3.9 Design site and facility security controls
- Wiring closets/intermediate distribution facilities
- Server rooms/data centers
- Media storage facilities
- Evidence storage
- Restricted and work area security
- Utilities and Heating, Ventilation, and Air Conditioning (HVAC)
- Environmental issues
- Fire prevention, detection, and suppression
- Power
Proper physical security is important in any facility. Different levels of physical security have different costs. The cost of physical security should be proportional to value of the assets being protected or to the harm that would result from a compromise of those assets.
Physical security is built in layers. We can look at the some of the following references for guidance
- BICSI TDMM (Telecommunications Distribution Methods Manual). BICSI puts out standards including how to install data, communications, and AV cabling, sizing of riser rooms, fire stopping, and project management.
- Uptime Institute Tier Standards. The tier standards are an international standard, which tell us how redundant our data center is.
- Tier 1. A basic data center that does not have any redundancy. The data center will shut down if any equipment fails. It requires
- A UPS
- Dedicated cooling
- A generator
- A UPS
- Tier 2. A basic data center with redundancy for power and cooling. The data center will not shut down if any equipment fails, but may need to shut down for maintenance. It requires
- Tier 3. The data center has redundant power and cooling, with redundant pathways for each. We can remove, shut down, and maintain power or cooling equipment without disrupting the data center.
- Tier 4. A Tier 4 is like a Tier 3 data center, but everything is fault tolerant.
- Tier 1. A basic data center that does not have any redundancy. The data center will shut down if any equipment fails. It requires
- ASHRAE (American Society of Heating, Refrigeration and Air Conditioning Engineers). ASHRAE publishes recognized standards for HVAC equipment installation.
Mechanical engineers follow ASHRAE standards when designing mechanical systems, and these standards are legally recognized and binding by many jurisdictions in the United States and Canada. - NFPA (National Fire Protection Association). NFPA publishes standards for fire protection and suppression. Like ASHRAE, their standards are binding in many jurisdictions in the United States and Canada.
- Local, regional, and national building codes. Your jurisdiction may impose additional requirements.
Let’s look at some general security measures and then we will discuss what we need in each type of facility.
Bollards/Barricades
A barricade or bollard is a physical device that keeps vehicles from crashing through a building. The barricade can be made of metal, concrete, or plastic (filled with sand or water). A barricade can be designed as part of a landscape architecture so that it is aesthetically pleasing.
The barricade is used to provide an additional layer of security next to a fence. A fence can keep people from climbing over but won’t stop a vehicle, and a barricade can stop a vehicle but won’t stop a person.
Below is a retractable barricade. We install this at a gate. It can stop vehicles of most sizes. When a vehicle is authorized to enter, we can lower the barricade. The barricade might be operated manually or automatically.
These barricades are typically found at high-security facilities where the vehicle is first checked for explosives.

For many buildings, decorative bollards are more appropriate. They can be disguised as part of the landscape or blend in with the architecture. One concept uses concrete planters which can be filled with flowers or trees.

Below is a courthouse. Instead of installing bollards, they raised the concrete around the building by approximately eight inches. This is enough to stop any vehicle from driving over it, while still allowing people to walk on top of it.

Fencing/Gate/Cage
A Fence or Gate or Cage keeps people out or keeps people in. For example, a tool storage area inside a building/warehouse might be fenced in so that only authorized people can take the tools. Fences commonly work with bollards.
When designing a fence, consider
- Who you are trying to stop. A chain-link fence can be cut with wire cutters easily. Even a barbed wire fence can be cut. Fences are good for slowing down people who are trying to climb over but are not so good for vehicles or sneaky people. A fence in combination with bollards may be a better approach. You can also consider a concrete wall.
- An electric fence is more effective at keep people out but may introduce unwanted legal liability. An electric fence must have clear signage that identifies it as such. It should also be separated from the public by a normal fence so that people cannot inadvertently contact it. In some areas, an electric fence might be illegal.
- An electric fence is more effective at keep people out but may introduce unwanted legal liability. An electric fence must have clear signage that identifies it as such. It should also be separated from the public by a normal fence so that people cannot inadvertently contact it. In some areas, an electric fence might be illegal.
- Whether the fence is opaque or transparent (chain link). The fence may need to be opaque so that people can’t see inside.
- The height of the fence. A tall fence may stop people from climbing or seeing over it, but it is irrelevant if people can cut through the fence or fly drones into the facility.
- Fences can be used in combination with other security measures. The fence provides a buffer zone. It slows people down. By the time a person has penetrated the fence, security will have been able to intercept them. The fence can be monitored with cameras, security patrols, and sensors.
Some high security fence ideas include
- Fences with razor wire in the chain link
- Chain link fences that are nearly invisible. They provide security but are also aesthetically pleasing.
- Fences that can be rapidly deployed from the back of a truck
- Fences that can be placed in the water to stop boats
- Fences that contain fiber optic cable. If the fence is touched or cut, the intrusion is automatically detected.
Inside a building, chain link fencing can be used to set up cages for controlled physical access. It is cheaper to build a cage than a physical room.
Signs
Signs work well with fences. We put signs up for two reasons
- Give people directions. Signs are especially useful when we have multiple entrances (employee entrance, visitor entrance, security, shipping/receiving, etc.)
- Tell unwanted people to stay out. The content of the sign may need to be in multiple languages. When you put up a sign telling people not to trespass, they will not be able to claim ignorance later.
Mantrap or Access Control Vestibule
A man trap is a door that only allows a single human to enter or exit at a time. The man trap door is typically used in combination with a card access/biometric authentication.
The user presents his credentials to a card reader and/or security guard. The first door opens, and the user enters a small hallway or room. The first door closes, and when the first door is closed, the second door opens. The man trap may be outfitted with a camera that detects if multiple individuals are present.

These are common in data centers and airports.
Badges
Anybody who is in our facility should wear a badge. A badge should have the following information
- Whether the person is an employee, contractor, or guest
- The name of the person
- The job title of the person
- The security level of the person, if applicable
- A clear photograph of the person
- The expiry date of the badge
Badges may be color coded to indicate security levels. People should wear their badges close to their faces and not on their hips. This makes it easier to read the badge and compare the photograph to the person’s face.
When an employee or contractor is terminated, security should take their badge away.
A guest should be given a badge when they enter the facility and they should return the badge when they leave.
Alarms
An alarm is necessary to protect critical assets. The two main types of alarms
- Intruder alarm – detects intrusions
- Environmental alarm – detects a fire, flood, high temperatures, etc.
The alarm will have multiple components
- Sensor. The sensor detects an event. Some types of sensors
- Motion Sensor detects motion, which could indicate the presence of an unauthorized person. Newer motion sensors have dual technology – a passive infrared signal and a microwave radar
- Glass Break Sensor detects if glass has been broken based on the specific sound frequency that glass breaking makes
- Door/Window Contact detects if a door/window is closed or if has been opened. The sensor consists of a magnet that sits on the door/window and a contact that sits on the door/window frame. This creates a closed circuit. When opened, the door/window breaks the circuit, and a signal activates
- Heat Detector detects for the presence of heat or for a rapid change in the temperature. Heat detectors come in different temperature ranges. A heat detector is usually connected to a fire alarm.
- Smoke Detector detects for the presence of smoke. A false alarm can occur if there are dusty conditions. A smoke detector is used in high heat areas where a heat detector would be inappropriate. A heat detector is usually connected to a fire alarm.
- Flood Detector detects moisture content. This may be installed in a server room, or in another area that is prone to flooding.
- Thermostat measures the temperature in the room. The thermostat can trigger a heater or air conditioner as required. High temperatures can lead to equipment damage. Cold temperatures can cause water pipes to burst.
- Motion Sensor detects motion, which could indicate the presence of an unauthorized person. Newer motion sensors have dual technology – a passive infrared signal and a microwave radar
- Controls. The control panel is the brains behind the operation. The controls collect data from the sensors and decide if an abnormal event has occurred, in which case the alarm is triggered. We must first program the control panel. The controls send an alert to another device.
- Alerts. The alarm must make an alert when there is an abnormal condition, or else it will have no purpose. It must notify somebody that an abnormal condition is present. Some forms of alerts
- Siren/Flashing Lights can scare intruders but are by themselves just a nuisance. Some intruders will ignore the alarms, especially when there are many false alarms. A police department will probably not respond to an audible alarm unless they are specifically notified that a crime is in progress.
- Alert on a control panel. The alarm can notify a monitoring station so that the responsible people can verify that the alarm is real and take additional action such as calling the police, calling for emergency services, or dispatching a security guard to investigate.
- Automated phone call/email/SMS alert to the responsible people or to a monitoring station.
- Siren/Flashing Lights can scare intruders but are by themselves just a nuisance. Some intruders will ignore the alarms, especially when there are many false alarms. A police department will probably not respond to an audible alarm unless they are specifically notified that a crime is in progress.
When an alarm is triggered, a security guard might first review the surveillance cameras in the relevant areas to determine if there is a problem. The security guard would then physically investigate the areas and act as appropriate. If nothing out of the ordinary is present, the security guard may turn off the alarm and record his findings.
An alarm system can be divided into multiple zones. Each zone is subject to its own rules. For example, a zone can be always armed, or it can be armed at night. A server room might always be armed unless somebody needs to access it. An office might only be armed at night when nobody is present.
When an alarm is in an armed state, any sensor activity will trigger an alarm.
The control system for an alarm must be in a physically secure room. The control system must itself be alarmed (connected to a tamper-detecting sensor), so that any attempt to disable it is detected.
When you design an alarm system, consider the following
- It is likely that your building will require a fire alarm. The fire alarm is separate from the intrusion alarm. It consists of smoke and heat detectors, bells, and a fire control panel. Fire alarms must be monitored, and their design, installation, and testing are subject to strict standards.
The company that monitors your fire alarm might also monitor your intrusion alarm. - Identify the locations where you need to place sensors
- Each door will require a sensor to determine whether it is open or closed
- Each window that opens will require a sensor to determine whether it is open or closed
- A glass break sensor should be installed opposite each window
- A motion sensor should be installed opposite each door or window as a back up to the open/close sensor
- Motion sensors should also be installed in large rooms
- Each door will require a sensor to determine whether it is open or closed
- Decide on a secure location to place the control panel
- Select one or more locations to install keypads. A keypad is used to disarm the alarm. A keypad should be installed next to any main entrance.
- Decide whether the system should be wired or wireless.
If the system is wireless, then you will need to change batteries in the sensors often. You will also need to install an adequate number of wireless repeaters if the building is large.
If the system is wired, then you will need to install alarm wire. Wired devices can be daisy chained, but there is a limit to the number of devices that can be connected to a single wire, and there is a limit to the length of the wire. - Divide the building into zones. We group the sensors into zones. When a sensor is triggered, the alarm will tell us which zone is affected.
- If the building has only a few sensors, we can assign each sensor to its own zone. For example, “Front Glass Break Sensor” might be a zone.
- If the building is large, then we can divide the building into something logical
- We might put wireless devices on one zone
- We might put each entrance on a separate zone
- The point is, if a sensor triggers an alarm, how quickly can you respond based on the zone information
- If the building has only a few sensors, we can assign each sensor to its own zone. For example, “Front Glass Break Sensor” might be a zone.
- Decide on the operating hours and program the system
- When people are in the building, then the system is disarmed. Motion and doors/windows opening do not trigger an alarm
- When the last person leaves the building, he must arm the system. Once the system is armed, any motion or door/window opening triggers the alarm
- You might have sensitive areas that are always armed unless somebody requires access. Examples could include a server room, a mechanical room, or a vault. You should put each of these rooms on a separate zone and keep that zone armed.
- When people are in the building, then the system is disarmed. Motion and doors/windows opening do not trigger an alarm
- You should purchase an alarm system with a control panel that supports the number of sensors that you require and the number of zones that you require
- Decide on how the system will be monitored
- If you have a continuous security presence, you might monitor the system in house. It might be linked to displays at your security office.
Remember that you usually cannot monitor your own fire alarm unless your monitoring center meets very specific requirements.
- If you outsource the monitoring, you will need to connect your control panel to a phone line, a cellular model, or the internet.
- You might outsource the monitoring but still configure the system to send alerts to your phone or e-mail address.
- If you have a continuous security presence, you might monitor the system in house. It might be linked to displays at your security office.
Cameras
A surveillance camera is used to monitor a physical area. At a minimum, cameras should be placed
- At all entrances
- Around the perimeter of your fence, if you have one
- At locations where money is counted or exchanged
- At locations where valuables are stored
- At all shipping and receiving areas
- At areas where thefts or acts of violence can occur
- At other areas where video monitoring is required
Ideally, you should have enough cameras to monitor every square inch of your facility. If you have areas where workers are performing physical labor, using tools, or handling products, you should have cameras. People often claim to get hurt at work and having adequate cameras will reduce some of those claims.
Cameras can be used with software that can
- Perform facial recognition and automatically detect/identify individuals and known trespassers.
The more advanced software can detect objects. For example, if a woman puts a purse down on a table, the software can recognize that object as a purse. If a thief steals the purse and walks away with it, the camera software can follow the purse throughout the facility across multiple cameras.
We can click on the purse and the software can show us where it went, regardless of which camera saw it. Or we can click on a person’s face and follow them around. The software automatically switches from camera to camera as they walk around the facility. - Provide data analytics to understand traffic patterns. Many retailers use cameras that can understand how people travel throughout the store and what products they look at the most.
- Detect motion. When detecting motion, a camera can automatically trigger an alert through the alarm system just like a motion sensor
Cameras are available in a wide variety of models and features.
- Analog or digital. Digital cameras are better because they can connect to an NVR over a network, can be powered by PoE, and offer higher resolutions. I do not recommend the use of an analog camera.
- Resolution. The resolution tells us how much detail we can see in the video feed and is measured in megapixels. Security cameras are available in resolutions of up to 4K. The resolution you require depends on the size of the area that you are watching – the higher the area, the greater the resolution.
You should choose a camera with a higher resolution than needed, and then reduce the video feed to a lower resolution. If you find later that you require a higher resolution, you can always increase it without having to replace the camera. - Digital and analog zoom. You should consider analog zoom when you are watching a large area but need to zoom in later to observe some details, such as a license plate. You can’t zoom in to a video after it has been recorded, so take this into consideration when choosing a camera resolution.
- PTZ. Ability to Pan, Tilt, and Zoom. PTZ is controlled by a motor inside the camera and allows you to move the camera around to observe other areas. It is good when the camera’s field of view is not wide enough to see the entire area. If you frequently need to move the camera, consider adding additional cameras, or replacing the cameras with wide-angle cameras. There are 180 degree and 360-degree cameras on the market.
- Optional heater for outdoor cameras. Many cameras will not function in the extreme cold.
- Indoor and outdoor ratings (designed to withstand cold weather). Choose a camera that can withstand the environment you are placing it in.
- Water/dust ingression rating. A camera will have a rating that is IPXX.
- The first X is a number from 0 to 6 that tells us how resistant the camera is to dust
- The second X is a number from 0 to 9 that tells us how resistant the camera is to water.
- The first X is a number from 0 to 6 that tells us how resistant the camera is to dust
Most cameras are rated at least IP67 now, which means that they are completely dust proof and can be submerged in up to one meter of water.
- Resistant to vandalism. A camera will have a vandalism rating that is IKXX, where XX is a number from 01 to 10. The higher the rating, the greater an impact the camera can take and keep functioning.
Choose a camera with a rating of IK10.
When you think about vandalism, consider that even though the camera might be solid, somebody could still spray paint it, cover it, cut the cable connecting it to the network, point it in a different direction, unscrew it from the wall, or damage the mount. - Integrated speaker/microphone. A speaker or microphone might be helpful.
- Internal storage (some cameras contain flash memory and can directly record video, negating the use of an NVR).
- Night vision and low-light viewing. Night vision is always necessary.
- Shape. Cameras generally come in two shapes: bullets and domes. A dome camera conceals the lens so that intruders don’t know where it is pointed. Dome cameras are more common in retail stores.
Bullet cameras provide more of a visual deterrent, and larger bullet cameras usually can accommodate lenses that provide a large optical zoom.
The camera video feed is recorded onto a network video recorder (a dedicated device or a computer with video recording software). The NVR can connect directly to (and power) each camera. In a larger, distributed installation, the cameras and the NVR might connect to the corporate network and have an independent VLAN. If we have a massive amount of video to store, we may create a shared directory on a storage appliance and connect it to the NVR.
The organization must decide how many days (weeks/months) worth of video they require. This affects the amount of storage space required (and then also the size of the NVR required). The amount of space required depends upon the
- Quantity of cameras
- Video resolution of each camera
- Frame rate of each video feed
- Whether the camera records 24/7 or only when the camera detects motion
Some cameras have built in storage capacity so that they can record more data even when the NVR is offline. Some cameras can be cloud managed, where they upload their video to the internet. This can consume substantial network resources. A network may not be capable of uploading all the video generated by the cameras.
It is important to post signs stating that the facility is subject to video surveillance. People who enter the facility should be required to sign a waiver indicating that they consent to the video surveillance and recording.
If you do not, you could be subject to a privacy lawsuit. In addition, the video that you collect may be considered inadmissible in a legal proceeding.
If the facility is large, we might monitor it with a drone. A drone can see people on the ground even if they can’t see it. A drone is useful for monitoring things like a long fence or a forest.
Logs
Logs are used in conjunction with physical security controls. The logs allow access/access attempts to be audited.
The logs should identify
- The identity of the person who accessed the resource
- The date and time that it was accessed
- The resource that was accessed
- How the identity of the person was verified and how the entitlement was verified
Each time a visitor enters or leaves a building, their entry/exit should be logged. Each time a person enters a server room or other controlled space, their presence should be logged. A log may be written or electronic.
Infrared Detection
Infrared detection identifies individuals and other objects through the heat patterns that their bodies generate. IR can be integrated into a surveillance camera or can part of a standalone sensor. IR detectors are more useful at night.
Industrial Camouflage
Industrial Camouflage is where we hide what is inside a facility so that we don’t attract attention.
Most data centers are unmarked. You can drive by many data centers and not realize what is inside because there are no signs outside that say it is a data center. It will look like a big long warehouse.
Many phone companies house their switching equipment in buildings that look like office towers.
Security Guards
A security guard is a human who provides security. The security guards may be stationed in key areas, may walk around, or may drive patrol vehicles.
Proper training is important. A security guard who is not vigilant will not be effective. Security guards who use excessive force, are disrespectful, or are perceived to be incompetent, will cost the company money, introduce legal liability, and damage its reputation.
Security guards may be outsourced from a company like G4S or Guarda. There is no good reason to outsource, except for cost. When renting security guards, it is important to ensure that the security company sends the same people each time, so that they become familiar with the premises. Many companies outsource security so that they do not have to risk legal liability in the event that a security guard acts inappropriately.
A larger organization may be able to better train an internal security force, even with as few as 50 security guards.
The security guard’s most important tool is his brain. Security guards also have other tools like guns, handcuffs, batons, and pepper spray, depending on the state/province that they are in. The organization must decide if it should risk the liability and cost of training to supply security guards with weapons.
Artificial intelligence is no substitute for a human brain. It is important to ensure that the security guard is aware of his surroundings. A security guard who is complacent may be worse than no security guard at all. Security guards are human and can be manipulated through social engineering techniques.
In general, a security guard is not a law enforcement officer. A security guard is entitled to
- Enforce the law when seeing an actual commission of a crime on the organization’s property
- Use reasonable force to protect himself or another human being from physical harm or death
- Use reasonable force to protect the physical property of his organization
- Detain an individual who the security guard knows has committed a felony (an indictable offense in Canada), and promptly turn him to a law enforcement agent
- Use reasonable force to prevent a trespasser from entering a secured facility
Security guards may also have dogs that can detect for food, drugs, or explosives. Like a weapon, the use of a dog can also subject the organization to serious legal liability.
A security guard also keeps track of visitors
- Signs visitors in and out
- Verifies that the visitors are legitimate
- Ensures that visitors have been briefed on the organization’s security and safety policies and that they are wearing appropriate personal protective equipment (PPE), if required
- Escorts visitors to the appropriate locations
If the office is small, the role of the security guard may be given to the receptionist. The receptionist can sign visitors in and out, but she probably won’t be able to tackle an intruder. Since many people are working from home, the receptionist’s role can be outsourced to a robot or an iPad.
When an area is critical, we might always have two people guarding the security desk. This prevents a crooked security guard working alone from colluding with an intruder.
Locks
There are many types of locks. Locks can be three things
- Mechanical Key lock. The mechanical key lock is used when there are only a limited number of keys required (such as a person’s office) and where it is not practical (or too expensive) to install electrical/network cabling and components for an electronic lock. The mechanical lock is excellent for this.
The disadvantage is that the mechanical lock requires physically creating keys for each user. If an individual loses a key or it is stolen, then the lock must be physically rekeyed. All users must then receive new keys corresponding to the lock.
A set of locks can be keyed with individual user keys and with a master key that opens all the locks. If the master key is lost, then all the locks must be rekeyed.
- Combination lock. The combination lock is for low security but where there are multiple users. The combination can be changed in the lock. A combination lock may be electronic or mechanical. Combination locks are frequently installed in lunchrooms and staffrooms.
- Electronic lock. The electronic lock is most important because it allows multiple people to access the system, and has the following features
- Restrict access based on time of day
- Restrict access based on location
- Allow a user to access multiple doors and locations with a single key card
- Use the key card in combination with the multi-factor authentication
- If the key card is lost or stolen it can be disabled without having to rekey the locks
- Restrict access based on time of day
- Lock that can be opened with both an electronic lock and a mechanical key. The mechanical key must be kept secure, and it is used to access the building in case a power outage disabled the electronic portion of the lock.
In a mechanical key lock, there are two ways in
- It can be broken. The thief who is willing to break the lock is one who does not care if the entry is later detected (somebody who is stealing something like money). The thief will break whatever is weakest – a nearby window, the door, or the lock. Therefore, it is important to make sure that the building is physically secure, not just the lock. The lock must be physically secure in that it cannot be broken or drilled.
Many mechanical locks exist for bicycles and laptops. These locks can be easily cut or broken. They prevent only the most casual of thefts, and it is better to ensure that these items are never left unattended. - It can be picked. The thief who wants to pick the lock is more sophisticated and does not want to be detected (somebody who is stealing data or planting a listening device/spyware). Some locks can be bypassed due to poor design. Otherwise, they can be broken or picked depending on how they are designed.
What I learned from the Lock Picking Lawyer (on YouTube) is that every lock can be picked. The question is, how long? The longer it takes to pick a lock, the more time there is to catch the intruder. If we combine a lock with a motion sensor or security camera that is being actively monitored, then it is less likely that an intruder will gain access.
An electronic lock cannot be picked, but some can be bypassed
- Hacking into the electronic system that manages the lock, and commanding it to open the door
- Creating a replica of a valid key card and using it to gain access
- Using a magnet to unlatch the door (some electronic door locks contain magnets that are easily bypassed)
Cable Locks
A cable lock is a lock that secures a computer or other hardware to a desk or other physical furniture. Most computers, monitors, and docking stations have ports that accommodate a cable lock. The cable lock is inserted into the port, wrapped around a physical piece of furniture (such as table leg) and then locked.
A cable lock can be easily cut with a bolt cutter, and only provides protection against casual theft. Some cable locks are alarmed and will trigger an alert when cut.
There are also locks that can alarm when the computer is moved. An example is a mount for an iPad, which has sensors that alert when the mount is lifted.

Safe
A safe protects valuables against fire and intruders. The safe can be opened with
- A numeric combination
- A key
- A key and a numeric combination
Safes come in many sizes. The larger safes are called vaults. The safe can also be connected to an alarm, which can be triggered if the safe is opened. Many jewelry stores have two separate alarm sensors connected to their safes (and possibly two separate alarm systems provided by different vendors). This eliminates a single point of failure in the alarm system.
The safe is subject to
- Fire. It is important to choose a safe that is rated to withstand at least one hour of fire.
- Physical removal. Thieves will first attempt to steal the entire safe and crack it later. It is important to bolt the safe down to the ground so that it cannot be stolen.
- Damage. Thieves will try to break through the safe. On many safes, it is difficult to pry open the door with a crowbar, but it is easy to cut through the side wall. Many safe manufacturers put a lot of effort into reinforcing the door, but very little effort in reinforcing the walls.
- Cracking. Many safes are flawed in their design, either through poor design or gaps in the door. Some safes can be cracked by inserting a magnet or small pry bar tool inside. It is important to choose a safe that cannot be cracked.
A safe can be hidden. It is a good idea to hide a safe to provide an additional layer of security.
Secure Cabinets/Enclosures
A secure cabinet/enclosure can hold items or documents. It is not as secure as a safe but can protect against unauthorized access. Secure cabinets are designed to protect large volumes of documents.
Protected Distribution/Protected Cabling
Protected distribution ensures that the cables are physically secure. An intruder could physically penetrate a data cable and hijack a connection such as a camera or a printer. This is an unlikely scenario, but still possible.
Cables should be protected against damage. They should be installed inside conduit and cable trays.
It is important to physically secure devices such as cameras and wireless access points (which can be hidden inside the ceiling space).
It is also important to not patch in cables that are not in use.
Lighting
Proper lighting is important for
- Physical safety of people walking. Hazards can be illuminated. It is important to provide bright lights on all entrances and walkways
- Making things visible. Intruders and criminals are more tempted to access buildings at night.
- Emergencies. Emergency lighting is necessary and may be required under various building codes. Emergency lighting is battery-operated and activates in the event of a power outage. It ensures that people can always see their way out.
Bad people can hide in dark corners and then sneak into the building or mug people walking by.
Faraday Cage
A Faraday Cage is a container that prevents the transmission of electromagnetic radiation (such as cellular or Wi-Fi signals). A Faraday Cage can be used to
- Isolate a device. For example, a cell phone seized during an investigation could be remotely wiped by the defendant. It must be secured in a Faraday cage so that it cannot transmit or receive data.
- Prevent data leaks. To prevent users from transmitting data without authorization, a Faraday Cage can be built around a room. This type of cage doesn’t work because users can secretly record data and leave with the recording device.
- Protect a device from EMI. Most devices have some EMI shielding.
A good substitute for a Faraday Cage is aluminum foil. Wrapping a cell phone with aluminum foil is just as effective as a commercial Faraday Cage.
Airgap
An air gap is a physical separation of a network. An air gap is necessary to protect against vulnerable networks where the risk of intrusion or damage is so high that the cost is justified. Networks that require air gaps include
- Networks that contain classified information
- Nuclear facilities
- Public utilities such as water, power, and gas
- SCADA and other industrial control networks
Environmental Controls
In a data center, there are three main types of environmental controls
- Hot and Cold Aisles. Proper design includes hot and cold aisles. Most rack-mounted equipment is designed to pull air through horizontally. The front of the device pulls cool air in. The air travels through the device, warms up, and is ejected through the rear.
In a standard rack, the devices should be installed so that the air intake is on one side and the air output is on the other side. Racks are installed facing back-to-back and front-to-front. Then the result is that front-to-front aisles are cool, and back-to-back aisles are warm. The data center can then pump cool air in the front-to-front and eject warm air from the back-to-back.
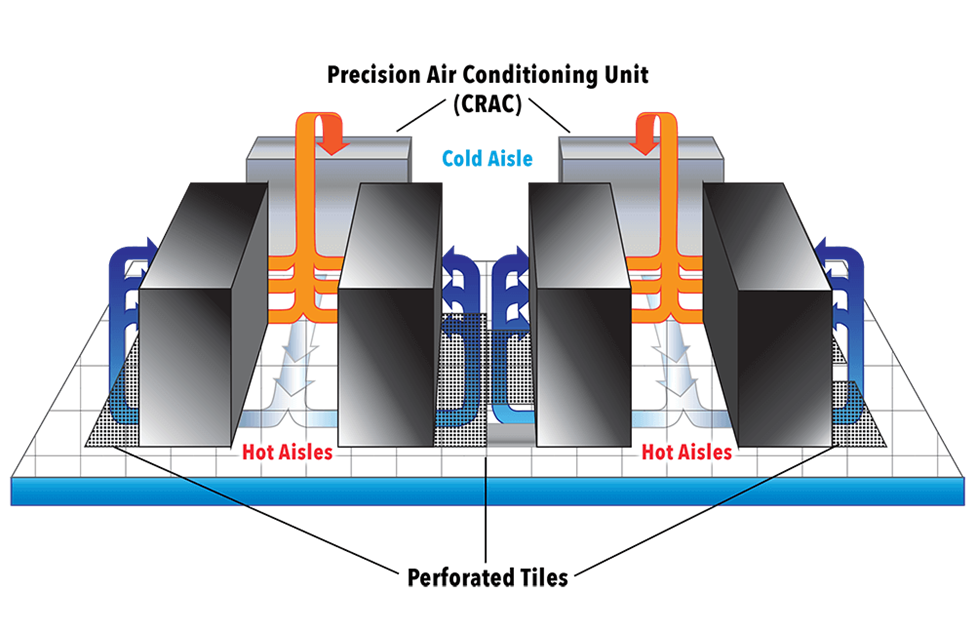
- HVAC – HVAC stands for Heating, Ventilation, and Air Conditioning. Engineers typically follow standards published by ASHRAE (American Society of Heating Refrigeration and Air Conditioning Engineers) when they design ventilation systems.
- Heating the room is not typically a concern because the equipment will generate more than enough heat. If the room needs to be heated, we need to determine how the building is heated
- If the building has a boiler (water is heated and pumped throughout the building), we will extend the heating loop into the room. This only provides heat.
- If the building has an air handling unit (air is heated and circulated throughout the building), we extend the duct work into the room. This provides heat and fresh air.
- We can install a portable heater.
- If the building has a boiler (water is heated and pumped throughout the building), we will extend the heating loop into the room. This only provides heat.
- Ventilation is a concern, but it depends on how much time people spend inside the room. If it is an MDF or IDF, it may not require much ventilation. It may be acceptable that the room receives fresh air through the doorway. If it is a data center, then fresh air is required. Fresh air can be pumped in through a make up air unit.
- Air Conditioning is a very important concern because the equipment will generate heat that needs to be removed. The air conditioner can also bring fresh air into the room.
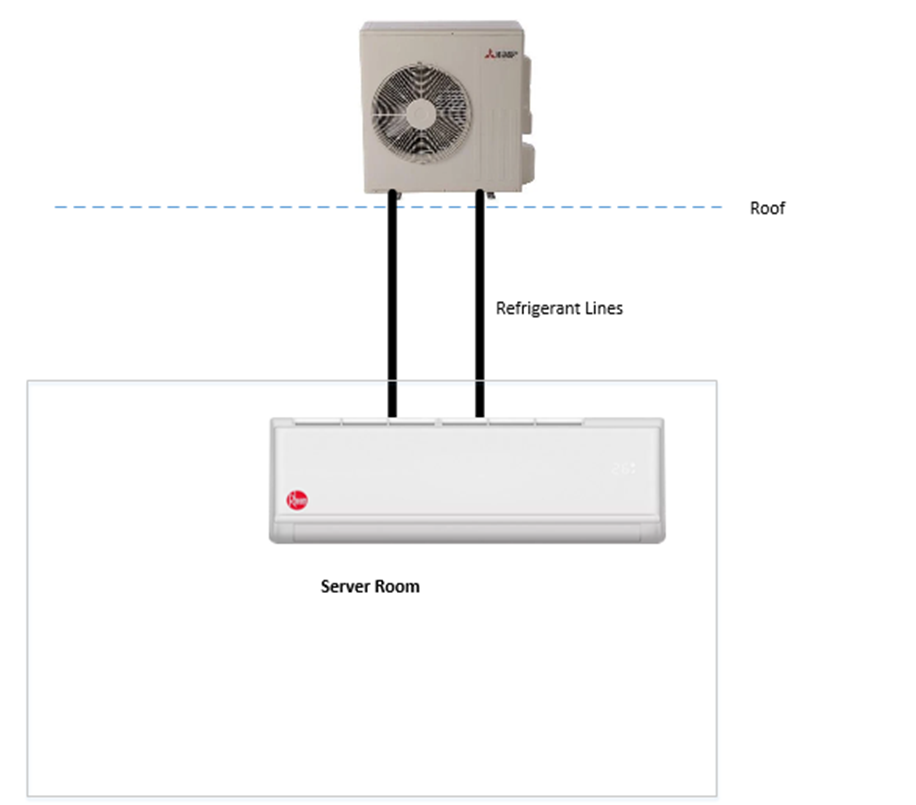
A typical setup for a small server room is to install a split system. It is technically a “heat pump,” not an air conditioner because it does not exchange any air with the outside world.
Inside the server room, we install an evaporator unit on the wall. On the roof, we install a condenser unit. The evaporator and condenser are connected with refrigerant lines.
The evaporator unit takes warm air from the room and extracts the heat. It empties the heat into a liquid called refrigerant. The warm refrigerant is pumped to the condenser on the roof, where the heat leaves. The refrigerant cools down and is pumped back into the server room.
- Heating the room is not typically a concern because the equipment will generate more than enough heat. If the room needs to be heated, we need to determine how the building is heated
- Fire Suppression – Fire Suppression is an important concern. How do we stop a fire?
- A fire extinguisher – the most basic fire suppression is to install a fire extinguisher. If a person sees a fire, and they can put it out safely, they can spray it with a fire extinguisher.
A fire extinguisher only prevents small fires that start when a person is watching. We must be careful to use an ABC fire extinguisher, which is one that can put out fires burning wood, flammable liquids, and electrical equipment.
A fire extinguisher must be inspected yearly.
- Sprinkler system – a traditional sprinkler system (also known as a wet pipe system) can automatically put out a fire. It consists of sprinkler heads that are installed throughout the building, connected to water pipes. The water pipes used for the sprinkler system are pressurized. Each sprinkler head contains a small piece of metal that melts under low temperatures (in the photo below it is red). If a fire occurs under the sprinkler head, the metal melts and water is released.
- A fire extinguisher – the most basic fire suppression is to install a fire extinguisher. If a person sees a fire, and they can put it out safely, they can spray it with a fire extinguisher.

A sprinkler system will put out the fire, but it will damage the equipment. We don’t want the sprinkler head to activate accidentally, and we can use the following measures- If we install a sprinkler head, we should install a cage around it so that it is not accidentally broken. If somebody breaks the sprinkler head, it will leak water.
- We can install high temperature heads in the server room. Sprinkler heads are manufactured to activate at different temperatures (100°F, 150°F, 225°F, etc). We should select a head that is rated for a high enough temperature so that it does not accidentally activate.
- We do not need to install a sprinkler system in a building that is not combustible (for example a building made of concrete). The actual determination of whether a building is combustible or non-combustible is complicated. It may be possible to build the server room out of materials that are fire rated, and then not have to install sprinkler heads (even if the rest of the building is sprinklered).
- We can install a pre-action system
- If we install a sprinkler head, we should install a cage around it so that it is not accidentally broken. If somebody breaks the sprinkler head, it will leak water.
- Sprinkler system with pre-action – a pre-action system is a system that does not activate until at least two signals trigger the system. We would install a normal sprinkler system. We would then install a heat detector in the server room, next to the sprinkler head. We would install a valve in the pipeline that feeds the sprinkler heads.
If the heat detector senses heat, it opens the valve and allows water to flow to the sprinkler head. If there is a fire, the sprinkler head melts and water is sprayed onto the fire.
If the heat detector does not sense heat, the valve remains closed and no water reaches the sprinkler head. The sprinkler head will not release any water, even if it is broken.- Dry system – a dry system is a sprinkler system that does not release water, but some other chemical such as Nitrogen or Carbon Dioxide. The gas flows through the entire room and forces the Oxygen out. Since fire needs Oxygen to continue burning, the lack of Oxygen puts out the fire.
A dry system is better because it can penetrate areas that water won’t. For example, if the fire starts at the bottom of the rack, underneath the UPS, the water from the sprinkler will not be able to reach it. The water will fall on top of the rack and puddle underneath the floor.
A dry system also won’t damage equipment.
We will need to install an alarm that warns people when the fire suppression system is activated so that they can quickly leave the room.
3M™ Novec™ 1230 Fluid is a special fluid that can put out a fire 50 times faster than a water-based system without damaging electronics.
The dry systems are more expensive than traditional sprinkler systems.
- Hypoxic system – a hypoxic system is one that reduces the level of oxygen in the room to a point where humans can breathe but a fire cannot start. Normal air is 21 percent oxygen, 78 percent oxygen, and 1 percent other gases.
If we change the air so that it is 15 percent oxygen and 85 percent nitrogen, then humans can breathe but a fire cannot start.
This system is currently not permitted by government regulations unless the employer provides workers with respirators, although studies have shown no adverse health effects.
This system is an active system because it must constantly remove oxygen from the air (fresh air coming from outside will continue to increase the oxygen levels).
- Sprinkler system with water mist – water mist systems are newer, but their popularity is increasing. A water mist system is one that generates an aerosol from the water instead of discharging a high-pressure stream.
The smaller droplets of water cool the air and create steam, which displaces the oxygen. This serves to put out the fire quickly. The mist also reduces the amount of water damage caused when compared with a traditional fire sprinkler system.
Water mist systems are more expensive than traditional systems. They may also be more expensive than pre-action systems.
- What type of fire suppression should you choose? Consider
- The cost of the sprinkler system, the cost of a fire damaging the equipment or burning down the building, the cost of the replacing the equipment, and the building codes
- It is better for the sprinkler system to damage the equipment in the server room than having a fire damage the equipment in the server room and spreading to the rest of the building
- It is always cheaper to design the sprinkler system before the building is built
- Always have a fire extinguisher handy – it is usually required by the local fire code. The fire extinguisher should be mounted to the wall and have a sign that people can see.
- If your building is still under construction or in the design phase and non-combustible, it will not have a sprinkler system
- Consider having the MDF and IDF built out of materials that can withstand a fire for one hour or two hours
- A dry or water mist sprinkler system may be installed only for the IDF and MDF. This will protect the equipment if a fire starts in one of these rooms. The cost of a dry system for a single room will not be much more than the cost of a traditional system for a single room.
- Consider having the MDF and IDF built out of materials that can withstand a fire for one hour or two hours
- If your building is still under construction or in the design phase, and combustible, it will have a sprinkler system
- If your building code allows it, you may build the IDFs and MDF out of materials that can withstand a fire for at least two hours, and not have a sprinkler head in those rooms
- Otherwise, you may be required to extend the sprinkler system into the IDF and MDF. This type of sprinkler system will damage the equipment. It is unlikely that the entire building will have a dry system.
- A dry or water mist sprinkler system may be installed only for the IDF and MDF. This will protect the equipment if a fire starts in one of these rooms, but the cost may be too high. It may cost $30,000 to install a dry system in a single room, so the business must consider whether the cost outweighs the risk.
- If your building code allows it, you may build the IDFs and MDF out of materials that can withstand a fire for at least two hours, and not have a sprinkler head in those rooms
- If your building is existing construction and non-combustible, then the building will not have a sprinkler system
- The business must consider whether they need a fire suppression system for the IDFs and MDF.
- Since only a single room is affected, the cost of a traditional system may be almost as much as the cost for a dry system.
- The business must consider whether they need a fire suppression system for the IDFs and MDF.
- If your building is existing construction and combustible, it will already have a sprinkler system that extends into the IDFs and MDF
- The existing sprinkler system will likely be a traditional system.
- Consider whether you can use fire proof materials to insulate the rooms and remove the sprinkler heads, and whether the cost is worth the reduction in the risk.
- Consider whether the cost of replacing the existing sprinkler heads with a pre-action or dry system is worth the reduction in risk of damaging the equipment
- The existing sprinkler system will likely be a traditional system.
- The cost of the sprinkler system, the cost of a fire damaging the equipment or burning down the building, the cost of the replacing the equipment, and the building codes
- Dry system – a dry system is a sprinkler system that does not release water, but some other chemical such as Nitrogen or Carbon Dioxide. The gas flows through the entire room and forces the Oxygen out. Since fire needs Oxygen to continue burning, the lack of Oxygen puts out the fire.
- Flood Protection. There are three considerations
- The data center should be built on a raised floor. In the event of a flood, water will drain below the equipment
- Do not run water pipelines through the data center if possible. This factor depends on the size of the data center, and the location in the building.
- Install moisture alarms. These detect moisture/water and can alert a supervisor to take further action.
- The data center should be built on a raised floor. In the event of a flood, water will drain below the equipment
Equipment should be
- Installed by a trained professional
- Maintained regularly
- Tested to ensure that it is operational and working correctly
- Monitored so that alerts can be identified and responded to
We should also use an Uninterruptable Power Supply (UPS). The UPS is a battery that provides power to our computer equipment in the event of a power outage. The UPS might be a standalone system or part of the building’s electrical system. We should select a UPS that is adequate for the equipment that we want to protect. We also need to protect against power surges.
Some Common Power Terms
- Fault – a momentary loss of power
- Blackout – a prolonged loss of power. A blackout can force equipment to shut down.
- Sag – a momentary low voltage. A sag can force equipment to shut down.
- Brownout – a prolonged low voltage. A brownout can force equipment to shut down.
- Spike – a momentary high voltage. A spike can damage equipment.
- Surge – a prolonged high voltage. A surge can damage equipment.
- Inrush – a power surge that occurs when connecting to a power source.
- Noise – a fluctuation that causes electromagnetic interference. Noise can cause disruption to Wi-Fi or other electromagnetic signals. We want to protect against noise.
- Transient – a small amount of noise.
- Clean power – a power supply that does not fluctuate
- Ground – a wire that is electrically grounded and protects against short circuits
Emanation Security – how do we keep radiation from leaking out of our facility? Electromagnetic radiation can be intercepted and converted into usable data.
- A Faraday Cage protects against electromagnetic radiation. We would line the walls of sensitive areas with a mesh that absorbs the radiation.
- White Noise is the generation of random audio or electromagnetic radiation. The random radiation mixes with the legitimate radiation, so that spies on the outside cannot figure out what is real and what is fake.
Let’s look at some types of rooms and what security measures each of them requires
- Wiring closets/intermediate distribution facilities
- A wiring closet may contain cross-connects, patch panels, and switches.
- The wiring closet should maintain at least a one-hour fire rating
- There should be a secure door with an electronic access control system. Only authorized people should be permitted to access the closet, and all access attempts should be logged.
- The facility should be equipped with cameras at each entrance, and cameras in the interior.
- The facility should be equipped with a dry fire suppression system.
- The facility should be equipped with an intrusion alarm and motion sensors.
- Equipment should be powered by a UPS. If it is critical, the UPS should be connected to a generator.
- We may also need to install a humidifier.
- In a building with multiple tenants, if the wiring closet contains equipment or wiring belonging to the internet service provider or telecommunications provider, it might be known as the demarc (demarcation point), MPOE (Minimum Point of Entry), MPOP (Minimum Point of Presence), or POP (Point of Presence).
- It is possible that multiple tenants need access to the facility
- It is possible that the ISPs and their contractors need access to the facility
- A tenant, ISP, or contractor could cause damage to the equipment belonging to another ISP or tenant
- Thus, we need to control access to the facility. We only permit specific qualified individuals to access the wiring closet. We may require them to provide background checks and insurance.
- Wiring closets can become messy. We need to ensure that proper cable management is followed.
- It is possible that multiple tenants need access to the facility
- A wiring closet may contain cross-connects, patch panels, and switches.
- Server rooms/data centers
- A server room may contain servers, storage appliances, routers, and other dedicated appliances, in addition to cross-connects, patch panels, and switches.
- The facility should maintain at least a one-hour fire rating
- Care must be taken to ensure that the facility does not use the server room for general storage
- There should be a secure door with an electronic access control system. Only authorized people should be permitted to access the facility, and all access attempts should be logged.
- The facility should be equipped with cameras at each entrance, and cameras in the interior.
- The facility should be equipped with a dry fire suppression system.
- The facility should be equipped with an intrusion alarm and motion sensors.
- Equipment should be powered by a UPS. If it is critical, the UPS should be connected to a generator.
- A raised floor to protect against flooding (with static dissipating tiles)
- If the facility needs additional protection, we may do the following
- Install a man trap at each entrance
- Have roving security patrols
- Install a man trap at each entrance
- If the facility is a standalone data center
- Install bollards and barricades
- Install a security fence around the facility
- Have security guards check all vehicles and deliveries
- Install bollards and barricades
- A server room may contain servers, storage appliances, routers, and other dedicated appliances, in addition to cross-connects, patch panels, and switches.
- Media storage facilities
- A media storage facility keeps back ups of data, and also stores blank media. We should protect blank media because hackers can introduce malware into it.
- The facility should maintain at least a two-hour fire rating
- There should be a secure door with an electronic access control system. Only authorized people should be permitted to access the facility, and all access attempts should be logged.
- The facility should be equipped with cameras at each entrance, and cameras in the interior.
- The facility should be equipped with a dry fire suppression system.
- The facility should be equipped with an intrusion alarm and motion sensors.
- A raised floor to protect against flooding. Water pipes should be routed away from the facility.
- We must keep track of all the media in the facility, and we must keep track of when it is removed. We may track the media via barcodes or RFID.
- We may take precautions to reduce the presence of magnetic fields
- A media storage facility keeps back ups of data, and also stores blank media. We should protect blank media because hackers can introduce malware into it.
- Evidence storage
- An evidence storage facility must be able to maintain a chain of custody. That means we must always be able to prove that we know where the evidence was stored and that nobody had the opportunity to tamper with it.
- The facility should maintain at least a two-hour fire rating
- There should be a secure door with an electronic access control system. Only authorized people should be permitted to access the facility, and all access attempts should be logged.
- The evidence storage facility should always be staffed by one or two security guards. When we need to remove evidence from the facility, the security guard logs the removal, and verifies that we are entitled to remove that piece of evidence. The security guard can be called to testify about the chain of custody.
- The facility should be equipped with cameras at each entrance, and cameras in the interior.
- The facility should be equipped with a dry fire suppression system.
- The facility should be equipped with an intrusion alarm and motion sensors.
- An evidence storage facility must be able to maintain a chain of custody. That means we must always be able to prove that we know where the evidence was stored and that nobody had the opportunity to tamper with it.
- Restricted and work area security
- The Reception area can include public restrooms and a public telephone. The reception area is not secure.
- The reception area is separated from the work area by a door with an access control system.
- It may also have cameras.
- The reception area will have plexiglass to protect against respiratory diseases.
- The reception area will have HVAC and a fire suppression system as required by local building codes.
- The reception area is separated from the work area by a door with an access control system.
- Sensitive areas are areas where the work is completed. All employees potentially have access to sensitive areas. We might limit an employee’s access to only the specific areas that they require and only at specific times.
- The sensitive areas have access control systems, alarms, motion sensors, and cameras.
- The sensitive areas will have HVAC and a fire suppression system as required by local building codes.
- We might install walls or partitions to keep people from eavesdropping on others. Some companies use open office concepts that do not provide much security.
- The sensitive areas have access control systems, alarms, motion sensors, and cameras.
- Access to highly sensitive areas such as server rooms are restricted to the people who require access.
- When we must access or store classified material, we use a Sensitive Compartmented Information Facility or SCIF. A SCIF is a specially designed room that allows us to discuss classified material without the risk of it leaking. Only specific people with the necessary security clearances can access the SCIF.
- The requirements for a SCIF are published by the government.
- The requirements for a SCIF are published by the government.
- We should escort visitors when they need to access secure areas. A better approach is to install conference or meeting rooms in the public area so that visitors do not need to enter the secure area.
- The visitor policy might include
- Verify that the visitor has a legitimate reason for accessing the facility.
- Verify that the visitor has a sponsor (an employee that the visitor is seeing).
- Determine the specific areas that the visitor is going to access.
- Provide the visitor with a badge.
- Sign the visitor in and out.
- Ensure that the visitor is wearing proper PPE as required to access the facility (if it is hazardous).
- Provide the visitor with some training
- General rules about the facility
- Location of the exits, washrooms, first aid kits, and other emergency supplies
- What to do in the event of an emergency
- General rules about the facility
- Have the visitor sign a non-disclosure agreement
- Perform a background check on the visitor prior to his arrival
- Search the visitor upon arrival to make sure he does not have any weapons or recording devices
- Search the visitor when he leaves
- COVID-19 screening on the visitor upon arrival
- Verify that the visitor has a legitimate reason for accessing the facility.
- The Reception area can include public restrooms and a public telephone. The reception area is not secure.
