4.1 Explain common security concepts
- Confidentiality, Integrity, Availability (CIA)
- Threats
- Internal
- External
- Vulnerabilities
- Common Vulnerabilities and Exposures (CVE)
- Zero-Day
- Exploits
- Least Privilege
- Role-Based Access
- Zero Trust
- Defense in Depth
- Network Segmentation Enforcement
- Screened Subnet (DMZ)
- Separation of Duties
- Network Access Control
- Honeypot
- Authentication Methods
- Multifactor
- Terminal Access Control-Access Control System Plus (TACACS+)
- Single Sign-On (SSO)
- Remote Authentication Dial-In User Service (RADIUS)
- LDAP
- Kerberos
- Local Authentication
- 802.1X
- Extensible Authentication Protocol (EAP)
- Risk Management
- Security Risk Assessments
- Threat Assessment
- Vulnerability Assessment
- Penetration Testing
- Posture Assessment
- Business Risk Assessment
- Process Assessment
- Vendor Assessment
- Security Risk Assessments
- Security Information and Event Management (SIEM)
Now that we have explored network redundancy, let’s take a look at security. The principles of data security follow three concepts: Confidentiality, Integrity, and Availability (CIA)
Confidentiality means that sensitive data is only seen by authorized users.
We link data (objects) and users (subjects) so that only authorized subjects have access to objects.
We evaluate confidentiality according to the following ideas
- Sensitivity – what is the value of the information? How much damage could it cause if it were leaked?
- Discretion – does a user have the ability to leak the confidential data? How much ability? Is it easy or difficult to leak the data?
- Criticality – how important is the information to the business?
- Concealment – can we hide the data so that unauthorized users can’t see it?
- Privacy – if the data is leaked, what harm can it cause to a specific individual?
- Seclusion – can we store the data in a remote location?
- Isolation – can we store the data away from other types of data?
Data could be leaked intentionally or unintentionally, but a leak is still a leak.
Integrity ensures that the data is not modified by unauthorized users while in transit or at rest. That means that the data that is received is the same as the data that was sent. We should be able to verify that an object has not been changed.
We evaluate integrity according to the following ideas
- Accuracy – the information is correct.
- Authenticity – the information has not changed since it was created
- Nonrepudiation – the person who created the information cannot deny that he created it. That is, we are certain of the identity of the author.
- Completeness – the information is not missing any component.
- Truthfulness – the information is realistic
- Validity – the information is logically sound
- Accountability – a person is responsible for the accuracy of the information
- Comprehensiveness – the information is complete
If an unauthorized user can access an object, he can probably change it too. Integrity can be affected by human users and by malicious programs such as viruses.
Availability ensures that the resource is available when it is needed.
We evaluate availability according to the following ideas
- Usability – the information is easy to understand
- Accessibility – many people can view the information regardless of the type of equipment they have or their background
- Timeliness – the users can access the data quickly
Availability can be affected by a lack of resources (too many users and not enough computing hardware/bandwidth) or by attacks such as Denial of Service.
The Threats to the data can be Internal or External. An internal threat is an employee, a vendor or somebody that we trust. An External threat could be a hacker, a foreign government, an activist, or a competitor.
A vulnerability is a weakness in a system, such as a misconfigured firewall or an operating system that is not patched. A threat will take advantage of a vulnerability to gain access into our system. When this happens, it is known as an exploit.
The end goal of security is to reduce or eliminate the exploits. We can’t stop external threats, but we can reduce internal threats and we can reduce the number of vulnerabilities. Because it is not always possible to eliminate every vulnerability, we must create multiple layers of security. The more important the asset, the more layers of security we should have.
Think about a bank. A burglar is a threat. If the bank leaves the vault unlocked at night, that is a vulnerability. But the bank has multiple layers of security – a locked door, a surveillance camera, a motion sensor, a security guard, a locked vault. Even if one of those items fails, it is still difficult for the robber to get the money from the vault.
Our network might have a firewall with access control lists, a VPN with two factor authentication, and a server with complicated passwords and limited privileges. Even if the server was unpatched (a vulnerability), a hacker wouldn’t be able to access it because the firewall would block him, and he wouldn’t be able to connect to our network through the VPN. These layers might be known as defence in depth.
A group sponsored by MITRE and the US Department of Homeland Security created a database of vulnerabilities called Common Vulnerabilities and Exposures, or CVE.
Each time a vulnerability is discovered in a commercial device, it is listed in this database. You can search the database for devices in use at your organization and determine whether one or more of them contains a vulnerability. You can then patch the device or take it out of service if it cannot be patched, or remove it from the network (or put it behind a firewall) if it cannot be patched and is critical to your operations.
A Zero Day exploit is a vulnerability in a software program or system that has just been discovered; therefore, there is no patch. Day Zero is the day that the exploit is first discovered by the public. An attacker might know about the vulnerability before the public and can take advantage of it for days, weeks, months, or even years.
When a company discovers a serious vulnerability in their system, they may choose to develop a patch and ensure that their largest customers have installed it before disclosing the vulnerability to the public. This will reduce the risk that hackers become aware of the vulnerability before it can be patched.
Some of the things we can do to protect our network
- Enforce the Principle of Least Privilege – A user account should be granted only the least privileges/access required for the user to perform his/her job (or function in the case of a generic account).
- User accounts should be audited to ensure that users are not granted permission to objects that they do not require
- An account can be restricted so that it can only access the system (or specific system resources) during specific times of day or specific days.
- Workers who operate on a fixed schedule should only be permitted to access the system when required to perform their job
- In a large organization, assigning privileges to each account manually can be time consuming and lead to security vulnerabilities (when too many privileges are assigned) or disruption to the business (when not enough privileges are assigned)
- User accounts should be audited to ensure that users are not granted permission to objects that they do not require
Instead, groups can be created. A group is a role that a user plays in the organization. Each group can be assigned specific privileges consistent with that role. A user can be assigned to one or more groups. The user then inherits the privileges that were assigned to each group.
For example, an organization may create an “engineers” group. The engineers’ group is given the privilege of accessing AutoCAD files. When a new engineer is hired, he is added to the engineers’ group. He now has access to AutoCAD files automatically.
- A location-based policy is one that provides a user with privileges based on his physical location at the time of log in, or based on his office location
When accessing the network through a mobile device, the user’s GPS location may be used to determine the appropriate policy
- Enforce Role Based Access Control – Permissions are not assigned to individual users or to objects. Instead, permissions are assigned to operations/actions (known as roles)
- A user can be assigned to a specific group (the user is given a role); the user inherits the permissions assigned to the role
- The organization can define the operations and actions that are relevant to their organization. For example:
- Sales person (can access sales data)
- Accountant (can enter data into the accounting system)
- Accounts payable clerk (can approve invoices and issue payments)
- Sales person (can access sales data)
- A user can be assigned to a specific group (the user is given a role); the user inherits the permissions assigned to the role
- Enforce Zero Trust – Zero Trust is a new concept that tells the network not to trust anything regardless of whether it is inside the network or outside. Any device connected to the network must prove that it is worthy of accessing a resource. In a way, it is an idea of installing a firewall between the internal users and the network, not just between the internet and the network.
The Zero Trust system works at Layer 7. It must deeply examine the data that is being transferred, not just the source and recipient.
A common implementation- We don’t trust anything connected to our network, not even computers. Even though they are probably corporate owned, we can’t immediately verify that they haven’t been exploited or placed there by a hacker.
- When a user logs in to a computer connected to our network, we verify that the computer is legitimate and that it has the proper security patches. We might do so through an endpoint management application or security certificate.
- We also verify that the user is legitimate and has authorization to log in to that specific computer at that specific time. We might do so through a smart card or other credential.
- We also verify that the computer is connected to the network at the correct location.
- We now give the user access to the specific resources that he is entitled to.
- We continue to monitor the user and the computer.
- We don’t trust anything connected to our network, not even computers. Even though they are probably corporate owned, we can’t immediately verify that they haven’t been exploited or placed there by a hacker.
- Network Segmentation Enforcement – earlier we talked about setting up VLANs to segment the network. We could have a VLAN for security cameras, a VLAN for user computers, a VLAN for servers, etc. When a user wants to access a resource inside another VLAN, the firewall must decide whether such an action is permitted. An administrator can configure firewall rules to give users access to the resources that they require.
The problem with this approach is that we must create many firewall rules (tens of thousands for a large network), and that a user can access all of the devices on his own VLAN, even though such actions may not be necessary. It is not possible for an administrator to manage all those rules.
Think about a scenario where a user downloads a virus (either accidentally or on purpose) and it spreads to all the other computers in the office due to an unpatched vulnerability. The VLAN could not prevent it.
A new idea is called micro-segmentation. With virtualization and software defined networking, we can monitor and inspect the contents of every packet travelling East-West (on the same VLAN). We can also create a firewall on each device (user computer, virtual server, physical server, etc) to determine whether a packet is permitted, and configure policies to adapt to changes in activities or user behavior. - Screened Subnet (DMZ) – The DMZ is the Demilitarized Zone. The DMZ is a zone where devices that need to access the internal and external network can be placed.
Hosts that require internet access and that are vulnerable to attack (such as e-mail servers, web servers, and VoIP servers) should be placed in the DMZ.
The best setup is to install a firewall between the internet and the DMZ, and another firewall between the DMZ and the internal network.
Always assume that a device in the DMZ has been compromised. Building on the concept of our redundant network from earlier, now we have installed a DMZ, and one server within the DMZ. The firewalls on the right protect our DMZ servers from external threats, and the firewalls on the left protect our internal network from external threats and potential threats from the DMZ.
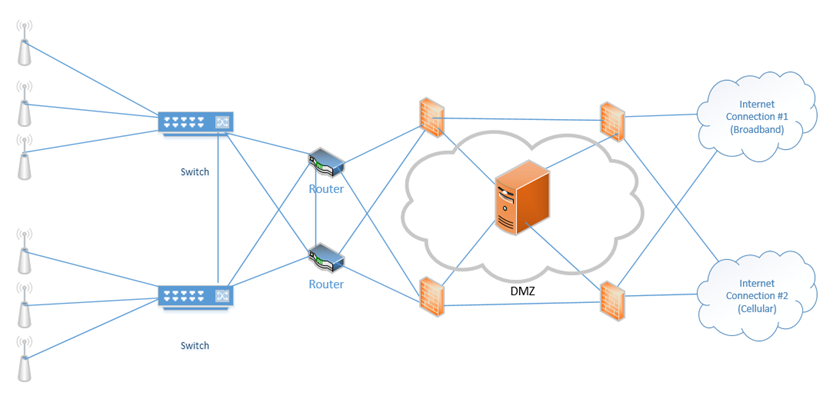
- Devices in the DMZ may have a public and a private IP. Their private subnet is known as the screened subnet.
- Separation of Duties – No single employee can or should do everything. For example, an employee who approves invoices should not also be the one to create/sign the checks. If the employee who approves invoices submits a fraudulent invoice and attempts to pay themselves, they would be caught.
In the IT world, we want to reduce the risk that a malicious administrator can introduce a vulnerability to our system. Some ways that we can separate duties
- No employee should have “super admin” access to every system; the system can be segmented, and each employee can be given a role. Multiple employees should share each role. This prevents a rogue employee from locking out other administrators.
- The work of any employee should be verified by another employee
- Have one employee install patches and another employee verify that the patches are operational
- Have one employee write configurations and have another employee verify that the configurations are correct
- Have one employee update configurations on a device and have another employee verify that the configurations have been correctly updated
- Have multiple employees jointly investigate security incidents, and have other employees review their findings
- Have one employee install patches and another employee verify that the patches are operational
- Require multiple administrators to approve the creation of an administrator account or changes to an administrator’s privileges
- The work of any employee should be verified by another employee
- Network Access Control – Network Access Control or NAC is an idea that we should verify the security status of a device before permitting it to access the network. It is related to Zero Trust. Some of the properties that our network will seek to verify
- Security patches
- Antivirus protection
- User authentication
- Security patches
We usually need to be able to give a non-compliant device limited access to the network so that it can obtain the required software updates and become compliant. Otherwise, devices that are offline for some time will become bricks.
- Honeypot – A Honeypot is a network device that appears to be vulnerable but is in fact designed to detect hackers. A network security administrator creates a honeypot to identify hackers and/or to distract them from legitimate network resources. A honeypot allows an organization to understand the motives behind the attacks (which can be used to better protect network and other resources), and the type and sophistication of the hackers.
There are several types of honeypots
- Pure honeypot – a production system with a monitoring device on the network interface. The pure honeypot can be detected by a hacker.
- High interaction honeypot – runs on a physical or virtual machine and imitates many production systems. The high interaction honeypot consumes a substantial amount of resources. When run on a virtual machine, the honeypot can be quickly killed and regenerated.
- Low interaction honeypot – simulates only necessary services, allowing more honeypots to operate with fewer resources.
- SPAM honeypot – spammers will locate servers that use open relays (an open relay is an e-mail server that allows an unauthenticated user to send an e-mail) and use them to send e-mails. The spammer will attempt to send e-mail test messages through the SPAM honeypot; if successful, the spammer will continue to send e-mail through the honeypot. The honeypot can detect the SPAM messages and also detect the spammer.
- High interaction honeypot – runs on a physical or virtual machine and imitates many production systems. The high interaction honeypot consumes a substantial amount of resources. When run on a virtual machine, the honeypot can be quickly killed and regenerated.
Authentication Methods are ways for us to verify the identity of a user. Some of the methods include
- Multifactor – In the past, you would authenticate with a server by providing a username and password. The problem with that method is that people can steal your username/password combination and log in as you.
The principles of multifactor authentication (formally two-factor authentication) are important. The three main factors are Something You Are, Something You Have, and Something You Know. Basic authentication methods combine Something You Have (a username/access card) with either Something You Know (a password) or Something You Are (biometric).
- Something You Are – something you are refers to a biometric identity such as facial recognition, fingerprints, voice recognition, or a retinal scan. Select the best type of biometric for your environment. A construction site or hospital may have employees with gloves, who cannot scan into a fingerprint reader, so a retinal scan will be more appropriate.
- Something You Have – something you have refers to a smartcard, identification card, or username; it could also refer to a randomly generated password (such as an RSA SecurID or authenticator app)
- Something You Know – something you know refers to a password or PIN
- Somewhere You Are – somewhere you are refers to your physical location. In the case of connecting to the internet, somewhere you are is your IP address or GPS location. If a hacker compromises a username/password and logs in through a computer or network location that is not recognized, then the login may be denied. Websites have sophisticated ways of detecting users – IP address, web browser version, computer version, date/time of the login, other user behaviors. If the username/login is correct, but the other factors aren’t it could be that the account was compromised, or it could be that the user is travelling/bought a new computer. The site can ask the user for additional verification (such as through an automated phone call) if it determines that the account may be compromised.
- Something You Do – something you do is an observation of the user’s action’s or behaviors. In Windows a user can choose a picture password; in an Android phone the user can interact with a pattern.
- Something You Have – something you have refers to a smartcard, identification card, or username; it could also refer to a randomly generated password (such as an RSA SecurID or authenticator app)
Consider that we have a large network with multiple devices (servers, switches, routers, etc.). We need a centralized method for managing user authentication. Why?
- We want an administrator to be able to log in to multiple devices without having to keep track of a different username/password combination for each one.
- We also want to log each time the administrator logs in.
- We want to be able to disable an administrator’s account without having to manually log in to each device.
How can we accomplish the above? There are a few methods
- Terminal Access Control-Access Control System Plus (TACACS+) – TACACS or Terminal Access Controller Access-Control System is a protocol for accessing/managing network devices. It was developed by UNIX.
TACACS+ was developed by Cisco and is a separate protocol from TACACS. Most systems use TACACS+ or RADIUS.
TACAS uses port 49 to communicate.
TACACS+ encrypts the full content of each packet while RADIUS encrypts only the user passwords. TACACS+ uses TCP, while RADIUS uses UDP (therefore RADIUS has more errors). Cisco continues to support RADIUS, but TACACS+ is recommended.
TACACS+ uses the AAA (Authentication, Authorization, Accounting) architecture, where each element is separate. Therefore, a system could use a different form of authentication (such as Kerberos) with TACACS+ authorization and accounting. Some forms of user authentication include- Point-to-Point
- PAP
- CHAP
- EAP
- Kerberos
- Point-to-Point
Authentication – the server is trying to determine who you are
- The client sends a START message to the server
- The server sends a REPLY message
- The client sends a CONTINUE message, if additional information is required for authentication
- Otherwise, authentication is complete
- The server sends a REPLY message
Authorization – the server is trying to determine if you are permitted to access the resource
- A default state of “unknown user” is created if the user’s identity is unknown
- Otherwise, the TACAS+ server responds with a RESPONSE message, which contains the restrictions on the user
Accounting – the server is making a record of your access
- A START message records when the user started the connection
- A STOP message records when the user stopped the connection
- An UPDATE message says that a task is still being performed
- A STOP message records when the user stopped the connection
TACACS+ allows an administrator to configure different privilege levels for each user (for example a user may not be permitted to modify an ACL on a router). RADIUS does not allow different privilege levels (all users are effectively superadmins).
- Single Sign-On (SSO) – Single Sign-On uses a central system to authenticate users across multiple applications.
For example, a user logs in to his computer via his Windows Active Directory password. He is then able to access the corporate intranet, procurement application, online library, payroll, and e-mail without having to re-enter a username or password.
Once logged in, the remaining applications understand that the user is already authenticated. In the background the applications receive authorization from the Active Directory server.
A user (and the organization) does not have to maintain separate usernames/passwords for each application.
If the single sign on system fails, then the user will not be able to access any of the applications.
Increasingly, social media sites such as Google and Facebook provide SSO services to other websites. For example, a user can use their Facebook account to log in to another site. Using Facebook for Single Sign On is a bad idea because Facebook will collect data about your visits to other websites and the websites will collect data from your Facebook account. - Remote Authentication Dial-In User Service (RADIUS) – RADIUS, or Remote Authentication Dial-In User Service, is a server that has three components
- Protocol
- Server
- Client
- Protocol
The Network Access Server is a Client of the RADIUS Server. When a user attempts to log in to the client, the client sends user information to the RADIUS server. The client and server encrypt their data with a shared secret, but the communication between the user and the client are not encrypted.
The RADIUS server receives connection requests and authenticates the user. RADIUS does not allow different privilege levels (all users are effectively superadmins). A RADIUS server combines authentication and authorization.
Authentication
- Many methods are possible including PPP, PAP, and CHAP
- The client sends the RADIUS server the user’s username and encrypted password
- The RADIUS server replies with
- Accept – the user is authenticated
- Reject – the user is rejected (credentials invalid)
- Challenge – the user must provide additional information
- Accept – the user is authenticated
- The client sends the RADIUS server the user’s username and encrypted password
Authorization
- Authorization tells the client what privileges to assign to the user
Accounting
- Accounting data is transmitted at the beginning and end of a session
- LDAP – LDAP stands for Lightweight Directory Access Protocol or LDAPS (for secure access). LDAP is essentially an address book. LDAP is governed by the X.500 standard.
LDAP includes a server called a Directory Server Agent, which typically speaks on port 389 or 636 for LDAPS. A client connects to the server.
A client can do the following (a client may have permission to do only some of these)- Add
- Delete
- Modify
- Search
- Add
For example, a photocopier with “scan to email” capabilities would connect to the LDAP server and obtain e-mail address entries for the various users in the office.
- Kerberos – Kerberos is a protocol that allows clients and servers to authenticate with each other and prove their identities. The server knows that the client is legitimate, and the client knows that the server is legitimate.
The Kerberos protocol protects against eavesdropping and replay attacks. Kerberos uses UDP port 88. Kerberos provides encryption over an unsecure network.
Kerberos’ current version is V5. It was developed by MIT and made available for free.
All versions of Windows including Windows 2000 and later use Kerberos for authentication by default (although other protocols can be used). Kerberos is used by Windows to join a client to a Windows domain.
Most common versions of UNIX also use Kerberos.
If a client wishes to connect, the following procedure is followed.- The client calls the Authentication Server (AS) to obtain authentication.
- The authentication server takes the client’s username and sends it to another server called the Key Distribution Center (KDC).
- The KDC runs a service known as the Ticket-Granting Service (TGS), which maintains a secret key.
- The KDC issues a ticket known as the Ticket-Granting Ticket (TGT) and encrypts it with the secret key.
- The encrypted key is sent back to the client.
- The client calls the Authentication Server (AS) to obtain authentication.
Let’s look at how a user would log in to a Windows machine
- A user would like to log in to a local Windows machine (the client), with a username and password. Even on a corporate network, the password should not be sent to the server (domain controller) in plain text.
- The local Windows machine encrypts/hashes the password.
- The client sends the user ID to the authentication server (in plain text), but not the password.
- The Authentication Server verifies that the client is in the database. The AS creates a secret key from the hash of the user’s password (that is stored on the server) and returns to the client the following messages
- A TGS Session Key, which is encrypted with the newly created secret key (Message A) – i.e. encrypted with a hash of the user’s password
- A TGT, which includes an expiry date and the client’s network address, all encrypted with the TGS’s secret key (Message B)
- A TGS Session Key, which is encrypted with the newly created secret key (Message A) – i.e. encrypted with a hash of the user’s password
- The client takes the TGS Session Key and decrypts it with the hash of the password that the user entered earlier. If the user entered the wrong password, then the client will be unable to decrypt the TGS Session Key. If the user entered the correct password, then the client will be able to decrypt the TGS Session Key.
- The client uses the decrypted TGS Session Key to communicate with the TGS
- If the client wants to request additional services
- The client sends additional messages to TGS
- Specifically, the client sends Message C, which is the TGT from Message B and the ID number for the requested service
- The client also sends message D, which is the authenticator (client ID and time stamp), encrypted with the Client/TGS
- Specifically, the client sends Message C, which is the TGT from Message B and the ID number for the requested service
- TGS obtains Message B from Message C and decrypts it (Only TGS has the encryption key for Message B). TGS uses this to decrypt Message D.
- If the Client ID in Message C and Message D match, then the client is authenticated
- TGS sends additional messages
- Message E is the Client-to-Server Ticket, which includes the client ID, network address, and expiry, encrypted using the service’s secret key
- Message F is the Client/Server Session Key, encrypted with the Client/TGS Session Key
- Message E is the Client-to-Server Ticket, which includes the client ID, network address, and expiry, encrypted using the service’s secret key
- The client takes Message E and Message F and uses them to authenticate with the Service Server
- The client sends
- Message E from before
- Message G, which is an authenticator, including the client ID, and timestamp
- Message E from before
- The Service Server decrypts Message E with its own secret key and obtains the Client/Server session Key. It uses this key to decrypt Message G. If they match, then the client is authenticated with the service
- The Service Server sends Message H to the client, which includes the timestamp in Message E, encrypted with the Client/Server Session Key
- The client decrypts Message H. If the timestamp on Message H is correct, then the client knows it can trust the server. A rogue agent could issue a fake message but would not be able to match the timestamp.
- The client sends additional messages to TGS
- The local Windows machine encrypts/hashes the password.
The encrypted key will expire, but if the user is logged in, the key will renew (the client will automatically contact the server and obtain an updated key).
To communicate with another node, the ticket is sent back to the service. The TGS verifies that the user is permitted to access the service and then sends the ticket to the Service Server (SS).
Kerberos has a single point of failure, which is the authentication server.
Kerberos also requires the clients, servers, and services to be responsive (since timestamps must match on all devices). That means that all devices must have synchronized clocks. If a client/server issues a ticket/message with a timestamp that doesn’t match due to a clock that is out of sync, then the system will fail. Clocks must not be more than five minutes apart (they don’t have to have the exact time).
- Local Authentication – Local Authentication means that we store the username and password on the local device.
Every device comes with the option to store a local username and password, which can be used if the remote authentication server is unavailable.
To avoid security issues, we should create a unique local username and password on each device and store them in a secure database. We should not use the default local username.
There are tools (especially on Windows machines) that automatically change the local username and password on a daily or monthly basis, according to a predefined formula. An administrator needing to log in with a local account can use a tool to determine the current local password. The local username and password can be unique for each computer. - 802.1X – IEEE 802.1X is a standard for Network Access Control. It allows a device to authenticate when connecting to a LAN or WAN.
There are three devices involved
- The supplicant is the device that chooses to connect to the LAN/WAN. It could be a laptop, desktop, smartphone, tablet, or other computing device
- The authenticator is a network device that allows/denies access. It could be a switch, a router, a firewall, or a proxy server.
- The authentication server is a server that decides whether a device should be granted access
- The authenticator is a network device that allows/denies access. It could be a switch, a router, a firewall, or a proxy server.
- The procedure
- The supplicant connects to the network
- The authenticator (switch) detects the new supplicant and automatically sets the port to an unauthenticated status. Only traffic related to 802.1X is permitted while the port is set to an authenticated status.
- The authenticator sends frames to the supplicant. These frames demand that the supplicant provide credentials such as a user ID. The frames are sent on the local network segment to a specific address (01:80:C2:00:00:03). The supplicant listens for messages on this address.
- The supplicant replies to the message with an EAP-Response Identity frame
- The authenticator sends the supplicant’s response to an authentication server
- The authentication server and the supplicant negotiate an authentication method. The server and the supplicant may support different methods of authentication and must agree on one that both understand. The negotiation methods are transported through the authenticator.
- The authentication server attempts to authenticate the suppliant. If successful, the authenticator changes the port status to authorized. If unsuccessful, the authenticator keeps the port status as unauthorized.
- When the supplicant logs off or is disconnected, the authenticator changes the port status back to unauthorized. When the supplicant logs off, it sends an EAPOL-Logoff message to the authenticator.
- The supplicant connects to the network
Security Risks
- A hacker can physically insert himself between the port and the authenticated computer; and then use the authenticated port
- A DDOS attack can take place. A hacker can create EAPOL-logoff messages with the MAC address of the supplicant and send them to the authenticator, forcing the port to go into an unauthorized state. This would force the supplicant to continually go offline.
- Extensible Authentication Protocol (EAP) – Extensible Authentication Protocol is a system for authenticating with a wireless network.
- EAP is a framework for providing authentication, but there are more than 40 possible methods that can be used, depending on the specific vendor of the equipment.
- RFC 5247.has defined EAP
- Each vendor may have more specific requirements and new protocols are being developed all the time
- Within EAP are several methods, including
- LEAP
- Lightweight Extensible Authentication Protocol
- Developed by Cisco
- LEAP is not supported by Windows but is supported by many third-party applications
- Cisco does not recommend using LEAP anymore because it does not protect user credentials
- Lightweight Extensible Authentication Protocol
- PEAP
- Protected Extensible Authentication Protocol
- Originally, EAP assumed that communications would be secure; therefore, it did not provide a mechanism to secure the data being transmitted.
- PEAP corrects this by providing a secure TLS tunnel
- A server-side certificate is used to create a PKI tunnel
- Protected Extensible Authentication Protocol
- EAP-NOOB
- Nimble out-of-band authentication for EAP
- Used by devices that do not have preloaded authentication information such as Internet of Things devices
- The user must assist the device in connecting via an out of band channel
- There are different connection options including QR codes and NFC
- Ephemeral Elliptic Curve Diffie-Hellman (ECDHE) exchange takes place over the in-band EAP channel. The user then provides the out-of-band channel message from the server to the device or from the device to the server, depending on what is required.
- EAP-FAST
- Flexible Authentication via Secure Tunneling
- Designed by Cisco to replace LEAP
- Three parts
- In band provisioning via Diffie-Hellman. The client is provided with a shared secret.
- Tunnel establishment. A tunnel is established between the server and the client.
- Authentication. The user is authenticated
- In band provisioning via Diffie-Hellman. The client is provided with a shared secret.
- Flexible Authentication via Secure Tunneling
- EAP-TLS.
- EAP – Transport Layer Security
- Uses TLS (Transport Layer Security) as its protocol.
- All wireless manufacturers support EAP-TLS
- Considered very secure
- EAP-TLS requires a client-side certificate. When a system is authenticated with a certificate, a password is not required. Even if a hacker obtained the username/password, without a certificate, the hacker would not be able to connect to the Wi-Fi.
- EAP is not implemented as widely as it should be because it requires the certificate
- EAP – Transport Layer Security
- EAP-TTLS
- EAP Tunneled Transport Layer Security
- Extends TLS so that the client does not require a certificate. Instead, the server creates a tunnel with the client. The client can then authenticate to the server using a legacy password or other authentication method. The tunnel protects the client from eavesdropping.
- EAP Tunneled Transport Layer Security
- LEAP
- EAP is a framework for providing authentication, but there are more than 40 possible methods that can be used, depending on the specific vendor of the equipment.
Finally, we must look at Risk Management, both from a security approach and a business approach. How do we evaluate risks to our infrastructure?
- Threat Assessment – A threat assessment is a process for evaluating potential threats. We must determine
- Whether the threat is real
- How serious the threat is to our organization if it takes place
- How likely it is for the threat to take place
- Whether the threat is real
We don’t know what we don’t know. It is not possible to determine every threat that could ever occur. We should develop a framework for brainstorming potential threats that considers the types of people who might attack our organization and their motivations.
A threat assessment should involve subject matter experts.
- Vulnerability Assessment – A vulnerability assessment evaluates our systems for security risks.
First, we should make a complete inventory of all the devices on our network. Then, we should systematically evaluate each one to determine all the ways that it can be attacked (physically, remotely, via a configuration change, via an API, etc). - Penetration Testing – A penetration test is when an outside person is hired to find security risks in an organization. Some organizations give the penetration tester permission to attack any system and discover all possible security holes because they want to make their systems better. Others limit the penetration tester’s scope because they do not want to admit to their customers, employees, shareholders, or themselves that there are security flaws in their systems.
A penetration test does not have to be electronic in nature. It can be as simple as an unauthorized person walking into a building and stealing papers from a filing cabinet.
To properly perform a penetration test, the tester must know- The common attack methods employed by hackers
- The type of information and resources that a hacker would like to steal from the organization (intellectual property, financial information, etc.)
- The common attack methods employed by hackers
The tester should obtain written approval from the highest levels of the organization before proceeding with the penetration test. Many of the actions performed by the tester could be considered crimes (trespassing, unauthorized access to a computer system, theft, fraud, etc.). If the tester is caught in the act, local staff may report him to the police.
- Posture Assessment – a posture assessment shows the organization’s overall security status. It shows the organization’s ability to defend itself against attacks, the types of risks that the organization faces, the value of the organization’s data, and the types of defences in place. The posture assessment is a tool that management can use to improve the organization’s overall security.
How do we evaluate risks to our business?
- Process Assessment – the process assessment is a procedure for determining whether a specific business process is secure or where its vulnerabilities lie. For example, if an organization has a process for paying an invoice, the assessment will determine whether an attacker could trick the finance department into paying a fake invoice. The assessment will show the vulnerabilities and how to repair them.
- Vendor Assessment – a vendor assessment is a procedure for determining whether external vendors put the organization at risk. It also determines whether the vendors have security policies that are in line with that of the organization. A vendor may have remote access into our systems and may store our data on their systems. Thus, even if our own security systems are strong, an attacker could exploit a weakness in one of our vendors.
We must work with our vendors to improve their systems. - Security Information and Event Management (SIEM) – SIEM stands for Security Information and Event Management. It can be a dedicated appliance, or it can be a software application. Many SIEM systems are cloud-based and share threat & intelligence data with multiple customers.
Most network devices generate and store security data. For example, a router may detect traffic from an unauthorized location or a server may detect, and log failed login attempts.
An SIEM aggregates this security data from multiple locations including routers, switches, servers, IP Phones, network storage appliances, video recorders. The SIEM may convert the logs and data into a common format. The SIEM allows a security administrator to view all security events in one place (and in one format) instead of having to log in to multiple devices.
The SIEM can also allow a network administrator to correlate events across multiple devices. For example, if a hacker gains unauthorized access to a network through the router and then fails to log in a file server multiple times, both events can be correlated as coming from the same source IP address and occurring at the same time.
The SIEM can automatically send alerts to a network administrator either via SMS or e-mail. The SIEM can be set to trigger alerts when specific events occur.
If network devices are in different time zones, the SIEM can automatically adjust the log times to the time zone of the security administrator. The SIEM can also remove duplicate events from the log.
Some examples of logged data- Failed log in attempt on a server or router
- Firewall refuses traffic from a specific IP address
- IP address is engaged in port sniffing
