4.4 Compare and contrast remote access methods and security implications
- Site-to-Site VPN
- Client-to-Site VPN
- Clientless VPN
- Split Tunnel vs Full Tunnel
- Remote Desktop Connection
- Remote Desktop Gateway
- SSH
- Virtual Network Computing (VNC)
- Virtual Desktop
- Authentication and Authorization Considerations
- In-Band vs Out-of-Band Management
How do we keep the network secure but still allow external users to connect? As mentioned earlier, we can use a VPN or Virtual Private Network.
A Remote Access VPN allows users to connect back to a corporate network, typically through their computer. A Site-to-Site VPN allows two offices to connect to each other and pretend like they are part of the same physical network. A Site-to-Site VPN typically applies to the site’s router and not to individual devices on the network.
- The performance on a VPN is affected by the quality of the user’s internet connection, by the quality of the corporate network’s internet connection, by the number of active users, and by the type of resources being accessed.
- When there are multiple sites that need to be connected, a site-to-site VPN should be replaced by a WAN
A VPN can be secured with IPSec – a set of protocols that allow hosts to exchange packets securely. IPSec has several modes of operation, including
- Tunnel Mode. The Tunnel Mode encrypts the source, destination, and contents of every packet. Essentially, it establishes a secure tunnel between two network devices where data can travel securely. The devices that are establishing the tunnel are not necessarily the devices that are creating the traffic. For example, a router could be sending traffic on behalf of a server inside the network. An outsider will not be able to examine the source, destination, or contents of any traffic.
- Transport Mode. The Transport Mode only encrypts the contents of the packet. It does not encrypt the source or destination. An outsider will be able to examine the source and destination. Transport Mode is established by the two network devices who are communicating, and not by the routers on the edges of the network.
- SA. An SA, or Security Association is an algorithm and key that are used to encrypt traffic in an IPSec tunnel. Each direction of communication requires a separate SA. Therefore, most IPSec tunnels will require two SAs.
- There are four methods of connecting a tunnel. Consider that two computers (each inside a separate network and behind a router) would like to communicate securely across the internet. How can an IPSec tunnel be established?
- Machine-to-Machine. Two computers (or smartphones) establish a tunnel and communicate. This is not practical because each computer will expend a substantial amount of computing power encrypting and decrypting the IPSec traffic.
- Router-to-Router. It is assumed that the connection between the computer and the router (on the internal network) is secure. The routers establish an IPSec tunnel. The computers no longer encrypt traffic between themselves and the routers. The routers encrypt all traffic between themselves.
- Machine-to-Machine and Router-to-Router. This combines the previous two scenarios. Each machine establishes an IPSec tunnel with the router on its network, and the routers establish an IPSec tunnel between themselves.
- Remote User. A remote user connects to a router through an IPSec tunnel, and then establishes a secondary IPSec tunnel to connect to a device deeper in the network.
- Machine-to-Machine. Two computers (or smartphones) establish a tunnel and communicate. This is not practical because each computer will expend a substantial amount of computing power encrypting and decrypting the IPSec traffic.
- Transport Mode. The Transport Mode only encrypts the contents of the packet. It does not encrypt the source or destination. An outsider will be able to examine the source and destination. Transport Mode is established by the two network devices who are communicating, and not by the routers on the edges of the network.

- Tunnel Mode Encryption. The tunnel mode is the method for encrypting the traffic. Consider that two routers have created an IPSec tunnel and that behind each router is a computer that wants to communicate. What is the order of operations?
- The computer generates some data and places it in a packet.
- The computer puts the address of the remote computer in the header of the packet (or the address of the network that it is sending it to, when the network employs NAT – more on this later).
- The computer sends the packet to the router (through the switch)
- The router encrypts this packet, including the headers
- The router encapsulates this packet inside a larger packet and adds the recipient’s router address to the header
- The router sends the packet to the destination router
- The destination router removes the outer header, decrypts the packet, and forwards it to the computer inside its network
- Neither computer is aware of the existence of the IPSec tunnel
- Tunnel encryption works through the following security protocols
- AH. Authentication Header. When AH is used, the original IP header (created by the computer that generated the data) is visible to outsiders, but the contents are protected. AH protects the integrity of the data. That is, the recipient can be sure that the sender listed on the packet is in fact the true sender.
- ESP. Encapsulating Security Payload. ESP encrypts the contents of the data, but it does not guarantee integrity.
- It is recommended to use both AH and ESP, thereby providing privacy and integrity.
- AH. Authentication Header. When AH is used, the original IP header (created by the computer that generated the data) is visible to outsiders, but the contents are protected. AH protects the integrity of the data. That is, the recipient can be sure that the sender listed on the packet is in fact the true sender.
- IPSec algorithms
- IPSec is a framework for exchanging data, but the contents of the framework vary from vendor to vendor and network to network. Just like there can be many different models of vehicles on a road, all following the same traffic rules, there can be many different types of algorithms to exchange data within a tunnel.
- Many different encryption algorithms can be used. This flexibility allows an algorithm to be replaced when it is discovered to be weak.
- Methods include
- Diffie-Hellman key exchange with public key signing
- MD5 and SHA-1 hashing algorithms to ensure data integrity
- IPSec is a framework for exchanging data, but the contents of the framework vary from vendor to vendor and network to network. Just like there can be many different models of vehicles on a road, all following the same traffic rules, there can be many different types of algorithms to exchange data within a tunnel.
- IPv4 vs IPv6. IPSec is integrated into all IPv6 packets by default, but not IPv4 packets. When IPv4 was designed, security was not a primary consideration. As the internet grew, the design of IPv6 required security to be integrated into all communications. A device can use IPv6 and not activate the IPSec feature however.
- The computer generates some data and places it in a packet.
In a Full Tunnel VPN, all traffic is routed through the VPN, but in a Split Tunnel VPN, only specific traffic is routed through the VPN.
The advantage of a split tunnel is that it reduces bottlenecks. Consider a corporate user working from home. The user needs to access network resources such as a shared drive and corporate finance applications. This traffic must go over the VPN. The user is also watching YouTube videos in the background. There is no reason to route YouTube videos over the corporate network (requiring encryption on both sides). YouTube traffic can travel over the user’s home internet connection.
In addition to providing internet security, Transport Layer Security is an alternative to IPSec VPN. A TLS VPN is useful when the network uses NAT.
An Always-On VPN is just like it sounds. It is a VPN that is always on. Typically, an Always-On VPN is part of a hardware appliance, but it could also be software-based. When the VPN detects an active internet connection, it automatically attempts to re-establish the VPN.
For security purposes, an Always-On VPN can block traffic from travelling over the internet when the VPN is not running. This would prevent a user from inadvertently disclosing his true location to websites that shouldn’t know it.
If a user requires access to a specific computer or device on the network, we can use the Remote Desktop Connection (RDC). RDC allows a user to have remote keyboard, mouse, and video control of a computer. It also allows a user to share printers and files. It can be established via the Microsoft Remote Desktop Protocol, or via another application such as Team Viewer or Log Me In.
A remote user wanting to connect to a computer might need to have the following
- Connect to the computer via RDC using the computer’s public IP address, if it has one
- Log in to the computer with the user’s credentials. The user must have permission to log in to that computer.
If the computer that we want to connect to does not have a public IP address, then the user might need to do the following
- Connect to the corporate network via a VPN.
- Connect to the computer via RDC using the computer’s LAN IP address. The computer must have RDC enabled.
- Log in to the computer with the user’s credentials. The user must have permission to log in to that computer.
Using third party software
- The remote user will not need to connect to the VPN.
- The computer on the corporate network will need to have the Team Viewer, Log Me In, or other software installed.
- The software establishes a connection to a server. The remote user also installs the connection client, which connects his computer to the same server, which allows him to reach the device.
Clearly there is a problem. If we want a remote user to be able to connect to a Windows server or computer on the internal network, then that device must have a public IP address (i.e we are exposing the remote desktop connection to the entire internet, which is bad), or we must force the user to use a VPN, which may not be practical, or we must force a user to install third party software.
There is another way. It is called the Remote Desktop Gateway. The Gateway is a server that allows an external user to connect to internal devices without any third-party software and without forcing those devices to carry public IP addresses. It does three things
- Create an SSL tunnel between the remote user and the Remote Desktop Gateway on the corporate network
- Authenticate the remote user via Active Directory, RADIUS, or another system
- Connect the remote user to the network resource (the server or computer that must be accessed)
There are other ways to remotely connect and control a computer. They include
- SSH. SSH is a protocol that allows a user to securely connect to a remote device via a terminal like PuTTY.
SSH is used for remotely configuring network equipment and servers running Linux. SSH originally did not provide a graphical user interface but there are some add on Linux applications that will do so.
SSH by default encrypts all data. - Virtual Network Computing (VNC) is a system that allows a user to remotely control a computer via the Remote Frame Buffer Protocol. The protocol is open source and works with Windows, Mac, and X Window (a GUI system for Linux).
An administrator must install an application on the server or computer, which accepts incoming connections from remote users. A remote user installs a client application that connects to and controls the server.
VNC is not secure by default, but there are add on applications that can make it secure. We can also tunnel the VNC connection over an existing SSH connection.
These connections that I’ve talked about are all considered “in bound” management. That is, we have one network and we are trying to administer our network equipment over the same network that those devices are running.
What if there is a problem with the router that brings down the network we can no longer access it remotely? Or what if we need to perform an operating system upgrade on a switch or server, which causes it to reboot? We need a back up method to get in. This is called out of band management.
Looking at a piece of network equipment like a Cisco Router or Cisco Switch, there are three ways to get into it
- The physical console port. The physical console port looks like an ethernet port, but requires you to connect the device to your computer via a special cable known as a console cable, which has a special pin out. To use the console port, an administrator must be physically present at the device.
- The management port. The management port allows you to connect an ethernet cable to the switch. We should set up a management VLAN and connect the various management ports to it. The management port will then be configured to have an IP address on that VLAN.
- Remote access through SSH or Telnet. Telnet is not secure and not recommended. Telnet and SSH operate over the existing physical network that the devices are connected to.
So what?
If we have only one network device, we can connect the console port to a special 56K dial-up modem. The most popular modems are made by US Robotics and are still quite common. The modem allows us to connect to the network equipment even if the network is down or the internet connection is down. Only a phone line is required.

When we have many devices, we can install what is known as a console server. The console server looks like a normal switch. We connect a normal ethernet cable between the console port on each device and the console server. The console server can be configured to communicate with each console port.

We connect the console server to the internet, and now we can remotely connect to the console server, and then use it to connect to and configure the network devices. It is recommended that we use a separate internet connection.
This can get tricky when the network is large and widespread because the various IDFs may not connect via copper, only fiber. Thus there may not be a copper link between the location where the switch is and the location where the console server is.
The perle console servers include the following features
- Modular design, which allows us to substitute ethernet style ports for USB ports. That means we can have remote USB access to a device.
- Built in cellular modem that provides remote access to the server without having to connect a separate modem.

We can set up a separate physical network for the management. This might take a substantial amount of equipment to create. And the question becomes, how do we manage the devices on the management network?
That covers network devices. But what about servers? What if we need to remotely upgrade the operating system of a server or want to remotely change the BIOS settings? On the back of many servers, you will find a “remote access” port. On a Dell server, it is known as an iDRAC port, and on an HP server, it is known as an iLO (Integrated Lights Out) Port.
This “port” is actually a card that fits inside the back of the server. The card is a small modular computer, like a server within a server. It connects to the ethernet network (which can be the same network, a separate management VLAN, or a separate physical network) and allows us to remotely connect to the server.
If we have many servers, we can configure the remote access port to connect to a central server where we can manage the equipment. iLO and iDRAC are not free and require licenses to use more advanced features.
We’ve talked about Authentication and Authorization before, but how can we make sure that only legitimate users are able to connect to our network?
- It is most practical to assign each user a single account. This is usually a Microsoft Active Directory account.
- When a user is also an administrator, we may assign him a second account, which provides administrative access.
- We can enforce different roles and permissions on each account or group of accounts. Each user should have access to only the devices that he needs to do his job, and each user should only be given the exact privileges he needs within those devices. For example, an administrator may be given remote access to the server to view content but not be given permission to make any changes.
- The users will connect to the corporate VPN or other remote access tool and authenticate with their Active Directory accounts.
- Use two-factor authentication where possible.
- We can configure TACAS+ on most network devices. The TACAS+ system allows the switch to verify an administrator’s credentials with the Active Directory Server. This allows an administrator to log in to the device with his AD credentials.
- We should enforce individual or group user permissions on network equipment as well. This will ensure that administrators only have the specific permissions that they require to do their job.
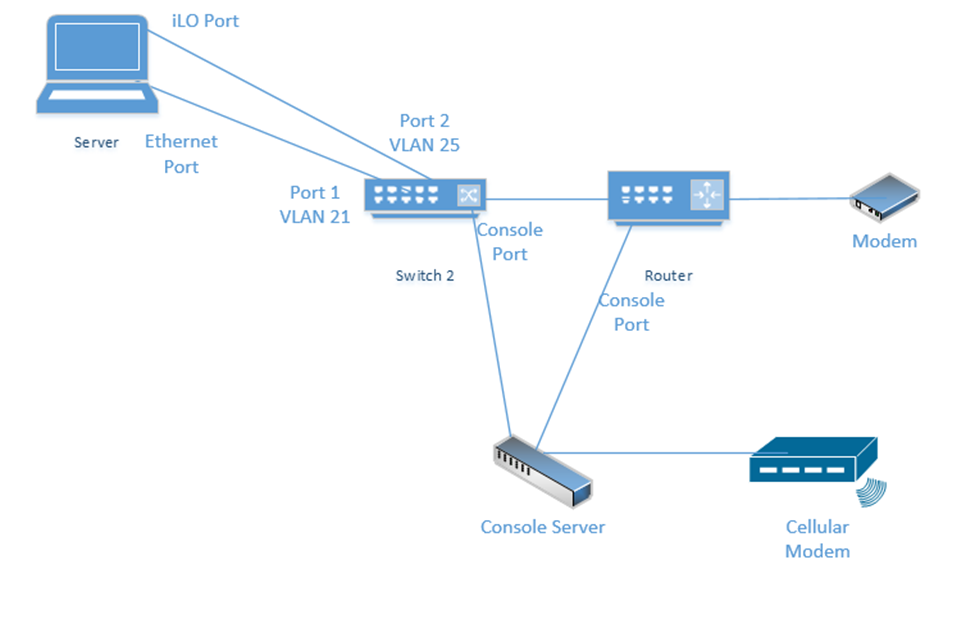
Here is a typical set up
- On the left, we have a server.
- The server’s ethernet port is connected to the switch port one, which is configured for VLAN 21 (remember that we should change the default VLAN to prevent VLAN hopping).
- The server’s iLO port is connected to the switch port two. We set up VLAN 25 as the management VLAN. Thus, we can configure the server as long as we are connected to the network (either locally or remotely). We can also use Remote Desktop to access the server via VLAN 21.
- The switch and router connect to a console server via their console ports. Even if the primary internet connection stops functioning, we can still configure those devices because the console server connects to the internet via a cellular modem.