2.4 Give a scenario, install and configure the appropriate wireless standards and technologies
- 802.11 Standards
- a
- b
- g
- n (Wi-Fi 4)
- ac Wi-Fi 5)
- ax (Wi-Fi 6)
- Frequencies and Range
- 2.4GHz
- 5 GHz
- Channels
- Regulatory Impacts
- Channel Bonding
- Service Set Identifier (SSID)
- Basic Service Set
- Extended Service Set
- Independent Basic Service Set (Ad Hoc)
- Roaming
- Antenna Types
- Omni
- Directional
- Encryption Standards
- Wi-Fi Protected Access (WPA) / WPA2 Personal / Advanced Encryption Standard (AES) / Temporal Key Integrity Protocol (TKIP)
- WPA/WPA2 Enterprise (AES/TKIP)
- Cellular Technologies
- Code-Division Multiple Access (CDMA)
- Global System for Mobile Communications (GSM)
- Long-Term Evolution (LTE)
- 3G, 4G, 5G
- Multiple Input, Multiple Output (MIMO) and Multi-User MIMO (MU-MIMO)
All Wi-Fi protocols are regulated by IEEE (Institute of Electrical and Electronics Engineers). Collectively, we call them 802.11. As the demand for technology increases, new standards are released. The current standard is 802.11ac.
An access point or client (computer, phone, Wi-Fi adapter) may support multiple standards. The standards are backwards compatible (for example, an 802.11ac device will work with an 802.11a device).
Six standards have emerged
| 802.11a | 1999 Standard Supports up to 54 Mbps in the 5GHz range |
| 802.11b | 1999 Standard Supports up to 11 Mbps in the 2.4GHz range |
| 802.11g | 2003 Standard Up to 54 Mbps in the 2.4GHz range If all the devices on a network are at the 802.11g level, then the network operates at 54 Mbps. Otherwise, it operates at 11 Mbps to support the older devices. |
| 802.11n (Wi-Fi 4) | 2009 Standard Supports multiple-input, multiple-output (MIMO) – an access point device with multiple antennas Up to 72.2 Mbps with one send and one receive antenna Up to 450 Mbps with three send and three receive antennas Also supports transmit beamforming which focuses the signal so that there are no dead zones It has a better way of supporting older devices. It can operate in one of three modes Legacy means it sends separate packets for older devices, which is not efficient Mixed means it sends out standard packets that support older devices and newer devices. We might also call this high-throughput or 802.11a-ht or 802.11g-ht. Greenfield means that it sends out 802.11n packets that support newer devices, but not older devices |
| 802.11ac (Wi-Fi 5) | 2014 Standard Supports multiuser multiple-input, multiple-output (MIMO) Up to 433 Mbps per antenna, or 1.3Gbps with three antennas |
| 802.11ax (Wi-Fi 6) | 2021 standard In addition to all the features of Wi-Fi 5, Wi-Fi 6 offers a 400% improvement in throughput and a 75% drop in latency. It has the best performance in high-density areas such as offices. It takes advantage of cellular technology called orthogonal frequency-division multiple access, which optimizes the radio signal. While the previous Wi-Fi standards operated in the 2.4Ghz and 5Ghz bands, Wi-Fi 6 also operates at 6Ghz (technically 5.925Ghz to 7.125Ghz). |
The standard provides guidelines that manufacturers of wireless devices use when making devices. With a reliable standard, products from different manufacturers all work together. Just think about it – it doesn’t really matter what brand laptop or phone you have, it generally works with the Wi-Fi at your office, your home, the airport, the mall, your friend’s house, etc. That’s because the Wi-Fi card in your device follows the same standard as the Wireless Access Points installed everywhere.
Which Wi-Fi device should you select? Obviously, the latest version is the best! Technology will continue to improve, and you don’t want to be stuck with something that is obsolete by the time you install it.
A radio signal (like the one used in Wi-Fi and cell towers) is like a wave. It goes up and down.
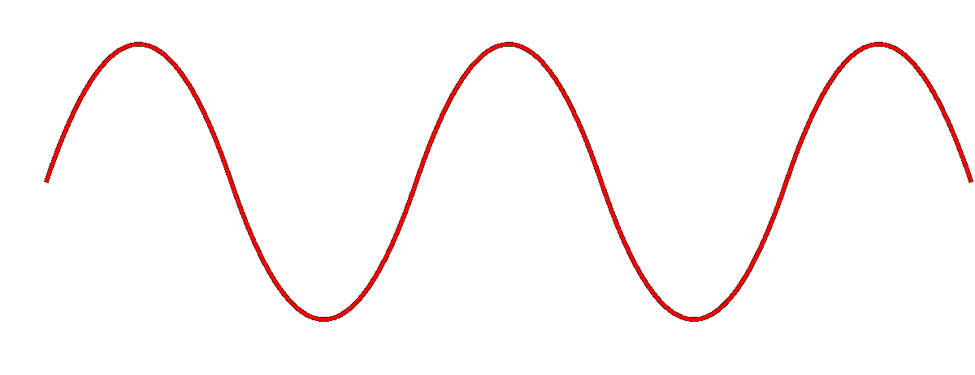
The height of the wave is called the Amplitude. The width of the wave is called the wave length. No matter the height or the width, the wave travels at the speed of light. You can think of a Wi-Fi signal like light that you can’t see, because scientifically, that’s exactly what it is. Thus, the wider the wave (the larger the wavelength), the less waves will pass through each second. We call this the frequency, measured as the number of waves that pass through per second. We measure frequency in Hertz (Hz).
If you had special glasses that would let you see waves in the air, it would look like a big mess of waves travelling everywhere. So, each device is programmed to “look” for waves at a specific frequency and ignore the rest.
The government regulates the frequency that each type of technology can use. If everybody could broadcast signals at any frequency they wanted, the air would be a mess and wireless systems would not be able to function.
Wi-Fi signals travel at a frequency of 2.4GHz and 5GHz (and 6Ghz soon). Older cordless phones use a signal with a frequency of 900MHz.
If we change the Amplitude of the wave over time (up and down), we can use it to convey information.
The range of a Wi-Fi signal is between 50 and 300 feet. It is affected by signal interference (noise) from neighboring networks. Different wall types can block or reduce the signal (glass, concrete, steel will block signals more than drywall).
The 2.4GHz range has eleven channels. It has a longer range and is less vulnerable to noise than the 5GHz range, which has twenty-three channels. Older devices use the 2.4GHz range. What’s a channel?
When two waves with the same frequency collide, they cancel each other out and the signal is lost. If I have a Wi-Fi network and my neighbor has a Wi-Fi network, the signals will interfere, and nobody will be able to understand anything. To solve this problem, we divide the 2.4GHz spectrum into 11 channels: Each channel is 22MHz wide, spaced 5MHz apart.
Therefore, a 2.4GHz network is not actually broadcasting at a frequency of exactly 2.4000000GHz, but instead at 2.412GHz, 2.417GHz, or 2.422GHz, etc.
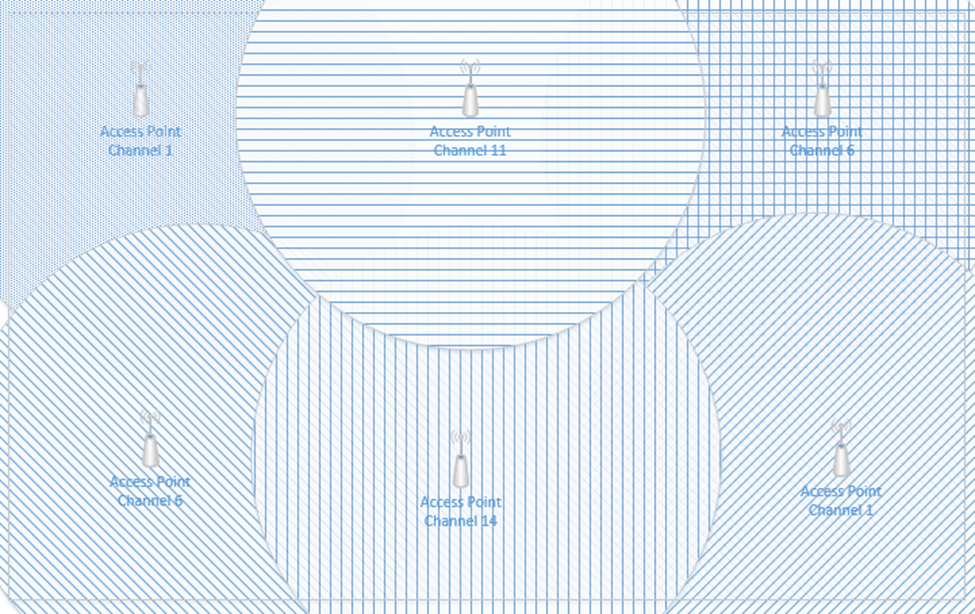
If two neighboring networks choose different channels, they will each broadcast on a slightly different frequency – different enough that their signals won’t interfere. We can manually select the channel that we want to broadcast on, or we can let our wireless system choose it for us. We should survey the neighboring networks to see what channels they are broadcasting on and select a different channel from all of them. If we have multiple access points in a building and their signals overlap, we should select a different channel for each of them.
The channel concept applies to 5GHz networks as well. A 5GHz spectrum is divided into 23 channels, each is 20MHz wide. A 5GHz spectrum can broadcast on 5.150GHz, 5.1570GHz, etc. There are more regulations for the 5GHz network and some countries do not allow some frequencies (they could interfere with weather radar and other systems).
If our network does not have enough bandwidth, we can bond two adjacent channels together to double its capacity. This is known as channel bonding. We combine two 20MHz channels into one 40MHz channel. One of the channels is the primary channel, and the other is secondary. Client devices that use channel bonding will transmit and receive on both channels, while client devices that don’t support it will only use the primary channel.
5GHz has one complication. Some of the frequencies in the 5GHz range are also used by government weather radar systems. If your device is using a frequency in the range of a government radar system, it must first scan to see if such a device is present. If it is, your device must switch to a different channel for at least an hour and then scan again. That is, the government devices get first dibs on some of the 5GHz channels and don’t allow interference from consumer devices. Devices have a feature called dynamic frequency selection (DFS), which allows them to detect the nearby signal and switch over.
High end devices such as smartphones and wireless access points will use dynamic frequency selection. Cheaper devices will not. If a wireless access point switches to a DFS channel, cheaper devices will not be able to detect the signal and will switch to the 2.4Ghz range instead.
Every country regulates the use of wireless signals and some channels that are available for use in the United States are not available in other countries. When you set up a wireless device, you must check the regulations in your country and verify that you are broadcasting in a range that is permitted. Regulations are subject to change and a channel that was legal before may become illegal later.
There are two general types of networks
The SSID is or Service Set Identifier is the name of the network. An SSID is mapped to a WLAN (Wireless Local Area Network), and a WLAN is typically mapped to a VLAN (Virtual Local Area Network). Multiple SSIDs/WLANs can be mapped to the same VLAN. The purpose of an SSID is to allow us to separate wireless traffic the same way that we can separate wired traffic.
A single wireless access point can broadcast multiple SSIDs. For example, we might have a “Guest” SSID for guests, a “Staff” SSID for staff, and an “IoT” SSID for smart devices. If we have a large office with multiple wireless access points, each wireless access point can be configured to broadcast all the SSIDs.
If I have a large office, one wireless access point won’t be able to provide a good signal across the entire floor. I might place my access points like this, and give each of them a different channel (or the controller might assign each one a different channel automatically). Each access point has its own MAC address, but all are broadcasting the same SSIDs.
What happens when I connect to the “Staff” SSID and I’m standing at the top left corner of the office? My laptop will probably connect to the closest access point (because it has the strongest signal). It might see “Staff” SSIDs from other access points nearby with weaker signals and different channels. As I move throughout the office, the signal from the first access point I connected to will become weaker, but my laptop will automatically move its connection to another wireless access point that is broadcasting the “Staff” SSID. This process is called roaming. When multiple access points create a seamless SSID, it is known as a ESSID or Extended Service Set Identifier.
The BSSID or Basic Service Set Identifier is the name (or MAC address) of the physical access point that I am connected to. Thus, within a given SSID, there can be one or multiple BSSIDs. If an access point is broadcasting multiple SSIDs, then that access point will also have multiple BSSIDs. That is, an access point will have multiple MAC addresses assigned to it by the manufacturer – one physical MAC address that it uses to communicate with the wired network, and multiple wireless MAC addresses that it can assign to each SSID. The number of SSIDs that a wireless access point can broadcast is limited to the number of wireless MAC addresses that are assigned to it.
The portion of the access point that broadcasts the signal is called the radio. An access point can have multiple radios. Having multiple radios allows the access point to communicate with multiple devices at the same time. An access point will need a unique MAC address for each radio-SSID combination. Thus, if an access point can broadcast 32 SSIDs and has two radios, it will have 64 wireless MAC addresses.
Below is a common Wireless Access Point, the Cisco Aironet 1142N. This access point has antennas concealed inside it. It’s considered omnidirectional, because it broadcasts in all directions. Most access points are omnidirectional. We can mount it to a ceiling and it will provide good coverage in an office.
What if I have a problem where I need to point a Wi-Fi signal in a specific direction? I could attach external antennas to the access point and mount them facing the direction that I require. This is known as unidirectional transmission. Antennas are available in different shapes and sizes. Antennas also increase the signal strength of the access point.

An example of an access point with antennas is below

Another example of powerful directional antennas is the Ubiquiti AirFiber. It allows us to send a strong Wi-Fi signal long distances by pointing it in a specific direction. For example, I could use the AirFiber to connect two far away buildings via a wireless connection.

There are many other types of antennas, each of which has a different pattern and purpose.
How do we secure the communication between the wireless access point and the wireless device? How do we ensure that unauthorized users can’t connect? There are several forms of wireless encryption.
- (Wired Equivalent Privacy) encryption uses a password to authenticate the host with the access point.
- An administrator configures a password on the wireless access point
- The authorized users are provided with the password, which they use to authenticate with the access point
- All further communications are encrypted with the provided password
- A packet sniffer can intercept packets and easily crack the password.
- WEP has been known to be insecure since 2005 but is still in use today.
- WPA keys were 64-bits long.
- WEP is not recommended
- An administrator configures a password on the wireless access point
- (Wi-Fi Protected Access) and WPA2 use a password to create a handshake (which creates a unique one-time password) between the host and the access point.
- An administrator must create a WPA or WPA2 password and configure it on each access point
- The authorized users are provided with the password, which they use to authenticate with the access point
- When a device first connects to a wireless access point, the device and the WAP follow a handshake process to create a unique one-time key that the two parties use to encrypt all further communications
- WPA is more secure than WEP because the key is much longer and because every connection is encrypted with a different password
- A packet sniffer can intercept packets during the handshake process and identify the password.
- WPA uses 256-bit keys
- WPA2 uses AES encryption algorithms and has replaced WPA
- An administrator must create a WPA or WPA2 password and configure it on each access point
- WPA Enterprise uses a RADIUS server to authenticate the identity of the host attempting to connect. The host will typically present a digitally signed certificate to the RADIUS server (i.e. the host computer must have a certificate installed to connect to the network). Another option is for the host to sign in to the wireless network by entering a username and password. Certificate-based WPA Enterprise is difficult to break, provided that the certificates are digitally signed using a strong algorithm and that there are no other flaws in the access point or RADIUS server. Username/password based WPA Enterprise can be broken if the username/password are intercepted. An attacker could set up a rogue access point broadcasting the same SSID and then intercept usernames/passwords.
- WPA3 is under development but is expected to replace WPA2.
- TKIP (Temporal Key Integrity Protocol) was a standard that was introduced to temporarily replace WEP.
- WEP had been broken and the Wi-Fi alliance needed a quick solution to replace it without forcing customers to replace physical hardware
- TKIP is no longer considered secure
- TKIP uses the same functions as WEP, except that it
- Adds an initialization vector to the secret key
- Uses a sequence counter to prevent replay attacks
- Uses a 64-bit Message Integrity Check
- Encrypts every data packet with a unique encryption key
- Adds an initialization vector to the secret key
- WEP had been broken and the Wi-Fi alliance needed a quick solution to replace it without forcing customers to replace physical hardware
Remember that Wi-Fi is considered a “one-to-many” connection. One antenna talks to many devices. But as I said before, a wireless access point can only communicate with one device at a time.
Access points use Time Division Multiplexing. The access point sends data to one device, pauses, sends data to the next device, pauses, sends data to the third device, pauses, etc. until it has sent data to all the devices. It is also receiving data from each device in the same pattern.
To send data to multiple devices at the same time, an access point must have multiple antennas and engage in advanced signal processing. This technology is known as Multiple Input, Multiple Output (MIMO).
How does it work?
- Remember that if we send multiple radio signals at the same time, they can either merge and become more powerful, or they can cancel each other out. Whether they merge or cancel each other out depends on the way that they are sent.
- Beamforming is an idea that we can send out signals from multiple antennas in a way that they can all combine at the receiver as a more powerful signal. The receiver uses an algorithm to amplify amplifies the different signals by giving each one a different weight.
- There are three ways
- Precoding – the access point sends out the same signal through multiple antennas. Each signal is given a different phase and weight so that the signals combine at the receiver to have the maximum power.
- Spatial Multiplexing – the access point splits a high-bandwidth signal into multiple low-bandwidth signals. Each signal is transmitted from a different antenna. Spatial multiplexing is good when there is a high level of noise. The receiver splits the signals into channels and interprets the data.
- Diversity Coding – the access point sends the same signal through multiple antennas, but each signal is sent orthogonal to the other ones (at right angles). That means, regardless of how the receiver is facing, it will receive at least one signal correctly.
- Precoding – the access point sends out the same signal through multiple antennas. Each signal is given a different phase and weight so that the signals combine at the receiver to have the maximum power.
We can take this a step further and use a Multi-User MIMO (MU-MIMO). What happens when we want to use MIMO with multiple users at the same time? The access point can divide the signals spatially so that it can serve multiple users at the same time, provided they are some distance apart. When multiple users close together, the signals cannot be separated easily, and those users must share the bandwidth.
Wi-Fi 6 allows MU-MIMO to function in both directions. Previous versions allowed multiple users to be served quickly when downloading, but Wi-Fi 6 allows multiple users to upload data at the same time.
When selecting wireless devices, consider the following
- Purchase wireless access points that support Wi-Fi 6 and MU-MIMO
- As the use of Wi-Fi increases, consider purchasing wireless access points that support a 2.5 Gbit/s or 5 Gbit/s ethernet connection.
- Determine the range of each access point and the area that you must cover; this will allow you to calculate the number of access points required
- Determine the number of devices or users that need to be served and the maximum capacity of the wireless access point
- Consider whether the area that requires coverage has a basic layout or whether specific directional antennas are required
A cellular antenna in a tower can only talk to one phone at a time. How do we connect multiple phones to a tower at the same time? What if everybody is at the Super Bowl and texting and talking and tweeting?
There are three types of cellular network connections – GSM (Global System for Mobile Communications), TDMA (Time Division Multiple Access), and CDMA (Code Division Multiple Access).
A cellular phone connects to a tower through its cellular modem. The phone will contain a SIM card that allows it to authenticate with that network. Some laptops and routers also support cellular connections.
A cellular phone may be locked to a specific cellular network (Bell, Telus, AT&T, Verizon, etc.) or unlocked (in which case it can connect to any network). You pay for a cellular plan with a specific carrier (Bell, Telus, AT&T, Verizon, etc.), which could include any number of features.
Some cellular phones have room for two SIM cards. A cell phone with two SIM cards can connect to two networks at the same time (or maintain two separate connections to the same network).
When a phone is outside the range of its default network (for example, when it is in another country), it is roaming, and will attempt to connect to any number of available networks. The user may incur additional charges for roaming.
GSM and CDMA are the two main types of cellular radio networks. Most cellular networks are GSM, except for those maintained by Sprint and Verizon. Some phones can operate on both GSM and CDMA networks. A carrier will operate their radios on several different frequencies (for example, Sprint operates over the CDMA 800 MHz and 1900 MHz frequencies). For a phone to connect to a carrier’s network, it must have a modem that operates on at least one of that carrier’s frequencies.
TDMA was an older cellular technology that has been incorporated into GSM. With TDMA, a cellular antenna would give each cell phone a time slot. The width of each slot is measured in milliseconds. Each phone would only listen during its slot. This way the tower can connect multiple phones at the same time. It’s like a person trying to have a conversation with several other people: say a few words to person one, say a few words to person two, say a few words to person three, come back to person one and say a few words, etc.. Each of the other people only needs to listen when they are being talked to.
GSM continues to use the same time slots that TDMA did. GSM data uses the GPRS (General Packet Radio Service) protocol, which is no longer considered secure.
CDMA is more complicated. It involves complicated math, linear algebra to be specific. You can think of the signal from a cell tower to a phone like a wave. Each phone agrees on a code with the tower. The tower creates a signal that is a mash of all the messages that it wants to send each phone; the messages are coded so that they don’t cancel each other out. Every phone receives the same signal but extracts its own portion from it. It’s like if I hid French words between all the English words in this book. An English-speaking person would read the English words and a French-speaking person would read the French words. Now imagine that I hid words from eighty different languages in this book. Every person could see all the words but only understand their own language.
There are several cellular network technologies/speeds
- 3G – 3G is also known as Third Generation. It provides data transfer rates of at least 144 kbit/s.
- 4G – 4G is also known as Fourth Generation. 4G must use an underlying IP network, and provide data speeds of up to 100 Mbit/s for moving users and 1 Gbit/s for stationary users.
- 5G – 5G is also known as Fifth Generation. It provides data rates of up to 1 Gbit/s. 5G is supposed to provide enough bandwidth to allow devices to function as primary internet connections. 5G broadcasts signals at 24 Ghz to 40 Ghz.
- LTE – LTE is also known as Long Term Evolution. It is an advancement of the 3G network, but does not meet the standard of 4G. LTE provides download speeds of up to 299 Mbit/s. It also requires IP packet switching for both data and voice calls.
Some phones support both GSM/CDMA and either 3G/4G/5G/LTE. GSM/CDMA are becoming less popular as 5G takes over.
When selecting a phone
- Ensure that the phone’s modem is compatible with the chosen carrier
- Ensure that the carrier has adequate network coverage in the areas you plan to visit
- Ensure that the cost of the cellular data and voice plan is known in advance
Cellular (data-only) connections are used by mobile workers and by cellular modems. It is common for an organization to install a primary broadband modem and a back up cellular modem. If the primary connection fails, the cellular back up will take over.
