device configuration, the running-config is updated, not the startup-config. When the router or switch reboots it reloads the startup-config and copies it into memory. The startup-config becomes the running-config. If we want changes to our running-config to become permanent, we should save them to the startup-config.
It is technically possible to store the Cisco IOS on an external server. Each time the router or switch boots, it loads the IOS over the network. But this is a bad idea because if the external server is inaccessible, the router won’t be able to boot. A better approach is to store the operating system on the Flash.
To upgrade the IOS, we can obtain a new version from the Cisco website. We can copy it to an external server or to a USB flash drive. Then, we copy it to the router by typing copy <source> <destination>. The Cisco device will ask us more questions when we type this command.
For example, to copy a file from an TFTP server to the Flash, we type copy tftp flash. The router will ask us about the IP address of the TFTP server and the filename. By default, the destination filename will be the same as the source, but we have the option to enter a new name. If we want to use the name in [], we can just press Enter.
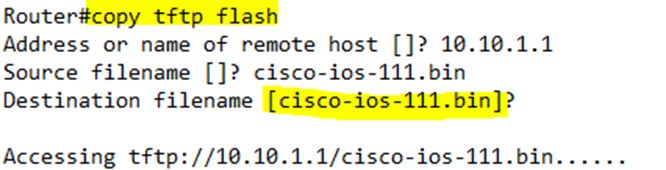
Before the router copies the file, it checks the file size and verifies that it has enough space to copy it. If the Flash has a file with the same name, the router will ask us to overwrite the existing one.
We should make sure that our TFTP server is accessible to our router or switch.
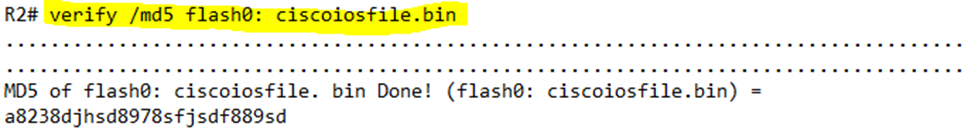
After we have downloaded the file, we should verify that it is legitimate. Cisco publishes an MD5 hash for each IOS file on its website. We can recalculate the MD5 hash on the router. If the hash calculated by the router matches the hash on the Cisco website, we know that the file is legitimate and that no errors occurred in transmission.
We can type verify /md5 <filename> to calculate the hash.
Instead of using TFTP, we can copy a file via FTP or SCP.
To copy a file over FTP, we use a similar command as TFTP, by typing copy ftp flash. It is important to note that the TFTP command expects an IP address for the TFTP server, while the FTP command allows us to enter a URL or hostname. Note that the switch or router must have a DNS server configured for us to successfully be able to use a URL or hostname in the command.
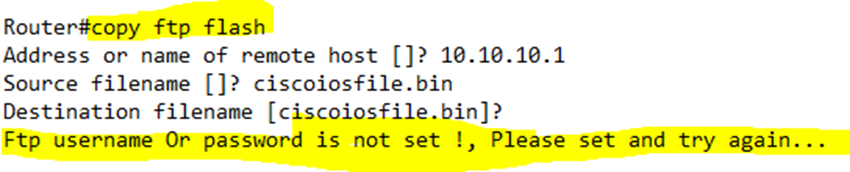
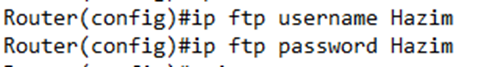
Before we run the FTP command, we should set a username and password in the global configuration; otherwise, we will see the above error.
We set the FTP Username via the ip ftp username <username> command and the FTP Password via the ip ftp password <password> command.