2.5 Given a scenario, manage and configure basic security settings in the Microsoft Windows OS
- Defender Antivirus
- Activate / Deactivate
- Updated Definitions
- Firewall
- Activate / Deactivate
- Port Security
- Application Security
- Users and Groups
- Local vs Microsoft Account
- Standard Account
- Administrator
- Guest User
- Power User
- Login OS Options
- Username and Password
- Personal Identification Number (PIN)
- Fingerprint
- Facial Recognition
- Single Sign-On (SSO)
- NTFS vs Share Permissions
- File and Folder Attributes
- Inheritance
- Run as Administrator vs. Standard User
- User Account Control (UAC)
- BitLocker
- BitLocker To Go
- Encrypting File System (EFS)
Defender Antivirus
Microsoft Windows Defender is a built-in antivirus program. It is automatically activated and receives regular updates. When you have a third-party antivirus program, it will disable Windows Defender. You can check the status of Windows Defender from the Windows Security menu.
Microsoft Windows Defender firewall is a built-in firewall program, as previously discussed. The firewall is automatically activated unless you have a third-party software firewall. In general
- You can enable all outbound traffic.
- A firewall rule should be as specific as possible. Each application that requires incoming traffic should have a rule permitting it access to the specific ports that it requires. You should not create any rules that allow incoming traffic on all ports or for all applications.
- Regularly review the firewall rules and remove unnecessary rules.
User and Groups
Remember that in Active Directory, a user account can be assigned to a group. Groups make it easier for us to manage users. A user account inherits the privileges assigned to the group. A user can belong to multiple groups. Some of the most common groups are in the table below (a large organization can have thousands of groups).
| Administrator | Also known as a Superuser There can be multiple administrator accounts, and there can be a hierarchy of administrator accounts. On a local Windows computer, there must be at least one administrator account. Ad admin account Can create other accountsInstall programsChange settingsView files (documents, desktop, etc.) belonging to all users A program must ask for permission when it attempts to run with administrator privileges. |
| Power User | A Power User is more powerful than a Standard User, but less powerful than an administrator. A Power User can’t view files belonging to other users. Power User accounts should be granted to more experienced users only. Power User accounts were present in Windows XP and then removed. |
| Standard user | A Standard User can log in, run programs, edit files, and perform general tasks A Standard User can’t -Create other user accounts -Install programs -Change advanced system settings -View files (desktop, documents, etc.) that belong to other users If the account is an Active Directory account, more granular permissions are available. |
| Guest | The guest account is not assigned to a specific person. It is disabled by default. The guest account allows anybody to access the computer without a password. A Guest account can’t -Store data -Create other user accounts -Install programs -Change advanced system settings -View files (desktop, documents, etc.) that belong to other users |
Microsoft is trying to get everybody to sign in with a Microsoft Account. A Microsoft Account is connected to an e-mail address, and its credentials are stored on the Microsoft server. When you set up your Windows 10 or Windows 11, Microsoft will force you to log in with a Microsoft Account (or create a new one).
After you log in with a Microsoft Account, you can disable it and switch to a local account. There is also a command that you can type to bypass the Microsoft Account setup and use a local account. If your computer is connected to a domain, then you don’t need to use a Microsoft Account.
Login Options
There are several ways to log in to Windows
- Username and Password. This is the most common way to log in to Windows. You must enter your username and password. The username and password may be stored on the local computer or on a central server.
- Personal Identification Number (PIN). A Windows PIN is more secure than a password because the PIN is only stored on the computer and not a central server. A PIN can be as complex as a password. The PIN is stored by the TPM.
- Fingerprint. You can sign into Windows with your fingerprint if your computer has a fingerprint reader. You must first register the fingerprint with the computer. You must also have a PIN set up for the fingerprint access to work.
- Facial Recognition. You can sign into Windows with your face if your computer has a webcam. You must first register your face with the computer. You must also have a PIN set up for the facial recognition to work.
- Single Sign On (SSO). Single Sign On allows us to log in to multiple applications with the same set of credentials. When you log in to your Windows computer, it logs you in to other applications used by your organization.
NTFS File Permissions
Let’s take a look at how file permissions work in Windows.
| Ownership | The owner of a file or folder is the user that created it. The owner has full control over the file or folder. The owner can prevent other users (even administrators) from viewing files/folders that the own. |
| Take Ownership Permission | A user with the Take Ownership Permission can take ownership of a file or folder. An administrator can take ownership of any file or folder by default. If the owner of a file has prevented others from seeing it, then administrators cannot see it. But an administrator can take ownership of the file and then see it. |
| Change Permission | An account with the Change Permission feature can give other users permission or take it away |
| Allow vs Deny | A folder or file will inherit permissions from the folder that it is in. For example C:\folder1\folder2 will inherit permissions from C:\folder1 A sub-folder will stop inheriting permissions if different permissions are set on it. In the folder security tab, you can set “allow” permissions and “deny” permissions for the ability to modify, read, read & execute, or write A deny permission will override an allow permission. Why do we need both allow and deny? It’s possible to give permission to a user or to a group of users, and then take it away from specific users in the group. For example, we don’t want the Accountants group to have access to “Folder1”. We would add Accountants and check the Deny boxes. But Bob is an Accountant and we want to provide him with access. We would add Bob and check the Allow boxes (the Allow overrides). Or we want the Engineers group to have access to “Folder1”. We would add Engineers and check the Allow boxes. But John is an Engineer, and we don’t want to provide him with access. We would add John and check the Deny boxes (the Deny overrides). |
| Moving vs Copying files and folders | When you move a protected file or folder, it retains its current permissions. When you copy a protected file or folder, it inherits the permissions from the folder that you copied it into. But, if you copy or move a protected file or folder from one volume to another, the object will inherit the permissions from the new location. |
| File Attributes | The standard NTFS file attributes are File name Security descriptor (who owns the file and who can access it) Object ID (unique file ID) Data (other unique file attributes) Standard Information (date and time stamp) |
| NTFS Folder Permission | Permissions that can be applied to a folder Full Control – we can do anything Modify – read, write, and delete files/folders Read & Execute – read only, and execute programs List Folder Contents – view folder contents Read – view folder contents and open files Write – write to files and create new files/folders Folder permissions are inherited by default. Permissions applied to a folder are inherited by the folder’s contents (file and subfolders). |
| NTFS File Permissions | Permissions that can be applied to a file Full Control – we can do anything Modify – read, write, and delete Read & Execute – open and/or run the file Read – view the file Write – open and write to the file |
Run as Administrator vs Standard User
On older versions of Windows (such as Windows XP), when you ran an application, it would run at the level of the user.
- If the user is an administrator, the application will run with administrator privileges
- If the user is a standard user, the app will run with standard privileges
Allowing all applications to run with administrator privileges is a bad idea. Why?
- An application running as an administrator can do anything it wants. A virus could hijack the application, and now the virus can do anything it wants.
- Some applications require administrator privileges to operate. They might need to save files to protected directories and/or modify system settings.
- On newer versions of Windows, UAC (User Account Control) will prompt the user to choose whether to allow an application to run with administrator privileges. UAC can be disabled, but this is not recommended.
- A standard user can run an application as an administrator by entering an administrator username and password.
- It is possible to set a program to always run as an administrator.
BitLocker
BitLocker is an encryption protocol built into Windows Pro. It provides full-disk encryption.
If the computer contains a TPM, the encryption key can be stored inside the TPM. We can also store the encryption key in Active Directory.
The computer can load to Windows, but none of the additional files are decrypted until the user successfully logs in. Operating system data necessary to load to Windows is stored in a separate partition.
If the computer does not contain a TPM, the computer will not load to Windows. A user must enter password when the computer boots.
BitLocker To Go allows you to encrypt removable drives, including USB drives and SD cards, which could use NTFS, FAT16, FAT32, or exFAT file systems.
When you insert un unencrypted removable drive into a Windows computer, you can select the “Turn on BitLocker” option and follow the steps to activate BitLocker
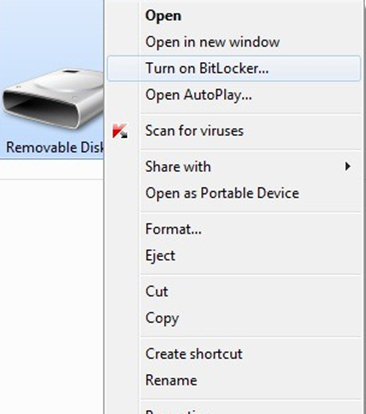
When you insert an encrypted removable drive into a Windows computer, Windows will automatically require you to enter the password to unlock it.
EFS
EFS is the Encrypting File System. Why do we need to encrypt the file system? Remember that Windows provides / denies access to files based on user permissions and an access control list (the NTFS file permissions we talked about). But if we take the hard disk out of the computer and plug it into an external reader, we can bypass Windows and read the files directly regardless of the permissions. This would be bad if the computer was stolen because the thief could remove the hard drive and see all the files.
To keep this from happening, we can encrypt the hard disk drive with BitLocker. The problem with BitLocker is that it encrypts the entire hard disk drive with the same key. The BitLocker key is encrypted with each user’s password. If we have multiple users on a computer, then when any user logs in, BitLocker uses their password to unlock the key and decrypt the entire hard disk drive.
So technically, any user could remove the hard disk drive from their computer, plug it into an external reader, and use their BitLocker key to decrypt the entire drive. By doing so, they can access any file, even when NTFS does not provide them with permission.
How can we prevent this? We can use the EFS. In an Encrypting File System
- A user manually selects the files and folders that he wants to encrypt. The system marks each folder for encryption in the metadata (encryption is inherited to subfolders)
- Each file is encrypted with a different key
- A private key is created and used to generate a public key
- All the file keys are encrypted with the public key
- The private key can only decrypt files and the public key can only encrypt files
- The private key is stored on the drive, but is encrypted with the user’s password
- Encryption and decryption are handled transparently by the file system. That is, when Windows requests a file from the file system, the file system automatically decrypts and delivers it. When Windows creates a new file, the file system automatically encrypts it.
- A file can be encrypted with EFS and then again with BitLocker
Security Problems with EFS
- When you send a file over the network or move it to a portable drive, the file will remain decrypted
- In Windows 2000, the local admin account can decrypt all files by default. In future versions of Windows, this is not possible
- Windows XP and further versions of Windows store the private key on a password reset disk and in Active Directory (if the computer is connected to a domain)
- If the user forgets/resets his password, then the private key is lost forever (it is encrypted with the user’s password)
- If the user’s password is compromised, then all the files are compromised
