1.3 Given a scenario, use features and tools of the Microsoft Windows 10 operating system (OS)
- Task Manager
- Services
- Startup
- Performance
- Processes
- Users
- Microsoft Management Console (MMC) Snap-In
- Event Viewer (eventvwr.msc)
- Disk Management (diskmgmt.msc)
- Task Scheduler (taskschd.msc)
- Device Manager (devmgmt.msc)
- Certificate Manager (certmgr.msc)
- Local Users and Groups (lusrmgr.msc)
- Performance Monitor (perfmon.msc)
- Group Policy Editor (gpedit.msc)
- Additional Tools
- System Information (msinfo32.exe)
- Resource Monitor (resmon.exe)
- System Configuration (msconfig.exe)
- Disk Cleanup (cleanmgr.exe)
- Disk Defragment (dfrgui.exe)
- Registry Editor (regedit.exe)
Let’s look at some built in features of the Windows Operating System.
Task Manager – Applications, Processes, Performance, Networking, Users
Features of the Task Manager Applications (now known as Processes) tab
- Lists each running application
- For each application, it lists the current CPU, Memory, Disk, and Network usage
- Lists the total CPU, Memory, Disk, and Network usage (as a percentage of their capacity)
- Can show us if a specific application is hogging resources
- We can use the Task Manager to end an application
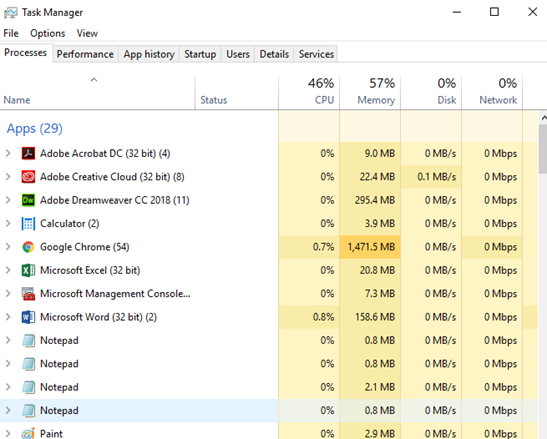
In newer versions of Windows, the Processes tab lists Applications and Background Processes.
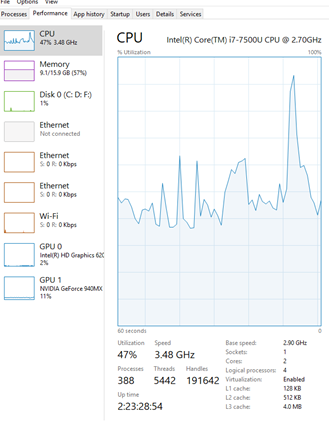
The Performance tab shows us the performance of the computer in a graphical interface.
The Users tab shows a list of users who are logged in. For each user, it shows the applications that the user is running, and the resources that each of the applications is using.
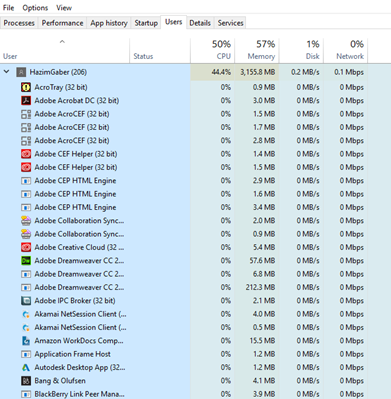
The Details tab (also known as the processes tab on older versions of Windows) shows a list of running processes. For each process, it shows the Process ID, the status, the user who is running the process, and the CPU/memory utilization. A process could be an application or a service. We can end a process or view the location of the file that contains the process.
Administrative Tools – Computer Management
The second tool is the Microsoft Management Console (MMC). This tool allows us to manage the operating system. Within this tool, we can launch several components (or we can launch them separately by typing in their file name). They are
- Event Viewer (eventvwr.msc)
- Disk Management (diskmgmt.msc)
- Task Scheduler (taskschd.msc)
- Device Manager (devmgmt.msc)
- Certificate Manager (certmgr.msc)
- Local Users and Groups (lusrmgr.msc)
- Performance Monitor (perfmon.msc)
- Group Policy Editor (gpedit.msc)
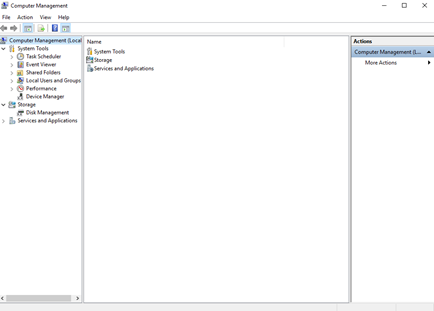
Administrative Tools – Device Manager
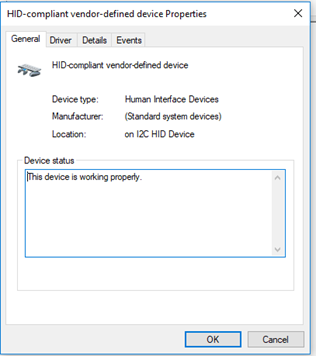
The Device Manager shows us a list of devices connected to the computer (internal and external). Devices are categorized by type. We can use Device Manager to view, disable, enable, or configure devices.
Click on a device to see its status, drivers, and settings. The settings vary from device to device. You can also update or roll back the device driver.
When you install a new device, Windows attempts to install the correct driver automatically. If this process malfunctions, you may need to visit the device manager to manually change the driver.
Administrative Tools – Local Users and Groups
Local Users and Groups shows us local users and groups. We can use Local Users and Groups to view, create, delete, or disable user accounts.
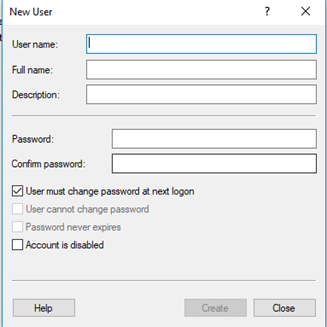
It is only available in Windows Pro versions. We can create a user or a user group
- A group is a set of users with specific privileges
- We can add a user to one or more groups. We can add multiple users to each group.
- We can assign various privileges to the group
- The two default groups are users and administrators. If we have many users, we may want to have more granular control on what each one can do.
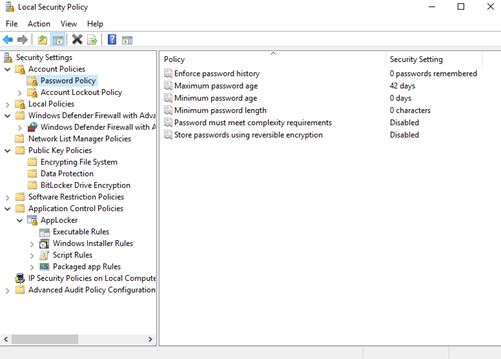
Administrative Tools – Local Security Policy
Local Security Policy allows us to set security policies on the computer. Policies are categorized by type. We can use Local Security Policy to create or modify security policies.
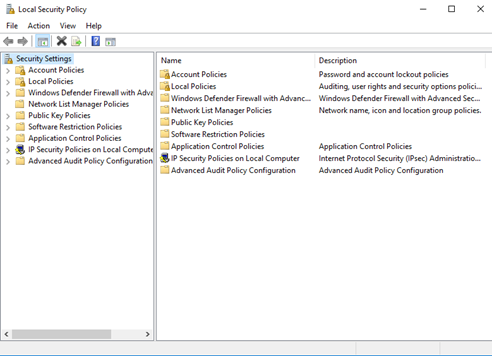
Some policies are predefined but can be edited (for example, password policy).
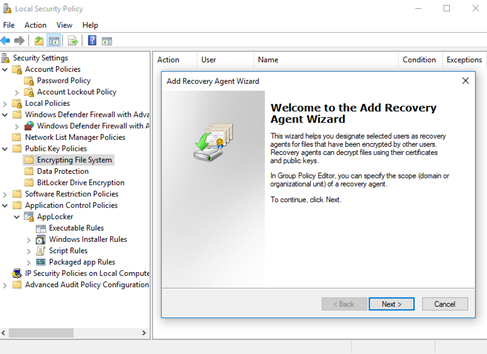
Other policies can be created through a wizard.
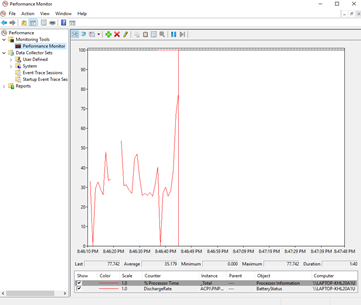
Administrative Tools – Resource & Performance Monitor
The Performance Monitor allows us to monitor different system resources. We can use the performance monitor to measure system resources, which could identify sources of error or poor performance. The Resource Monitor provides a summary of this information.
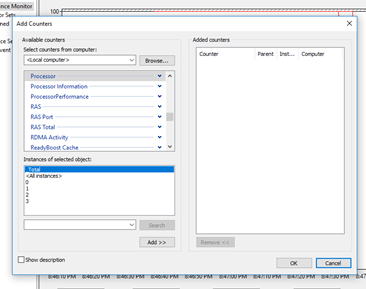
We can tell the performance monitor which processes we want to track, and which attributes of each process we want to track.
Administrative Tools – Services
Services shows us all the installed services. A service is a program that runs in the background. It usually starts when Windows starts, but it can be triggered to start by something else.
We can use Windows Services to view, start, stop, restart, or disable services. Services can cause errors or impact performance.
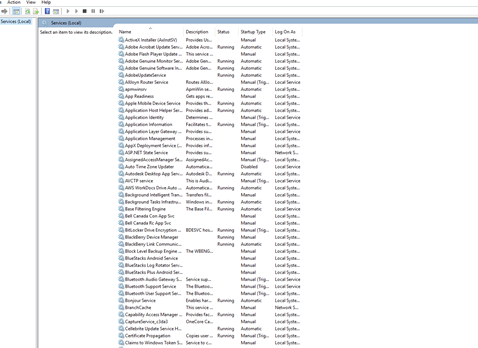
A service may have dependencies – other services that must operate in conjunction with it. A service may not be able to start without dependencies.
Administrative Tools – Task Scheduler
The Task Scheduler allows us to create, delete, or modify automated tasks. For example, we might create a task to automatically run a backup program each day.
A task must have a name and may have a description.
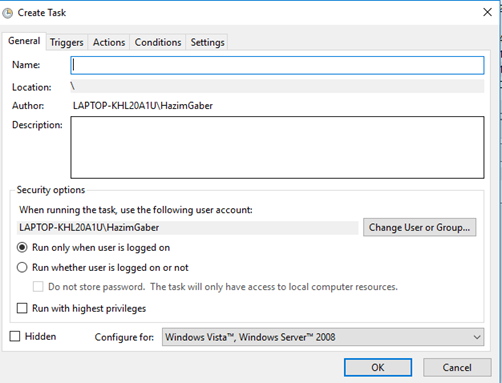
A task will have one or more triggers. A trigger is a scenario or event that causes the task to execute. A trigger could be a time (the task may run daily, hourly, weekly, on weekdays, etc.).
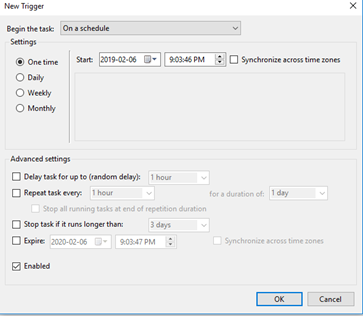
A trigger could be an event (for example, system start up, network connection, program crash).
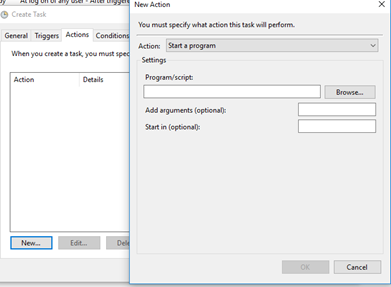
A task will have one or more actions. An action is something that the task must do (run a program, establish a connection, execute a script, etc.).
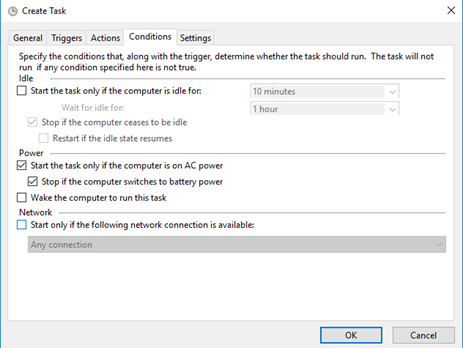
We can also set conditions for the task. We can choose to run the task only when the computer is idle, only when the computer is connected to AC power, and/or only when the computer is connected to the internet.
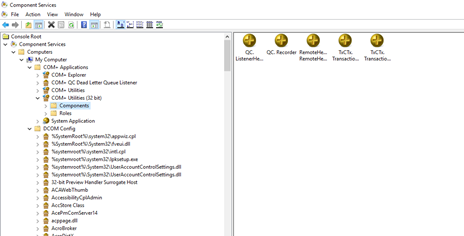
Administrative Tools – Component Services
Component Services manages COM+ and DCOM components. COM+ and DCOM are Windows plug ins that allow developers to create applications that run smoothly and scale better.
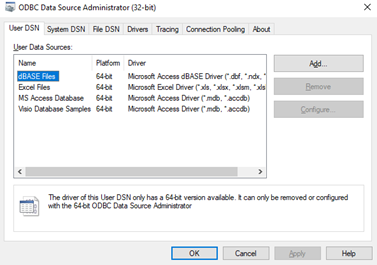
Administrative Tools – Data Sources
Data Sources lists the databases that the computer can connect to.
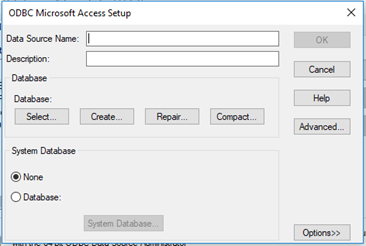
We can add a new database to the system by specifying the database type, name, and location. Once a database is added to the data source, other applications can connect to the database by simply mentioning its name.
Administrative Tools – Print Management
Print Management allows us to view and delete printers installed on the computer. Sometimes, removing or renaming a printer from the Devices & Printers menu will fail. If it does, visit Print Management and try again.
Administrative Tools – Windows Firewall
The Windows Firewall allows us to set rules that permit or deny network traffic from entering or leaving our computer. The Firewall may be disabled and managed by an antivirus application (such as Norton Antivirus)
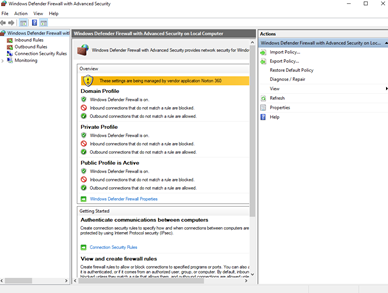
- We can create an Inbound Rule
- Affects traffic that is entering our computer
- Affects traffic that is entering our computer
- We can create an Outbound Rule
- Affects traffic that is leaving our computer
- Affects traffic that is leaving our computer
- A rule can be set to block traffic (a blacklist) or allow traffic (whitelist)
- We can use a wizard to create rules
- We can block/allow traffic from a specific program, port, IP address, or a combination of these
- When you install a program, it might automatically add rules to the firewall, so that it can operate properly
Administrative Tools – Event Viewer
The event viewer shows us a list of events (automatically logged by Windows). We can use the event viewer to identify the source of errors.
Events are generated by the System, by Security issues, and by Applications. An event can be a piece of information, a warning, an error, or a critical error. We can filter by the type of error, the source, or the date/time that it occurred.
msconfig – General, Boot, Services, Startup, Tools
When Windows boots, it loads
- Drivers for all the installed hardware components
- The programs that are listed in the Startup list
- All the services that are set to run automatically
Drivers, programs, and services can cause errors.
In msconfig, the general tab has three options
- Normal Startup loads all start-up items (drivers, programs, and services)
- Diagnostic Start-up loads only basic start-up items and services (we can use this to disable many drivers and start-up items, and then enable them one by one to see which one is the cause of the error)
- Selective Start-up lets us choose whether to load system services and/or start-up items
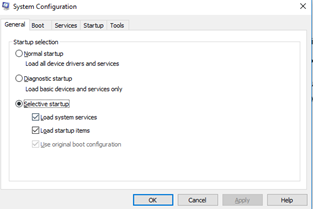
The boot tab allows us to choose advanced boot settings
- Boot in Safe Mode with minimal features
- Boot from an Alternate Shell (a command prompt)
- Boot from the Network
- We can choose to boot into Safe Mode if we have a problem with the operating system
- Safe mode boots with minimal features running
- We can then enable features one at a time to determine which one is causing the issue
- Safe Mode is available as
- Safe Mode
- Safe Mode with Networking – like Safe Mode but allows the network to function
- Safe Mode with Command Prompt – only loads the command line
- Safe Mode
- We also have the option to
- Enable Low-Resolution Video – allows us to repair issues caused by bad display drivers
- Enable Boot Logging – creates a log file of the drivers when they load; this allows us to diagnose issues caused by bad drivers
- Enable Low-Resolution Video – allows us to repair issues caused by bad display drivers
- Safe mode boots with minimal features running
- We can also choose to limit the number of processors or amount of memory in use
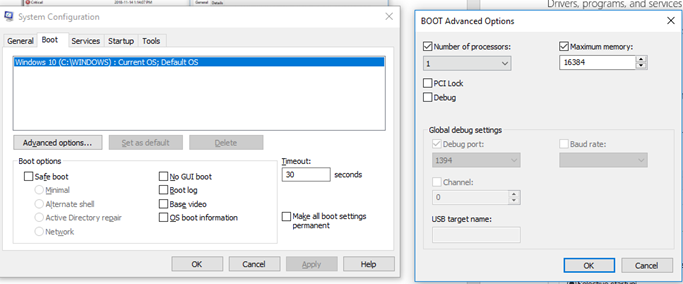
The services tab allows us to enable or disable services
The Startup tab lists all the applications that start up when the computer starts
- In newer versions of Windows, the Startup tab is in the Task Manager
- The Startup tab also lists the impact each item has on the computer’s performance (may not be completely accurate)
- You can enable or disable each item
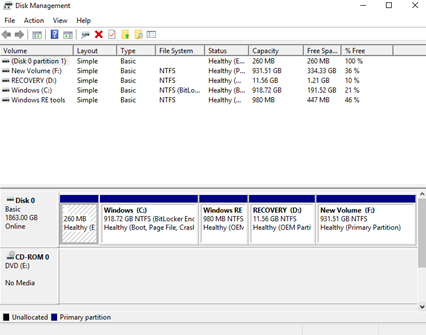
Disk Management – Drive Status, Mounting, Initializing, Extending Partitions, Splitting Partitions, Shrink Partitions, Assign/Change Drive Letters, Add Drives, Add Arrays
Disk Management shows us a list of physical disks, and how they are partitioned.
- At the top, we can see a list of every partition, the type of partition (Basic or Dynamic), the File System, the Status, the Capacity, and the amount of Free Space
- At the bottom, it shows us each disk, its capacity, and a layout of the partitions (remember that partitions must be contiguous on a basic drive)
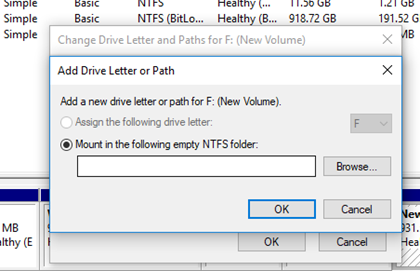
- We can add a drive letter to a partition
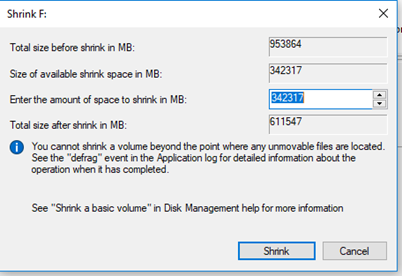
- We can shrink a volume by up to the maximum amount of free space available. For example, if the volume is 1000MB, with 250MB of free space, then we can shrink it by up to 250MB.
- We can increase the size of a partition.
- There must be free space available on the drive
- The free space must be to the right of the partition because partitions must be contiguous. If you want to add a non-contiguous partition, you must use some advanced software.
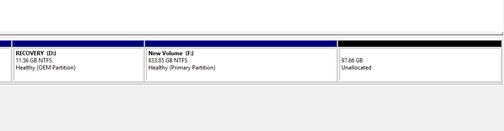
- For example, in the photo, we can increase the Volume F by 97.66GB (since we have 97.66 GB to the right of Volume F).
- We can’t increase Volume D, or add the 97.66GB to volume D, because there is no free space to the right of Volume D.
- We can also turn the 97.66GB into one or more new volumes.
- There must be free space available on the drive
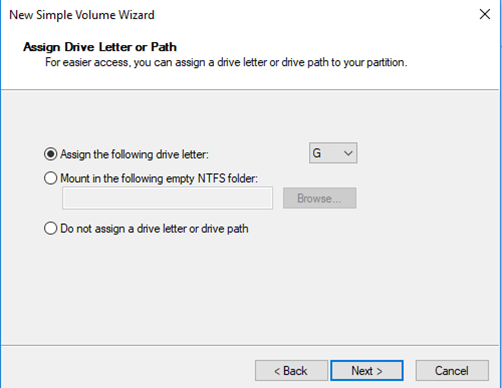
- We can create a new volume from some unallocated free space
- We can choose to
- Assign a drive letter (from a list of available letters)
- Mount the drive as a folder in another drive. For example, a drive can be mounted as, C:\My Documents\. Then the data stored in C:\My Documents is stored in a separate drive.
- Assign a drive letter (from a list of available letters)
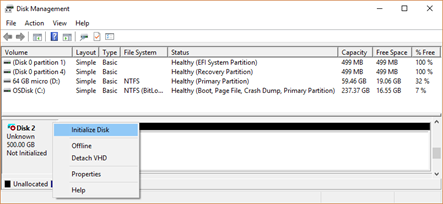
- If we install a new physical disk, it will appear in Disk Management
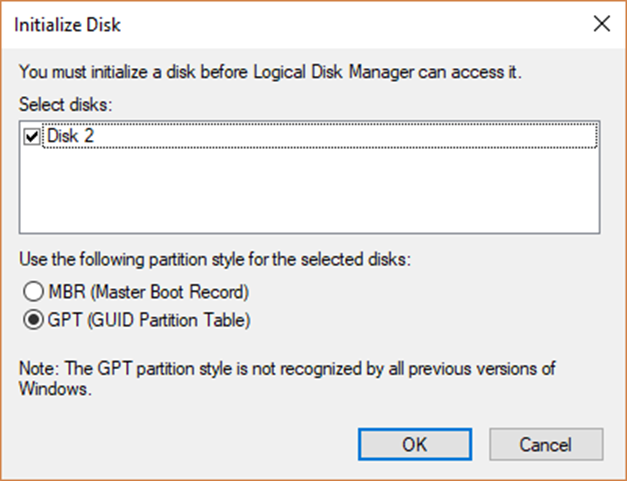
- Choose to initialize the disk either as a GPT or MBR
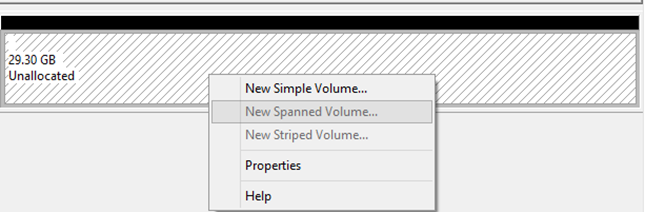
- To create a RAID array
- Choose a New Spanned Volume
- Then choose the type of RAID
- Choose a New Spanned Volume
Disk Status
The different disk statuses are
- Foreign Drive – a dynamic disk from another computer will show up as “foreign”
- Formatting – a disk that is being formatted
- Failed – a disk that is physically damaged or corrupted
- Online – a disk that is working and in use
- Offline – a disk that is damaged or corrupted; in particular, having communication problems
Disk Management isn’t always the best tool for managing disks. Consider using a commercial tool for more advanced operations.
System Utilities – Regedit
Regedit is the Windows Registry Editor. It requires admin privileges to operate. Regedit contains system, user, and application settings & preferences
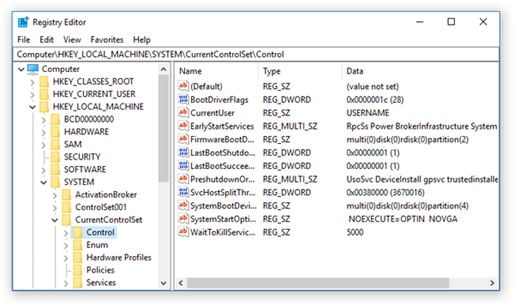
- The registry is hierarchical (it contains keys, which are like folders)
- Keys store values: each value contains a single setting
- There are several types of values
- String value – strings are flexible; any type data can be stored
- Binary value – binary values can store only a zero or a one
- DWORD value – A DWORD can store a 32-bit binary (ones and zeroes) value
- QWORD value – A QWORD can store a 64-bit binary (ones and zeroes) value
- There are five main keys
- HKEY_LOCAL_MACHINE: contains computer settings
- HKEY_CURRENT_CONFIG: contains information generated at boot time (this information is regenerated each time the compute reboots)
- HKEY_CLASSES_ROOT: contains information about applications
- HKEY_USERS: contains settings for all users
- HKEY_CURRENT_USER: contains settings for the user who is logged in
- It’s possible to store a registry value inside a registry file. You can export a registry key for back-up purposes. The back-up contains the value of the key and its location. Double-clicking on the file adds it to the registry.
System Utilities – Group Policy Editor
The Group Policy Editor shows us all the group policies that apply to our computer and user profile. You must have administrative rights to even view the group policy editor.
We can edit the group policy on our local computer, but the server group policy will always override the local group policy. If we add a local policy that is not on the active directory server, then the local policy will continue to apply.
System Utilities – Certificate Manager
The Certificate Manager shows us all the certificates that are present on our computer. A computer (or user) uses certificates to authenticate itself with external resources.
We can install new certificates by importing them into the certificate manager. We may also be able to export certificates if we have permission.
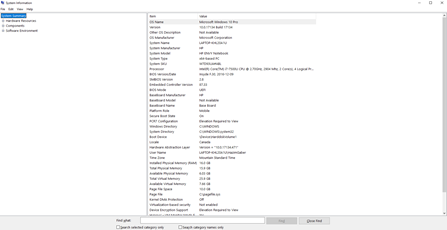
System Utilities – System Information
msinfo32 provides information about the computer. It includes the operating system version, the processor type, and the amount of RAM. It also lists the hardware installed and the details about the software environment.
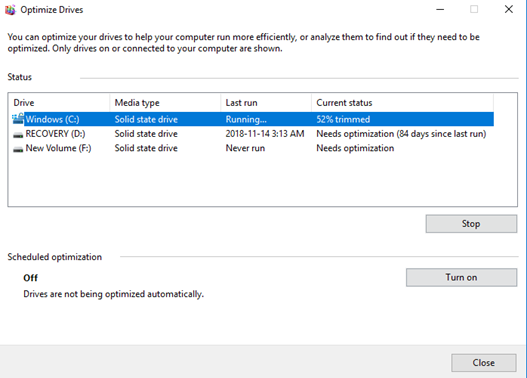
System Utilities – Disk Defragmenter
The Disk Defragmenter allows you to defragment your disk. A disk becomes fragmented when files are stored in multiple pieces in different parts of the drive (instead of being stored contiguously). This only happens on a magnetic hard drive. A fragmented disk performs poorly. The defragmenter locates file fragments and puts them back together.
The defragmentation process can be run when the computer isn’t busy.
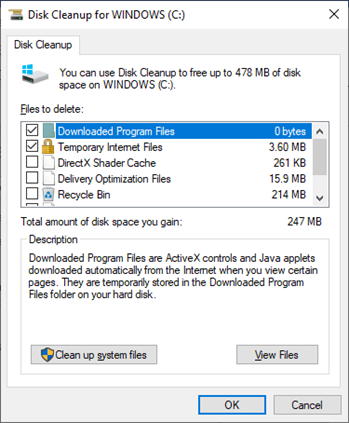
System Utilities – Disk Clean Up
The Disk Clean Up Utility identifies unnecessary files that are taking up space and allows us to delete them.