5.5 Describe remote access and site-to-site VPNs
An employee might want to work from home or on the road but needs access to the corporate network. We can’t build a WAN link to each user because that would be too expensive.
A VPN or Virtual Private Network allows us to connect to the corporate network and pretend that we are physically on the network. The user uses his own personal internet connection, and the VPN software transports the data back to the corporate network over a tunnel. The VPN also encrypts the traffic.
We can also use a VPN to connect a remote site to our main network when a WAN is not available or too expensive.
There are several types of internet connections available to end users and VPNs can be established over all of them.
A DSL or Digital Subscriber Line is delivered over a phone line. It may provide speeds of up to 150 Mbit/s. A subscriber will require a DSL modem to convert the signal from a phone line to an ethernet cable. The same phone line can be used to transmit voice simultaneously because internet traffic is transmitted at a different frequency from voice traffic. At the ISP’s network, voice and data are filtered and sent to different types of equipment. Voice traffic is routed to a telephone switch, while data traffic travels to an internet router. The device that performs this filtering is called a digital subscriber line access multiplexer or DSLAM. When a DSL modem powers on, it must synchronize with the DLSAM so that they can agree to filter out noise and errors. After synchronization, a DSL modem is ready to transmit data. A DSL modem will typically have a “link” or “DSL” light that shows its synchronization status. Below is a photo of a common DSL modem.

Cable Broadband is a product competing with the DSL. While DSL is typically provided by a phone company Cable Broadband is provided by a cable television provider and is delivered over a coaxial cable. A subscriber requires a cable modem to connect to the network. At the provider’s facility, a device known as a cable modem termination system is installed. This device synchronizes with the subscriber cable modems and transfers their data to the internet. It is necessary for the ISP to filter video and internet traffic at their data center.
Another option is to install a Wireless WAN like a 4G, LTE, or possibly 5G. A cellular modem connects to the ISPs cellular network via an antenna. Each cell tower contains a fiber optic connection back to the ISPs main network. The modem uses a SIM card to authenticate to the network. Many Cisco routers can connect directly to a cellular internet connection via an expansion card. Some Meraki routers can accept a SIM card and connect to a cellular network.
Fiber is quickly replacing copper, even in residential neighborhoods. Most fiber is being installed by the phone companies, which typically have the right to install underground cable. Cable companies and cellular providers own some fiber as well. Metro Ethernet is typically delivered over fiber, although it could be delivered over copper.
The VPN must be able to do the following
- Authenticate each user so that the network can confirm he is legitimate and that he only has access to the resources that he is entitled to.
- Authenticate each network so that the user can confirm that he is connecting to a legitimate corporate network.
- Provide data integrity to confirm that the data received by the network is the data that was sent.
- Provide anti-replay protection to prevent a man-in-the-middle attack – a situation where a hacker can intercept a legitimate packet and resend it in order to gain access to a protected resource
- Encrypt the data so that nobody on the internet can see it.
A site-to-site VPN allows two sites to create a connection, like a point-to-point tunnel. At the edge of each network is a router that connects to the internet. We configure the edge routers to create a tunnel between each other, which is always on. The routers use the tunnel to transport data between their locations.
Any internal device at one site can communicate with any internal device on another site without having to create a separate VPN tunnel because the edge routers handle the traffic.
We use a technology like Generic Routing Encapsulation to create the tunnel.
Consider this scenario. Computer A is connected to Router A, and Computer B is connected to Router B. Each computer is on a separate LAN, but we don’t have a WAN connection between the two LANs.
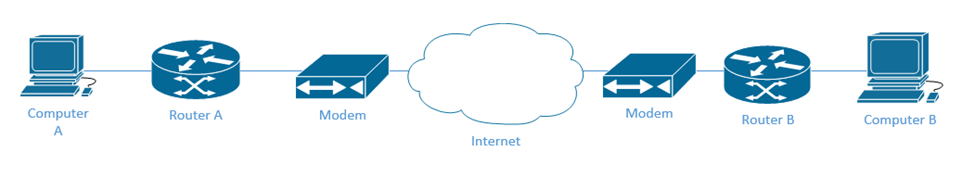
Router A and Router B create a tunnel so that they can transport traffic between their respective networks. Computer A and Computer B continue to speak with their routers as normal. They do not know anything about the tunnel.
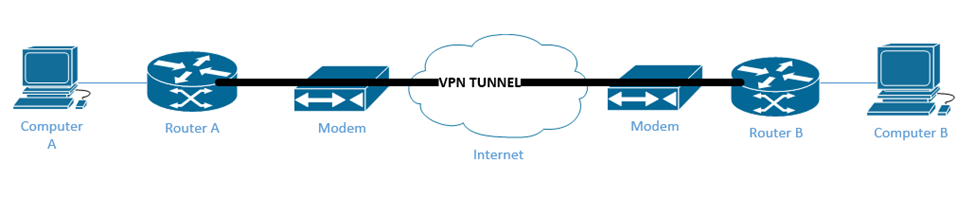
An IPSec architecture defines how the VPN will encrypt traffic, but the member devices are free to use any type of protocol to provide encryption or communication. When establishing a tunnel, the two devices must agree on an encryption key. How do two devices agree on an encryption key and share it over the internet without anybody seeing it?
Each device generates two encryption keys. The first encryption key is called the private key and can only decrypt data. The device uses the private key to generate a public key. The public key only encrypts the data. It is possible to generate a public key from a private key, but it’s not possible to generate a private key from a public key.
The device shares its public key with the sender (the other party to the communication). The sender uses the public key to encrypt the data and send it to the recipient. The public key can be placed on the internet without any harm because it can’t be used to decrypt the data.
Upon receipt of an encrypted message, the recipient uses its private key to decrypt the data. A device might generate a different set of keys for each party that it communicates with.
There are many algorithms that can be used to generate and exchange the keys. The keys might be known as a shared secret. One popular algorithm is called the Diffie-Helman Key Exchange.
There are two problems with using a public/private encryption key. First, it takes a lot of system resources to encrypt and decrypt each message. Second, there is a risk that the private key gets leaked. If a hacker intercepted and stored all our encrypted messages, he could wait until he obtained the key, and then used it to decrypt everything we said.
What we need to do is generate a second simpler key from the encryption key. This key is called a session key or an ephemeral key. It requires less system resources to encrypt and decrypt data with the session key.
In a communication, we generate a new session key for each message, thereby encrypting each message with a different session key. If a session key is compromised, a hacker will only be able to view the contents of a single message, instead of the entire conversation. The original private key cannot be used to decrypt any messages, so if it is leaked, no communications will be compromised. This is known as perfect forward secrecy.
For a user working from home, a better tunnel is a VPN over TLS. TLS, or Transport Layer Security is a replacement to SSL. TLS is also used to encrypt traffic between a user and a web server. Instead of using an unsecure HTTP protocol, a user’s web browser and the web server agree to establish a TLS session and send the HTTP traffic inside it.
Cisco AnyConnect Secure Mobility Client is a software program that we can install on any end user’s computer. The Client helps the user connect to the corporate network over a VPN tunnel. Unlike a site-to-site VPN that is always on, a user only activates a remote VPN when he needs to access internal resources.