5.1 Define key security concepts (threats, vulnerabilities, exploits, and mitigation techniques)
The key to a good security policy is to keep the bad people out, but also to avoid inconveniencing the legitimate users. The cost of the security should not be greater than the risk caused by a lack of security. We must always remember that if the security policy stops a business from operating efficiently, it will not be effective.
An enterprise network is complicated
- We have thousands to hundreds of thousands of users and thousands to hundreds of thousands to millions of different devices spread across multiple locations.
- Users have different roles, and each role requires access to different resources.
- Some users want to work from home or from the road, but they need to connect to the enterprise network.
- Users might want to use their personal devices on the network, including laptops and smartphones.
- The enterprise network may need to exchange data with other networks such as the government, vendors, or customers.
- There are many different network devices from many different vendors.
- Parts of the network are in different states or countries. Each state or country may have different laws about how data is stored or transmitted.
A weakness in our network is called a vulnerability. Somebody can take advantage of a vulnerability to penetrate our network. They do so with a malicious tool called an exploit. An exploit is a tool that is used against a vulnerability. The scenario where a person uses an exploit to take advantage of a vulnerability is called a threat.
We can reduce the risk that a threat poses by using a mitigation technique. But first, we must identify the threat.
For example, if a router has a flaw in its firmware that might be a vulnerability. A tool that can be used to enter the router without permission, by taking advantage of the firmware flaw is an exploit. If a hacker uses this tool, that is a threat. We might install a firewall or upgrade the router’s operating system as a mitigation technique.
How can we secure the whole network when we have
- Different types of equipment such as Routers, Switches, Wireless Access Points and Controllers
- Different models of equipment
- Different ages of equipment each of which may be running a different version of the firmware or operating system
We might not even know what all the different threats are. Before we can secure the network, we must first understand what all the components are and where the vulnerabilities lie. That means
- Identify the physical location of every device and how it connects to other devices
- Identify the logical connections of every device including IP addresses, virtual ports, and VLANS
- Identify the make, model, and serial number of every device. Identify the operating system version running on every device. If a vulnerability arises in an operating system that we are using, we can patch it.
There are many types of attacks. For the CCNA, it is important to understand them in general terms, but for the real world, it is important to know exactly what they are. This chapter goes into a lot more detail than you’re expected to know.
One type of threat is called spoofing. Each device within the network assumes that the other devices are who they say they are. If a device says that it has a specific IP address and MAC address other devices assume that it is telling the truth.
In a spoofing threat, a rogue device can change its IP address or MAC address so that it matches that of a legitimate device and then send traffic as that device. Devices receiving the traffic will assume that it originated from a legitimate device.
Recall that each network device is assigned a unique IP address. Two network devices can communicate over a WAN or public network if they know each other’s IP addresses. A hacker can intercept their communication by changing his machine’s IP address to match that of one of the devices. This method takes special skill and control/modification of network routers, because
- Most network devices/computers will detect the IP address conflict.
- The device whose IP address is spoofed will not receive any traffic because it is being intercepted by the hacker’s computer. The hacker’s computer must pretend to be the legitimate computer and carry on the communication.
- To remain undetected, the hacker will have to intercept the IP traffic through the router and then forward it to the legitimate recipient.
A broadcast IP address is a special type of IP address that exists in every network. The broadcast address allows a device to send a single message to all the IP addresses on that network. One type of broadcast message is known as an “echo”. Devices receiving the “echo” message reply to the sending device.
In a Smurf Attack, the hacker forges the “from” portion of the echo message so that it appears to have come from another system. The device whose address appears in the “from” portion will receive all the replies. Depending on the size of the network, and the number of echo messages sent, that device could receive hundreds or thousands of replies.
There are millions of web servers operating on the internet (which host websites). If a hacker wants to bring down a web server, the hacker would flood that server with massive amounts of traffic. The web server would then be unable to respond to legitimate traffic, and ordinary users would be unable to visit the website. This is known as denial of service. Services other than websites exist on the internet (credit card processing, databases, etc.), and all are vulnerable to DoS.
There are many types of DoS attacks
- SYN flooding. When a user wants to connect to a web server, a three-way handshake (SYN, SYN/ACK, ACK) process occurs between the two computers.
- The user sends a SYN message to the server; the server responds with a SYN/ACK message to the user, and the user responds with an ACK message to the server
- In SYN flooding, the hacker imitates a legitimate user and sends more SYN requests than the web server can handle. The web server responds with the SYN/ACK response, but the hacker does not complete the third part by sending the SYN.
- The server keeps a connection open waiting for an ACK message that never arrives. The server can only keep a limited number of connections open. If all of them are waiting for ACK messages that will never arrive, then the server won’t be able to establish connections with legitimate users
- Fragmenting. When data travels over the internet, the sending computer breaks it down into pieces known as packets. The packets may take different routes to reach their destination. The receiving computer puts the packets back together. The data in each packet should not overlap.
- In a fragmenting attack, the hacker send data to the server, but puts overlapping data into each packet
- The server attempts to put the data back together but can’t. If the operating system isn’t equipped to recognize this attack and discard the bad packets, then it will crash.
How to prevent Denial of Service
- Most DoS attacks are preventable now. Why? A hacker will not have enough bandwidth to bring down a large web service. Major websites such as Google, Facebook, eBay, etc. use distributed server farms consisting of millions of servers, with redundant pathways to the internet. A hacker will not have enough capacity to overload their systems.
- Most enterprise systems contain firewalls that can easily detect and block DoS attacks. If a substantial amount of illegitimate traffic appears to be originating from a single source, it can simply be turned off.
- For a small monthly fee, services such as CloudFlare offer large-scale cloud-based firewalls to protect smaller websites from DoS attacks (which they normally could not afford).
- A company should never be a victim to the same attack twice. After the first attack, they must investigate and configure their systems so that it never happens again. The most common types of attacks are well documented, and systems are available to prevent them.
Distributed Denial of Service was invented after DoS stopped working (due to improvements in internet infrastructure).
With DDoS, a hacker infects thousands (or hundreds of thousands) of computers (or other IP devices such as cameras) and uses all of them to send traffic to a web server that he wants to crash. These computers are known as bots and together they form a botnet. Since the traffic appears legitimate (and is in fact originating from hundreds of thousands of different sources, in different geographic locations, with different internet service providers, and different computer types), it is difficult to filter or prevent.
The botnet operator will continue to acquire additional bots, to grow his botnet. The operator might lease his network of bots to a person or organization that wants to bring down a website (for revenge, competition, or other reasons).
An Amplified DDoS attack happens when the hacker’s request is much smaller than the victim’s response. For example, the hacker is requesting a copy of a webpage. The request may be a few bytes in size, but the response is the entire webpage, which may be several megabytes. If the hacker has a way to divert the response to another destination, he can launch an attack with little bandwidth.
A Reflective DDoS attack is when the hacker forges the destination address of his request to that of the victim. The victim server sees requests for web pages that are coming from itself. Therefore, the victim begins sending traffic back to itself.
In a Man-in-the-Middle attack, a hacker inserts himself between the sender and recipient of an electronic communication. Keep in mind that more than 60% of internet traffic is machine generated (one computer talking to another with no human interaction).
Consider that Alice and Bob are two hypothetical internet users having an encrypted conversation. They could be two humans, or it could be that Alice is an online banking user and Bob is the bank. The purpose of the communication is irrelevant. Consider that the hacker, Eve, wants to spy on them.
Alice and Bob’s messages pass through a central server. Depending on Alice and Bob’s geographical locations, the messages may pass through many servers, routers, switches, fiber optic cables, and copper lines. The internet is fragmented, and different parts are owned by different companies. If Alice is in New York and Bob is in Los Angeles, the traffic must pass through many states, and many internet service providers.
- If the traffic between Alice and Bob is unencrypted, and Eve can obtain access to one of the servers, routers, switches, or physical connections, then Eve can spy on the conversation.
- If the traffic is unencrypted, but Alice does not have access to one of the servers that the connection travels through, Eve could trick Alice into sending messages addressed to Bob to her instead (by corrupting/modifying Alice’s address book). Eve would do the same to Bob. In Alice’s address book, Eve replaces Bob’s address with her own. In Bob’s address book, Alice replaces Alice’s address with her own. Alice sends messages to Eve thinking she is sending them to Bob, and Bob sends messages to Eve thinking he is sending them to Alice. Now Eve can read Alice’s messages and forward them to Bob. Eve can also read Bob’s messages and forward them to Alice. Neither Alice nor Bob is aware that Eve is reading their communications.
- If the communication is encrypted and uses public key cryptography (such as Apple iMessage), a man-in-the-middle attack is more difficult. Users encrypt messages with public keys (which they obtain from a central directory). If Alice wants to send a message to Bob, she obtains Bob’s public key from Apple, encrypts the message, and sends it to Bob. Bob uses his private key (which only he knows) to decrypt the message. If Eve can intercept the message, she could perform a man-in-the-middle attack
- We will discuss public key cryptography in more depth later, but in general consider this
- A private key can only decrypt a message. A user keeps his private key secret.
- The user generates a public key from his private key. He gives the public key to everybody who wants to send him a message. The public key can only encrypt a message.
- Eve generates her own public and private keys
- She hacks into the central directory and changes Bob’s public key to her own
- Alice decides to send a message to Bob. She checks the directory for Bob’s public key, and receives what she thinks is Bob’s public key (but is in fact Eve’s public key)
- Alice sends the message to Eve (thinking she is sending it to Bob)
- Eve decrypts the message, reads it, and then encrypts it with Bob’s public key
- Eve sends the message to Bob
- Bob receives the message, thinking it came from Alice and decrypts it with his own private key
- Eve does the same thing with Alice’s public key so that she can intercept messages that Bob is sending to Alice
- We will discuss public key cryptography in more depth later, but in general consider this
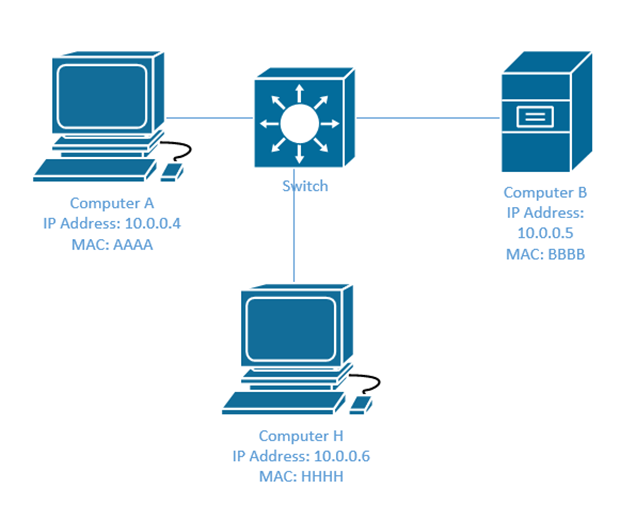
A hacker can use a Man-in-the-Middle attack to poison the ARP. The hacker must send the last ARP message to be successful.
Computer A has IP address 10.0.0.4 and MAC address AAAA. It wants to learn the MAC address of Computer B, so it sends an ARP Request, which is broadcast over the entire network. The ARP message says, “if you’re IP address is 10.0.0.5, what is your MAC address”. The hacker’s computer is on the bottom and has an IP address of 10.0.0.6 and a MAC address of HHHH.
Computer B will respond to tell Computer A that it’s IP address is 10.0.0.5, but Computer H (the hacker’s computer) will respond afterwards to tell it that the MAC address is HHHH. Computer B won’t know that Computer H did this. Computer A will address traffic intended for Computer B to Computer H.
If a hacker wants to identify areas to attack, he can perform a reconnaissance attack. Many legitimate tools such as nslookup and ping can also be used by a hacker to discover open ports and other vulnerable systems. Once a hacker has discovered the vulnerabilities, he can plan a further attack.
What is a buffer? The buffer is kind of like a lineup at airport security. The flow of passengers is not steady. When there are more passengers than security guards, a long lineup develops. If the airport doesn’t have enough room to hold all the passengers, they might have to wait outside.
The buffer is the same. Consider a web server or other computing device. Information is coming in over a wire. Sometimes the information is coming in quickly, and sometimes it is coming in slowly. The server must take each piece of data and process it somewhere. When the levels of traffic are high, the server can’t process all of it in real time. Thus, all data first enters a buffer, where it lines up to be processed. The server takes data from the buffer at a steady rate.
- For example, the traffic ranges from 0.5GB/s to 2GB/s
- The server can process data at 1GB/s
- If the traffic is 1GB/s or less, the server can process the traffic in real time. The traffic passes through the buffer but doesn’t spend any time there.
- If the traffic is more than 1GB/s, the server can’t process the traffic in real time. The buffer starts to fill up.
The buffer has limited capacity. If the buffer fills up, then it should reject additional data. For example, if the buffer has a capacity of 10GB, and data comes in at a rate of 2GB/s, but the computer can only process 1GB/s, then after 10 seconds, the buffer will be full.
The buffer may be designed to hold specific sizes of data. For example, a buffer may be designed to store IP addresses. Recall that an IP address is 12 digits. If a hacker sends a piece of data that is larger than what the buffer expects, a buffer overflow results. For example, if the IP address is 12 digits, and the hacker sends 14 digits, a buffer overflow could result.
In 2014, a major exploit known as Heartbleed caused security vulnerabilities across millions of websites, including Facebook, Google, and Revenue Canada. How did it work?
- Websites encrypt their data with an algorithm known as SSL
- A developer created an app called OpenSSL, which makes it easy for web developers to implement SSL in their website, using minimal code
- Millions of websites, including millions of the worlds largest websites used the OpenSSL app
- When a user visits a website, a connection is created. The user’s computer and the web server keep the connection open for as long as necessary (but for no longer than necessary). To preserve resources, the server closes the connection when it is no longer required. It checks if the user is still present through a method known as a “heartbeat”, which is the electronic equivalent of asking the user “are you there?” ever minute. If the user says “yes”, the connection stays open. If the user doesn’t reply, the server closes the connection.
- Every minute, the user’s computer sends a small random amount of data to the web server. The user’s computer sends the web server the length of the data as well.
- For example, the user’s computer might send “sdkjfasfjksdlfskldflskdf” length:24
- The web server sends the data back. Thus, the web server and the user’s computer know that both are still online and agree to keep the connection active.
- In fact, the server stores the data in a buffer and gives it an address (the address is the spot where the data starts). To return the data to the user, the server locates the data at that address, and counts the number of spaces based on the length it was provided. If the data’s address starts at position 40 in the buffer, then the server will start reading at position and count another 23 position. Thus, the server will return the data from position 40 to position 63.
- A hacker found out that OpenSSL didn’t verify the accuracy the length that the user’s computer provided.
- Thus, a hacker could send a small amount of data such as “aaa” and a large length such as length:4523
- The server would store “aaa” in memory and then send back 4523 bits of data, starting with “aaa”. If aaa started at position 40, the server would reply with the data from position 40 to position 4562. What kind of data is stored in the other positions? Anything is possible.
- If the hacker repeated these steps, eventually he would receive most of the contents of the server’s memory, which could include encryption keys and private banking information.
- This bug could have been easily prevented with a few lines of code to verify the length of the data.
- Once discovered, it was quickly patched. But hackers had been using the security hole to steal data undetected for over two years.
How to prevent
- Proper code and error handling in programs. The buffer overflow happens because the computer receives data in an unexpected format and doesn’t know what to do. Buffer overflows can be prevented by writing good code that checks for errors and refuses to accept data that does not meet the required format. A program shouldn’t crash when it receives invalid data; it should simply reject it.
- The correct data has an expected format (length, character type, contents, format, etc.)
- In pseudocode, write an “if” statement. If the data doesn’t match the expected format, then reject the data.
Malware is any type of malicious application. There are many types of malware.
A virus is an unauthorized program that causes undesired activity. A virus is not a standalone program, but instead it latches on to another legitimate program. When the legitimate program runs, so does the virus.
Viruses typically infect executable programs such as programs with extensions of .exe. Viruses can also infect documents, such as Microsoft Word documents or Microsoft Excel spreadsheets. These are known as macro viruses. Current versions of Microsoft Office disable macros by default (a user can open a Microsoft Office document file without allowing the macro to execute).
Viruses can enter automatically through backdoors. A user could inadvertently introduce a virus by clicking on attachments or downloading files from the internet.
The damage that a virus does is called the payload. Viruses can cause a wide range of effects from being simply a nuisance to deleting files. Viruses that infect industrial control systems can cause millions of dollars in damage. Viruses that infect medical equipment can put lives at risk.
A virus can be detected and prevented using an antivirus program. An antivirus program has two methods of detecting viruses
- Definitions: A definition is a specific “fingerprint” of the virus. An antivirus program may contain hundreds of thousands of virus definitions. It scans each new file introduced into the computer against the definitions. If the attributes of a file match a definition, then the antivirus program knows that it has located a virus (and knows which virus it has located).
To develop the antivirus definitions, the antivirus software manufacturer must first obtain copies of the virus and create the definition. That means that some computers have already been infected with the virus by the time the definition has been created. Thus, definitions do not provide complete protection against viruses.
A polymorphic virus is one that attempts to change its code. Each time the virus runs, the code changes slightly, but the damage that it causes remains the same. A polymorphic virus attempts to hide from antivirus definitions. - Heuristics. A heuristic is a type of artificial intelligence. It allows the antivirus program to determine whether a specific program is legitimate or not, based on its behavior. For example, a program that attempts to modify critical system files is likely not legitimate.
The latest generation antivirus programs share data with the cloud. For example, Norton Antivirus automatically collects data regarding suspicious applications from users. This data is sent to a response center for further analysis. Norton Antivirus then updates all user programs with the results. By sharing data with the cloud, antivirus programs can detect viruses faster.
The most famous computer viruses have been
- ILOVEYOU. Released in 2000, ILOVEYOU was transmitted via e-mail with a subject line of “I love you”. It overwrote system files and personal files, before spreading through e-mail. It caused $15 billion in damage.
- MyDoom. Similar, to ILOVEYOU, MyDoom spread via e-mail in 2004. It is estimated that 25% of all e-mails sent in 2004 were infected with MyDoom. It caused $38 billion in damage.
- Stuxnet. Stuxnet is a special kind of virus because it infected the firmware of a USB drive. The firmware of a USB drive is not typically accessible to the computer or to an antivirus program – it’s considered “read only” memory and allows the USB drive to read/write data from/to the computer.
The Stuxnet virus contained a second virus inside of it. When the USB drive was inserted into a PLC (an industrial control system), the second virus infected the PLC. Stuxnet only infected Siemens S7 PLCs.
Stuxnet was used to infect industrial control systems that were “air gapped” (not connected to the internet or to any network).
Stuxnet was unusual because- It took advantage of multiple zero-day exploits (security holes that are unknown to the software manufacturers). A zero-day exploit is considered valuable to a virus manufacturer/hacker, and to use several in the same virus is highly unusual. Zero-day exploits are quickly patched by manufacturers once discovered and can’t be reused. A zero-day exploit could be worth up to a million dollars. To use several million dollars worth of zero-day exploits in a virus that brings the creator no financial reward is highly unusual.
- It limited its infection to only specific types of computers and PLCs. Most virus manufacturers do not want to limit the damage that they cause.
- It is estimated that Stuxnet took between three man-years and fifteen man-years to prepare. Development of Stuxnet required advanced knowledge of the Windows operating system, USB firmware, and Siemens PLCs.
Crypto-malware and ransomware are closely related. Crypto-malware is a type of virus or malicious program that encrypts data on a computer.
The malware can be introduced through e-mail or downloaded files. The malware usually encrypts user documents, videos, photos, and music. It does not usually encrypt system files.
The distribution of crypto-malware is usually automated, although people or organizations can be specifically targeted. It should be noted that after the crypto-malware has infected the computer, then the author is able to view the contents of the computer. At that point, he can make an assessment as to how high of a ransom to charge. For example, if an ordinary person was targeted, the ransom might be low, but if a hospital was targeted, then the ransom might be high.
After infection, the computer operates as normal, but the user is provided with a message that their files have been encrypted. The malware usually instructs the user to pay a ransom to unlock the files. The ransom must typically be paid in bitcoin.
There are two types of crypto-malware
- Crypto-malware that pretend to encrypt the files. They change the file extension to something random, but do not encrypt the file. When the extension is changed back to the original, the files revert to normal. These forms of crypto-malware are extremely rare.
- Crypto-malware that encrypt the files. After the files are encrypted, the key is sent to a central server. The user receives the decryption key after paying the ransom. Some forms of crypto-malware do not provide the option to decrypt the files, either because they are misconfigured or because the intention is to prevent a user from accessing his files.
Ransomware is an extension of crypto-malware, in that it instructs the user to pay a ransom in exchange for unlocking the files.
Typically, the user is instructed to visit a TOR website, where they are provided further instructions. TOR websites are generally able to hide their location, although law enforcement agencies have developed methods to identify them. The user is instructed to pay the ransom with cryptocurrency (untraceable currency) such as bitcoin.
In most cases, the hackers provide the victim with the tool to decrypt their files upon receipt of payment. In some cases, the hackers do not.
The ransom amounts have ranged from the equivalent of $500 to $20,000 depending on the person or organization that was affected. Many organizations pay the ransom and don’t publicly admit that they have been hacked.
How to prevent ransomware
- Proper user education to teach users how to identify potential ransomware delivered via e-mail, and to not open unusual attachments.
- Block e-mail attachments that contain macro-enabled Microsoft Word and Excel documents.
- Regularly install Windows operating system security updates
How to defeat ransomware once infected
- Attempt to restore data from backup or from the Volume Shadow Copy. This only works if the organization has backed up their data, and only the data that was backed up can be restored. This is not effective against newer versions of ransomware, which delete the Volume Shadow Copy.
- Attempt to decrypt the ransomware. Police forces in the EU have been able to provide victims with assistance in decrypting some forms of ransomware. Some versions of ransomware use weak encryption that can be broken through brute force or other techniques.
- Pay the ransom. In earlier cases, it was almost certain that the hackers would automatically (or manually) provide the decryption key upon payment of the ransom. In more recent cases, this is not guaranteed because there are many copycat ransomware viruses created by people with very little knowledge or infrastructure. Ransomware developers have franchised their operation to “script kiddies” who are simply distributing the ransomware and collecting payments. There are also versions of ransomware that have been put out by nation-states to cause political disruption; this type of malware only destroys data but is disguised as ransomware.
Notable infections
- In 2019, Jackson County, Georgia paid $400,000 to remove ransomware from their computers.
- University of Calgary paid $20,000 to decrypt computers infected by ransomware in 2017. The FBI later charged two people in Iran with spreading the virus, which infected computers at health care providers and other organizations.
Notable ransomware
- CryptoLocker was transmitted over e-mail as a ZIP file. Inside the e-mail was an executable disguised as a PDF. The decryption key was sent to a remote server. A victim could pay a ransom and receive a decryption key automatically. The creators of CrytoLocker made an estimated $27 million. In 2014, security firm FireEye was able to obtain the database of decryption keys, allowing victims to decrypt their files for free.
- WannaCry took advantage of a zero-day exploit in the Windows Server Message Block. WannaCry infected computers that had not patched the Windows Server Message Block vulnerability. The average ransom amount was $600. Over 200,000 computers were infected, with losses estimated at over $4 billion.
- Unlike other forms of ransomware, Petya encrypted the master boot record of a Windows computer. This caused the entire computer hard drive to be encrypted. Another version, known as NotPetya was targeted towards Ukrainian government entities and critical infrastructure. NotPetya quickly spread to other computers worldwide and could not be decrypted. It is believed that NotPetya was created by the Russian government.
The difference between a worm and a virus is that the worm replicates by itself, whereas the virus must attach itself to a legitimate file. The virus only runs when the legitimate file runs.
Worms can generally spread over a network from computer to computer, by themselves. They take advantage of security holes.
Examples of worms
- SQL Slammer took advantage of a buffer overflow bug in Microsoft SQL Server. The worm would randomly generate IP addresses and then send itself to those IP addresses. If the IP addresses belonged to computers that were running an unpatched version of SQL Server, then the worm would be successful in infecting them. The worm caused many internet routers to crash, and reboot. Each time the routers rebooted, they would resend routing updates to each other, which would cause internet traffic congestion. SQL Slammer was exceptional in that it fit inside a single data packet.
A trojan is a legitimate program that hides an illegitimate program. A user must install the trojan and/or give it permission before it can take effect. Trojan is named after the Trojan horse.
Trojans can hide in many programs including toolbars, screensavers, games, and other applications.
Examples of Trojans
- FinFisher (FinSpy), which is developed by Lench IT Solutions plc. This trojan is used to infect Windows computers and all brands of phones. It travels through e-mail, links, and security flaws in popular programs. Many antivirus programs are unable to detect it.
FinFisher is sold to law enforcement agencies and dictatorships, some of which are accused of numerous human rights violations.
A rootkit provides unauthorized administrative level access to a computer by changing its operating system and attempting to bypass its security functions.
There are five types of rootkits
- Firmware. A firmware rootkit hides inside the device firmware (such as the BIOS, video card controller, router, network card, or hard drive controller). The device firmware is not typically scanned by (and is out of reach of) antivirus programs. While manufacturers such as HP have introduced BIOS integrity features that check for changes to the BIOS firmware, rootkits can infect other components such as the graphics card or hard drive.
- Virtual. A virtual rootkit is also known as a hypervisor rootkit. It operates between the processor and the operating system. It intercepts calls made by the operating system, like a “man-in-the-middle” attack. The result is that the processor believes that it is talking to the operating system and the operating system believes that it is taking to the processor, but, both are talking to the rootkit. The rootkit sends everything it learns to a central server.
- Kernel. A kernel rootkit runs on a computer with the highest privileges (the same privileges as the operating system) by replacing parts of the operating system core and device drivers. A kernel rootkit can’t be detected by an antivirus program because the rootkit is acting like part of the legitimate operating system.
- Library. A library level rootkit replaces legitimate operating system DLLs with fake ones. A library is a set of code/functions that an application can reference (a software developer will include different DLLs with their application so that they don’t have to rewrite thousands of lines of code). When an application references code in an infected DLL, the rootkit will also run.
- Application Level. An application level rootkit replaces application files with fake versions. The application may need to run at an elevated level in order to cause damage.
Examples of rootkits
- LoJack. LoJack is a legitimate rootkit that comes preinstalled in the BIOS of some laptops. If the laptop is lost or stolen and later connected to the internet, LoJack will report the location of the laptop to a server. LoJack is designed to remain on the laptop even if its hard disk drive is erased or replaced.
- Sony BMG. In 2005, Sony installed a rootkit known as XCP (Extended Copy Protection) on music CD’s that it released. When users attempted to play the CD’s through their computer, the rootkit created security vulnerabilities. The intention of the rootkit was to prevent people from copying music off the CD’s, but the rootkit created security holes and hid in the background.
Sony was forced to recall all unsold music CDs and faced multiple class-action lawsuits.
A keylogger records each key that a user presses. It may also take screenshots, activate the webcam, or activate the microphone without the knowledge or consent of the user.
The keylogger reports all data back to a central source or records the data on the computer for further retrieval. Data may be sent via
- FTP
- Wireless/Bluetooth to a nearby receiver
A keylogger may have legitimate purposes if installed by an employer or law enforcement agency. Some antivirus programs will detect keyloggers created by law enforcement and some will deliberately ignore them.
A keylogger may be used to invade the privacy of another person (stalking) or it may be used for financial gain (the logged data is analysed to obtain online banking passwords, e-mail passwords, etc.).
The keylogger may be introduced into a system through another type of malware such as a virus or trojan.
Whether the keylogger can be detected by an antivirus program depends on where it runs. Keyloggers that run in the operating system kernel or through a hypervisor may be undetectable.
Keyloggers can also be hardware-based
- Keyboard keylogger device (USB device that sits between the keyboard cable and the computer). A keyboard’s circuitry can be covertly modified to include a keylogger.
- Wireless keyboard sniffer (device that can intercept signals between a wireless keyboard and the dongle; this device functions when the connection is not encrypted or where the encryption method can be easily broken)
How to prevent keyloggers
- It is difficult, if not impossible to detect a hardware based keylogger, especially one that is embedded into the device circuitry. Keeping computer hardware physically secure is the best defense. In addition, the use of multi-factor authentication methods can keep accounts secure even when the usernames and passwords are compromised.
- Most software-based keyloggers are detectable by antivirus programs. Some software-based keyloggers that take advantage of zero-day exploits or that operate on the firmware, kernel, or hypervisor level cannot be detected.
Adware is software that shows advertisements. The advertisements may appear as pop-ups, videos, or audio. Adware may be included in legitimate software programs such as games, music applications, or other applications. Typically, adware is bundled with low-quality applications. The advertisements are also of low quality as most legitimate advertisers do not want to be associated with this type of exploitation.
Adware can also be installed without the user’s consent when introduced as part of a computer virus or trojan.
Adware can hijack legitimate website advertisements. When a user visits a legitimate website, the adware swaps advertisements placed by the website owner with advertisements sold by the adware publisher. Thus, the revenue from the advertisements is diverted to the adware publisher without the knowledge of the user or website owner.
It may be difficult or impossible to remove adware. Adware may spy on a user’s activity or browsing history. The adware publisher may sell this data to market research firms or use it to show the user more relevant advertising.
It is illegal to install or distribute adware without the consent of the user. In addition, the user must have an opportunity to remove the adware. There is no specific anti-adware law, but Section 5 of the Federal Trade Commission Act prohibits “unfair or deceptive acts”. The Federal Trade Commission (FTC) is empowered to commence civil actions against publishers who distribute adware.
Spyware is software that spies on a user’s activity. Spyware can include keyloggers but can also include components that take screenshots or videos, activate the webcam or microphone, and/or copy files.
The distribution of spyware can be prosecuted under the Computer Fraud & Abuse Act, as further discussed in this book. It can be further prosecuted under harassment and stalking laws if the behavior amounts to such.
A logic bomb is a program that is installed by a legitimate user. The logic bomb appears to be legitimate. The logic bomb remains dormant until activated by a specific date/time or event. In Windows, the logic bomb can be programmed to activate in the Event Scheduler.
The logic bomb can steal data, delete data, or cause other harmful actions. Logic bombs are commonly installed by disgruntled system administrators. After the system administrator is fired or quits, the logic bomb activates and damages the company’s systems.
Social engineering is the attempt to use psychological methods to manipulate individuals into providing confidential information or access to systems.
Unlike malware, social engineering relies on human emotion
- Wanting to be liked
- Fear
- Wanting to help
- Intimidation
- Familiarity
- Hostility
A good book on social engineering is Social Engineering: The Art of Human Hacking by Christopher Hadnagy.
Why do social engineering attempts work? There are many reasons.
- Authority
- The person on the other end of the phone call/in person acts with authority. People are afraid to challenge those who appear to be in a position of authority (such as members of senior management).
- Authority can be established by confidence, tone of voice, clothing, and/or uniforms.
- People are afraid to challenge authority because of perceived negative consequences (getting fired)
- The consequences do not have to be explicitly stated by the thief. They can be implied, or the user might simply assume what they are based on the alleged authority.
- Social engineering authority attacks can be prevented by enforcing policy against all users, regardless of their position. The company must create a culture where verifying the identity of another person is encouraged, regardless of that person’s position.
- For example, the thief could pretend to be a member of senior management and convince the victim that she could lose her job if she does not comply. The thief could demand that the victim provide him with corporate financial information, or wire money to a third party.
- Intimidation
- Intimidation uses the threat or idea of negative consequences if the person fails to comply.
- The thief does not have to make any direct threats, but instead may cause the victim to believe that negative consequences will occur (or the victim may assume that negative consequences will occur if they fail to comply).
- For example, the thief could pretend to be a police officer and convince the victim that she will be arrested if she does not comply. The thief demands that the victim disclose sensitive data relevant to an investigation.
- Consensus
- Consensus involves a group-decision.
- If a social engineer is unable to convince a specific person to perform an action, he could attempt to convince others in that person’s social circle. Those other people could convince the victim to proceed.
- For example, the thief could convince the victim that her co-workers completed the same action.
- Scarcity
- Scarcity means that something is unavailable or in limited supply.
- If the victim values something that is scarce, they may forgo normal procedures and fall into the trap to obtain that item.
- For example, the victim wants a rare (sold out) toy at Christmas time. The thief convinces her that he can supply the toy if she provides him with her credit card/banking information (which he uses fraudulently). The victim never receives the toy.
- Familiarity
- The victim feels familiar with the situation and proceeds because nothing seems out of place.
- The thief can convince the victim to focus on ideas that are familiar, by dropping names, projects, or other tasks into the conversation.
- Although the victim does not know the thief, she is led to believe that he is a legitimate co-worker.
- Trust
- The victim trusts the thief and proceeds with their own free will.
- The victim believes that the person they are talking to or the site that they have visited is legitimate.
- The thief may take time to build this trust, especially with a high-value target. The greater the victim trusts the thief, the more the victim will be willing to do.
- Urgency
- Urgency is like scarcity
- Urgency builds on the idea that there is a limited time to act.
- People hate losing money more than they hate not making money.
- For example, the victim could be told that money is about to be withdrawn from their bank account and they only have a few minutes to stop it (by providing their banking information to the thief). Normally, the victim would take their time to check that the person they are speaking with is legitimate but bypasses these risk controls because of the urgency.
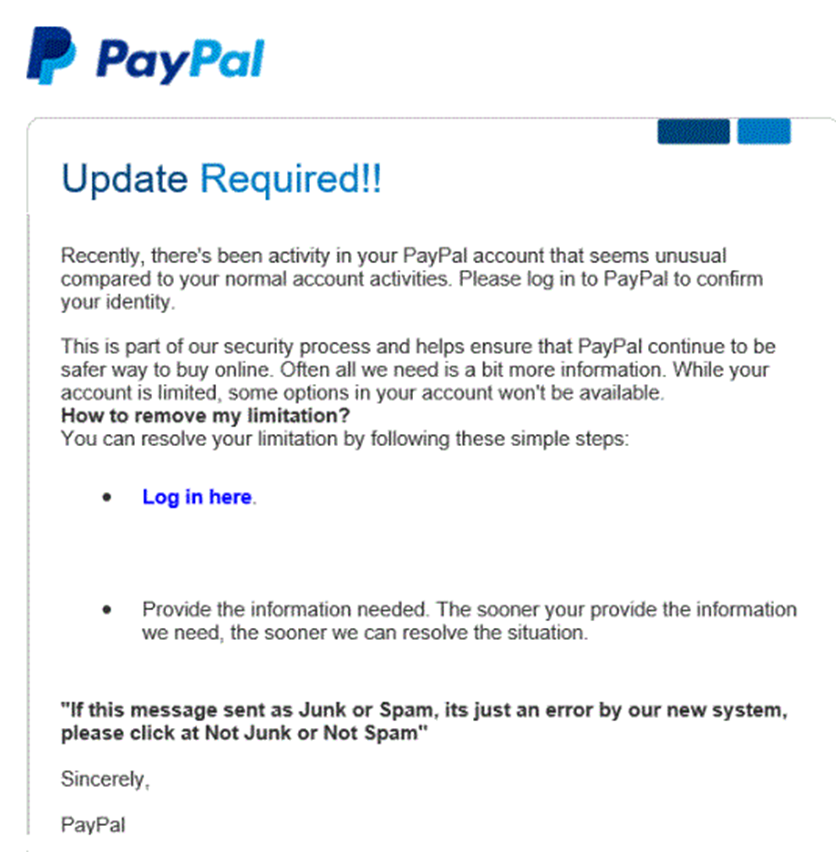
Phishing is the attempt to obtain sensitive data by pretending to be a trusted entity. Phishing usually occurs through e-mail or telephone. Phishing is usually sent as a mass e-mail to thousands or millions of people.
Typically, a user will receive an e-mail asking them to sign in to their bank account or other account (PayPal, eBay, Amazon). The e-mail is fake, and the website that the e-mail leads to is fake (but appears to be real).
Typical phishing e-mails will say
- Your account has been compromised and you must log in to correct the issue
- Your account will be suspended if you don’t log in
- You have received a large payment (Interac eTransfer) and you must log in to accept the money
The hacker may register a domain that looks like the legitimate one. For example, the user may register www.paypa1.com instead of www.paypal.com. Or the hacker may register a domain that is completely unrelated to the original website and attach a subdomain that looks like the legitimate site. For example, the hacker registers fakewebsite.com and attaches the “www.paypal” subdomain to it, making www.paypal.com.fakewebsite.com. The users will see the first part of the URL “www.paypal.com” and think they are on a legitimate site, even though the user’s browser went to fakewebsite.com.
How do we prevent phishing?
- Proper user education to identify suspicious e-mails.
- Knowledge that legitimate e-mails from banks and other sites will contain the user’s full name while phishing e-mails will not (unless the sender has access to the user’s data)
- Phishing e-mails and/or websites may (but not always) contain poor grammar or spelling
- Phishing websites will not contain the correct URL. Users should always check that they have visited the correct URL.
- Automated systems that detect and filter phishing e-mails. These systems are built into most web browsers and e-mail systems and verify that the e-mails originated from legitimate sources and that the websites are legitimate.
Spear Phishing is like phishing, but it targets specific groups or people. The more precise the targeting, the higher the response rate.
A normal phishing attack could target millions of users. For example,
- A hacker could send a fake e-mail appearing to be from Bank of America to 1,000,000 e-mail addresses
- From those 1,000,000 addresses, only 250,000 might work
- The SPAM filter would block 200,000 from those 250,000
- From the 50,000 only 10,000 might have accounts at Bank of America
- 80% of those users might be smart enough to detect the phishing scam, in which case only 2,000 people respond
- The attack is shut down early on, and many users are unable to respond, so the hackers only collect data from 500 users
- The success rate is about 0.005%. Although it is low, the return on investment might be high. It may cost the hackers a few hundred dollars out the e-mail, but they might be able to collect at least $100 from each user (for a total of $50,000).
In spear phishing, the hackers identify specific customers of Bank of America for example. They may use a list stolen from the bank. The hackers customize the e-mail to include the name and other personally identifying information of each recipient. As a result, the SPAM filter will be less likely to identify the e-mail as SPAM, and the user will be more likely to respond.
Whaling is like Phishing, but targets high-value individuals such as celebrities, CEOs or other executives. Whaling is specifically targeted to the high-value individual. Whaling takes more effort to execute, but the response rate is higher, and the amount of money stolen from each user is higher. Many high-net worth individuals have access to credit cards with high limits.
Another scheme involves a scammer visiting a store such as Best Buy and attempting to illegally purchase expensive electronics in the name of a celebrity on credit. The scammer disappears with the electronics and the store is never paid. The store should have verified that the buyer legitimately represents the celebrity.
How do we prevent whaling?
- Proper user education
- 100% identity verification of the person who is seeking information.
- A high-net worth individual should understand that he is at much higher risk of exploitation either through fraud or extortion schemes. This person should employ people who specialize in detecting and preventing these threats.
Vishing or VoIP Phishing and Smishing or SMS Phishing are forms of phishing that use a VoIP phone or SMS messages. Smishing is particularly dangerous, because although we can block many types of malicious e-mails, it is difficult to block SMS messages – they contain very little metadata (except for the date and sender, all SMS messages look the same).
Pharming is a form of phishing where we redirect a legitimate website’s traffic to an illegitimate website.
In a watering hole attack, a thief plants a form of malware on a frequently visited website. The users visit the website and download the malware.
A watering hole attack typically takes advantage of a zero-day exploit. It allows malware to download in the background without any indication to the user.
How to prevent
- Proper antivirus can prevent many watering hole attacks
- Website operators should ensure that their servers and code are up to date
- Watering hole attacks that take advantage of zero-day exploits cannot be prevented
In cross-site scripting, a user includes script as part of their input in a web form or link. There are three types
- Non-persistent XSS attack, where the script is executed by the web server immediately and sent back to the browser
- For example, a hacker sends a user a link to a legitimate online banking website, but the link includes some code that executes (through the website) in the user’s browser. The script copies the user’s login credentials and sends them to the hacker.
- Persistent XSS attack, where the script is stored by the web server and executed against others
- For example, a hacker posts a YouTube comment and includes some HTML (which includes links and photographs to an ecommerce site). The HTML executes in each visitor’s web browser, and all visitors see the comment (including the links and photographs). This is unlikely to happen on YouTube because data is sanitized, but it is certainly possible on other websites.
- DOM-based XSS attack, where the script is executed by the browser
How to prevent
- Proper input validation in web forms both on the web browser side and on the server side
- Remove or filter all script characters from web forms, including “<”, “;”, and “|”
- Use anti-XSS libraries such as ANTIXSS
- Use Content Security Policy in the website
In cryptography the data is encrypted. Hackers try to decrypt it. There are many ways, but all cryptographic attacks can be prevented. Some of the attacks include
- Birthday. Consider a set of values (not necessarily unique values), . In any set , the possibility that at least two values are identical is . If we have a set of two values, then the possibility that they are identical is . As the set grows, the possibility that two entries will be identical also grows. This idea came from the fact that in a room of 30 people, there is at least a 50% chance that two of them share a birthday.
- Known Plain Text/Cipher Text. If the hacker can intercept a portion of the plain text communication and the corresponding portion of the cipher, he can use cryptanalysis to decrypt the algorithm. The hacker does not require the entire communication, only a portion. Good encryption algorithms can mitigate this threat because they use large keys.
- Rainbow Tables. Recall that it is bad security practice to store passwords in plain text. Passwords are typically hashed, and the hash is stored (the hash is not reversible).
But a hacker could generate a dictionary of passwords (common and uncommon) and calculate the corresponding hash for each one. This dictionary is known as a rainbow table. The hacker could then steal a hash and look up the corresponding password for each one.
Rainbow tables are readily available on the internet for passwords up to eight characters (every possible combination!) and rainbow tables of even longer passwords can be computed.
To prevent the use of rainbow table attacks, modern password hash functions incorporate a ‘salt’. The salt is a random set of characters appended to the end of each password before the hash is calculated. The hash and the salt are stored in plain text. If the hash database is compromised, the hacker would have to regenerate each rainbow table incorporating the salt into every password to make any sense of it. This would be practically impossible. - Dictionary. A Dictionary attack uses a list of predetermined passwords and brute force to guess the password. The dictionary could consist of common words in the English language, especially common passwords such as “password”, “12345678”, and “abcd”.
A hacker could create a custom dictionary based on the user account that he is trying to hack into. For example, the dictionary could be customized to include the names of the user’s children, pets, vehicles, etc..
Many organizations force users to choose complex passwords. Password complexity could include- Not reusing the same password
- Including upper case letters, lower case letters, numbers, and special characters
- Ensuring that the password meets a minimum length
- Not using a person’s name, address, or username in the password
Yet, it is still possible to create a custom dictionary based on the password complexity requirements. For example, if the user’s password was ‘donkey’, then a complicated password might be ‘D0nkey!’. Users tend to substitute @ for a, 0 for o, 1 for l, and so forth in a predictable manner.
A dictionary attack can be prevented by limiting the amount of password attempts a user has before his account is locked out. Of course, the dictionary attack could occur offline, or the hacker may have a way to bypass the incorrect password attempt count.
- Brute Force. A brute force attack is like a dictionary attack, except that the system attempts every password combination possible (based on the character set), starting from the letter a and working its way up until the password is guessed. For example, the system will guess the password ‘sdfsfgdgsdfsdfd’, and then the next password would be ‘sdfsfgdgsdfsdfe’
The length of time for a brute force attack to be successful depends on the computing power available (how many passwords can be attempted every second) and the length of the password (how many passwords need to be attempted).
An online brute force attack is when the brute force occurs against a live computer. For example, consider Active Directory, a Microsoft system that stores user accounts on a central server. When a user attempts to log in to an Active Directory-based computer, the computer validates the login credentials with the server. On a successful login, the computer caches the correct credentials on the local computer. If the computer is later offline (or off the local network), the user can still log in (the computer validates the login with the cached credentials).- In an online attack, the hacker would brute force the computer’s login while it is connected to the Active Directory server. This attack would likely be unsuccessful because the server would notice the incorrect logins and disable the account.
- In an offline attack, the hacker would brute force the computer’s login while it is not connected to the Active Directory server. This attack may or may not be successful depending on the length and complexity of the password.
How to prevent
- Offline attacks can’t be prevented. Where possible, secure equipment so that it is not stolen. Stolen equipment is more susceptible to offline attacks.
- Enforce stronger password requirements (including special characters, numbers, upper/lower case letters).
- Enforce a timer that delays the entry of passwords. This can be accomplished at the software or hardware level, by hashing the password multiple times.
- Offline data can be encrypted with a strong algorithm that takes several seconds to validate the password. This would be a minor inconvenience to a user entering an incorrect password, but would substantially slow down a brute force attack.
