5.2 Describe security program elements (user awareness, training, and physical access control)
Users are not experts at security and hackers are always looking for new ways to exploit them. We need to train people so that they can recognize and report security threats.
The best security program has
- User Awareness – We make users aware that threats exist so that they can be vigilant.
- User Training – We teach users how to formally detect threats. A user training policy should apply to any user who has access to our network. Users must be encouraged to report potential security threats.
One new way that organizations train users is to send them fake phishing e-mails and see if they respond or provide their credentials. If they do, then they are warned that they clicked on a link that could have come from a hacker, so that they learn how to recognize similar threats in the future.
Even the most highly trained security analysts are vulnerable to phishing attacks, especially when the attacker is sophisticated. We are all human, and social engineering is designed to work on weak human emotions. - Physical Access Control – We keep people out of the places that they shouldn’t be. Keeping network and server infrastructure physically secure is important because a person with physical access can
- Physically damage the equipment by powering it off or removing the hard disk drives
- Gain console access to network equipment. Most Cisco switches and routers can be physically reset by a user with physical access, regardless of the type of security on the device.
- Connect unauthorized devices such as USB drives to servers, routers, and switches.
With a physical access control system, we use an electronic system to keep track of who entered, where they entered, and what time they entered. We can restrict the areas that each person can access, and we can restrict the time of day that they can access an area.
Tailgaiting is an attempt to obtain unauthorized access to a physical facility.
Many offices, industrial facilities, and data centers are controlled via electronic proximity card and/or biometric locks. When a legitimate user unlocks an entrance with their access card and/or biometric lock, an intruder can follow them into the building. Tailgaiting works because
- A person might hold the door open for a person who is walking behind him (doing otherwise might be considered rude)
- A person might not wait to verify that the door closed and locked behind him, and another person might follow him. The door lock might not work properly, in which case the door does not fully close.
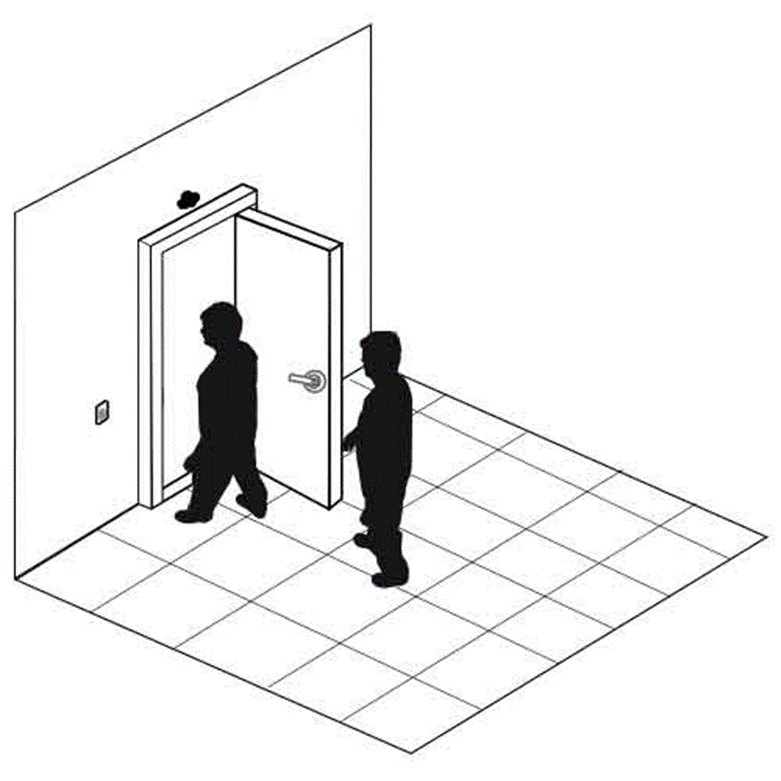
How to prevent
- Proper user education to enforce the use of access cards and prohibit tailgating. Users should know that not holding the door is not considered rude.
- Install a security guard at each entrance or monitor entrances with security cameras
- In more extreme cases, installation of man trap doors might be necessary. A man trap door allows only one person to enter at a time. The man trap door contains cameras with artificial intelligence to detect the number of people inside and permits entry to only one individual at a time.

A Fence or Gate or Cage keeps people out or keeps people in. For example, a tool storage area inside a building/warehouse might be fenced in.
Consider
- Who you are trying to stop. A chain-link fence can be cut with wire cutters easily. Even a barbed wire fence can be cut. Fences are good for slowing down random people who are trying to climb over but are not so good for vehicles or sneaky people. In those cases, a concrete wall may be required.
- An electric fence is more effective at keep people out but may introduce unwanted legal liability. An electric fence must have clear signage that identifies it as such. It should also be separated from the public by a normal fence so that people cannot inadvertently contact it.
- Whether the fence is opaque or transparent (chain link). The fence may need to be opaque so that people can’t see inside.
- The height of the fence. A tall fence may stop people from climbing or seeing over it, but it is irrelevant if people can cut through the fence or fly drones into the facility.
- Fences can be used in combination. The fence provides a buffer zone. It slows people down. By the time a person has penetrated the fence, security will have been able to intercept them. The fence can be monitored with cameras, security patrols, and sensors.
Inside a building, chain link fencing can be used to set up cages for controlled physical access. It is cheaper to build a cage than a physical room.
A security guard is a human who provides security. The security guards may be stationed in key areas, may walk around, or may drive patrol vehicles.
Proper training is important. A security guard who is not vigilant will not be effective. Security guards who use excessive force, are disrespectful, or are perceived to be incompetent, will cost the company money, introduce legal liability, and damage its reputation.
Security guards may be outsourced from a company like G4S or Guarda. There is no good reason to outsource, except for cost. When renting security guards, it is important to ensure that the security company sends the same people each time, so that they become familiar with the premises. Many companies outsource security so that they do not have to risk legal liability in the event that a security guard acts inappropriately.
A larger organization may be able to better train an internal security force, even with as few as 50 security guards.
The security guard’s most important tool is his brain. Security guards also have other tools like guns, handcuffs, batons, and pepper spray, depending on the state/province that they are in. The organization must decide if it should risk the liability and cost of training to supply security guards with weapons.
Artificial intelligence is no substitute for a human brain. It is important to ensure that the security guard is aware of his surroundings. A security guard who is complacent may be worse than no security guard at all. Security guards are human and can be manipulated through social engineering techniques.
In general, a security guard is not a law enforcement officer. A security guard is entitled to
- Enforce the law when seeing an actual commission of a crime on the organization’s property
- Use reasonable force to protect himself or another human being from physical harm or death
- Use reasonable force to protect the physical property of his organization
- Detain an individual who the security guard knows has committed a felony (an indictable offense in Canada), and promptly turn him to a law enforcement agent
- Use reasonable force to prevent a trespasser from entering a secured facility
Security guards may also have dogs that can detect for food, drugs, or explosives. Like a weapon, the use of a dog can also subject the organization to serious legal liability.
A security guard also keeps track of visitors
- Signs visitors in and out
- Verifies that the visitors are legitimate
- Ensures that visitors have been briefed on the organization’s security and safety policies and that they are wearing appropriate personal protective equipment (PPE), if required
- Escorts visitors to the appropriate locations
An alarm is necessary to protect critical assets. The two main types of alarms
- Intruder alarm – detects intrusions
- Environmental alarm – detects a fire, flood, high temperatures, etc.
The alarm will have multiple components
- Sensor. The sensor detects an event
- Motion Sensor detects motion, which could indicate the presence of an unauthorized person
- Glass Break Sensor detects if glass has been broken based on the specific sound frequency that broken glass makes
- Door/Window Contact detects if a door/window is closed or if has been opened. The sensor consists of a magnet that sits on the door/window and a contact that sits on the door/window frame. This creates a closed circuit. When opened, the door/window breaks the circuit, and an alarm activates
- Smoke Detector detects for the presence of smoke but can also sound a false alarm. It can be triggered by dusty conditions.
- Flood Detector detects moisture content. This may be installed in a server room.
- Thermostat detects temperatures that are too high or too low. High temperatures can lead to equipment damage. Cold temperatures can cause water pipes to burst.
- Controls. The controls allow the alarm to be programmed. The controls collect data from the sensors and decide if an abnormal event has occurred, in which case the alarm is triggered. The controls send an alert to another device.
- Alerts. The alarm must make an alert, or else it will have no purpose. It must notify somebody that an abnormal condition is present. Some forms of alerts
- Siren/Flashing Lights can scare intruders but are by themselves just a nuisance. Some intruders will ignore the alarms, especially when there are many false alarms. A police department will probably not respond to an audible alarm unless they are specifically notified that a crime is in progress.
- Alert on a control panel. The alarm can notify a monitoring station so that the responsible people can verify that the alarm is real and take additional action such as calling the police, calling for emergency services, or dispatching a security guard to investigate.
- Automated phone call/email/SMS alert to the responsible people
When an alarm is triggered, a security guard might first review the surveillance cameras in the relevant areas to determine if there is a problem. The security guard would then physically investigate the areas and act as appropriate. If nothing out of the ordinary is present, the security guard may turn off the alarm and record his findings.
An alarm system can be divided into multiple zones. Each zone is subject to its own rules. For example, a zone can be always armed, or it can be armed at night. A server room might always be armed unless somebody needs to access it. An office might only be armed at night when nobody is present.
When an alarm is in an armed state, any sensor activity will trigger an alarm.
The control system for an alarm must be in a physically secure room. The control system must itself be alarmed (connected to a tamper-detecting sensor), so that any attempt to disable it is detected.
