5.3 Given a scenario, use the appropriate network software tools and commands
- Software Tools
- Wi-Fi Analyzer
- Protocol Analyzer / Packet Capture
- Bandwidth Speed Tester
- Port Scanner
- iperf
- NetFlor Analyzers
- Trivial File Transfer Protocol (TFTP) Server
- Terminal Emulator
- IP Scanner
- Command Line Tool
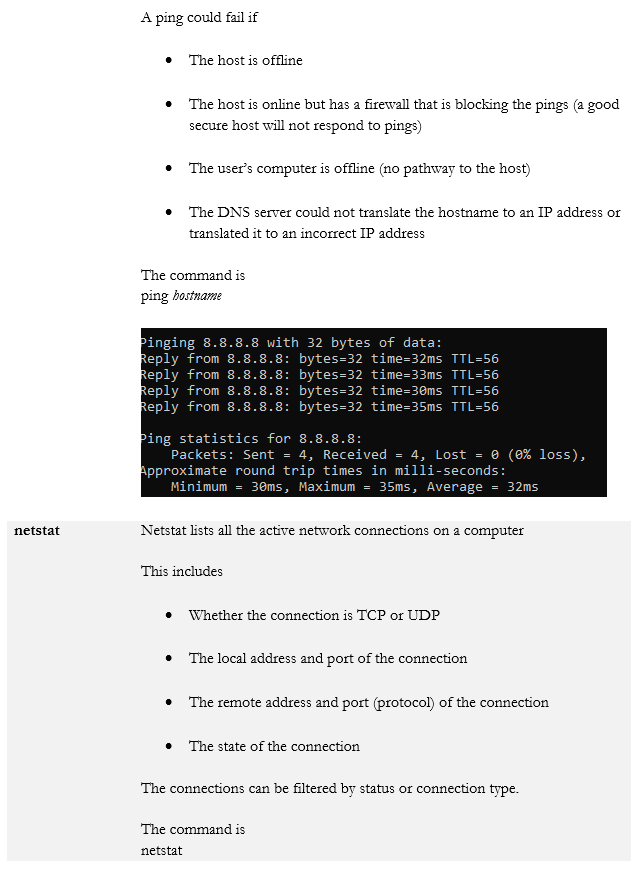
- ping
- ipconfig / ifconfig /ip
- nslookup / dig
- traceroute / tracert
- arp
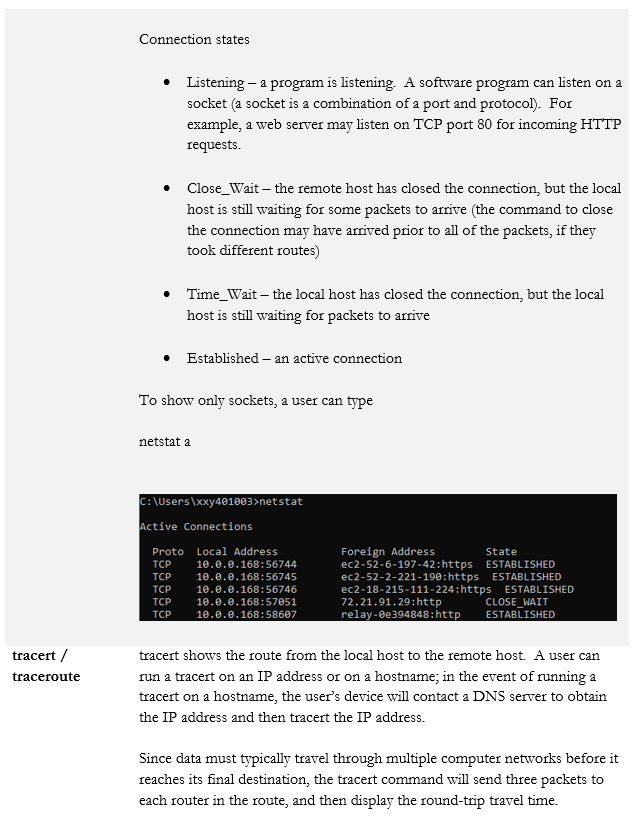
- netstat
- hostname
- route
- telnet
- tcpdump
- nmap
- Basic Network Platform Commands
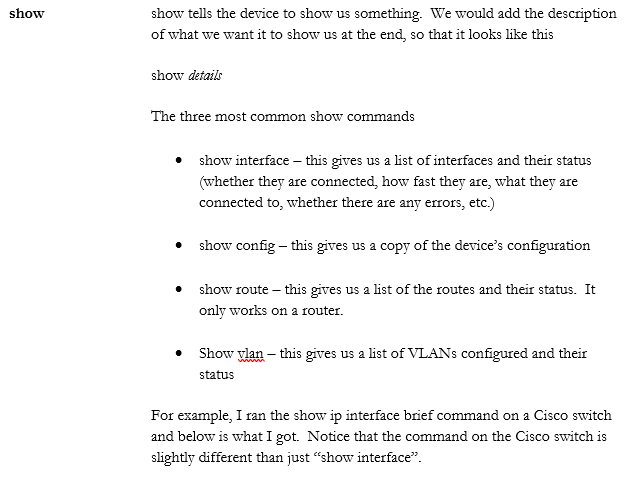
- show interface
- show config
- show route
We mentioned the hardware tools that you should carry. Now let’s look at some software tools. Some of these tools are integrated into hardware like the network analysers that I mentioned previously, but you may also install their respective software components onto a laptop.
- Packet Sniffer/Protocol Analyzer. It might also known be known as a packet analyzer or network analyzer. This lets us intercept packets on a wired or wireless network so that we can analyse them. We may also be able to generate traffic so that we can test our network. We can also determine whether traffic is being encrypted or if it sent in plain text. A good packet sniffer is called WireShark. Packet sniffing another person’s network without permission might be illegal.
- Port Scanner. A port scanner tells us which ports are open on a given network or device. We can use it to test the effectiveness of our firewall and to detect rogue devices.
- IP Scanner. An IP Scanner tells us which devices on our network are active. We give it a range of IP addresses, and it scans through them to see which ones return a response. It will identify each device by its IP Address, MAC Address, Hostname, and Open Ports. It may also be able to tell us the manufacturer of the device (or at least the manufacturer of its network card).
The Port Scanner and the IP Scanner may be integrated into the same software, such as the Advanced Network Scanner, which is available for free.
A properly configured device should only respond to requests made by devices authorized to access it. Thus, we can use the scanner to determine whether- A device is present on our network, but shouldn’t be
- A device is not responding to anybody, even those who are permitted to access it, in which case it may be offline or misconfigured
- A device is responding to people who have no authorization to access it, in which case its security settings are misconfigured
- A device is responding but has open ports that should be closed and/or closed ports that should be open.
- A device is present on our network, but shouldn’t be
- Wi-Fi Analyser. A Wi-Fi analyser can measure wireless signals and networks. Ekahau and Air Magnet SurveyPro are examples of Wi-Fi analysers.
- Bandwidth Speed Tester. A speed tester can tell us the upload and download speed of a connection. It may also tell us about jitters, latency, and packet loss.
Speed testers are available on the internet and can include speedtest.net and fast.com. The results of the speed test are only as good as the speed test website; if the server is slow, then the results might be slow.
One of the best speed testing applications is iperf. You can use iperf to create an end to end speed test between a client and server. - Net Flow Analyser. A Net Flow Analyser allows us to determine which the traffic on our network is coming from, and where it is going. This way, we can identify where the sources of congestion are.
Many software defined networks have this tool built in to their administrative applications. For example, Cisco Meraki allows you to analyse and shape traffic via an online interface. - TFTP Server. A TFTP Server is an application that you can run on your laptop. The most common purpose you will use it for is to upgrade the operating system on a switch or router. You can download an image of the router’s operating system onto your laptop and then use the TFTP software to upload it to the switch. This is useful when the organization does not have a reliable repository for the switch or router operating systems.
- Terminal Emulator. A common Terminal Emulator is called PuTTY. PuTTY allows us to connect to and communicate with a server, switch, or other device, via console, SSH, or Telnet. PuTTY is an important program to have and it is free.
We can also perform testing from a command line. Some of the commands are in the table below.

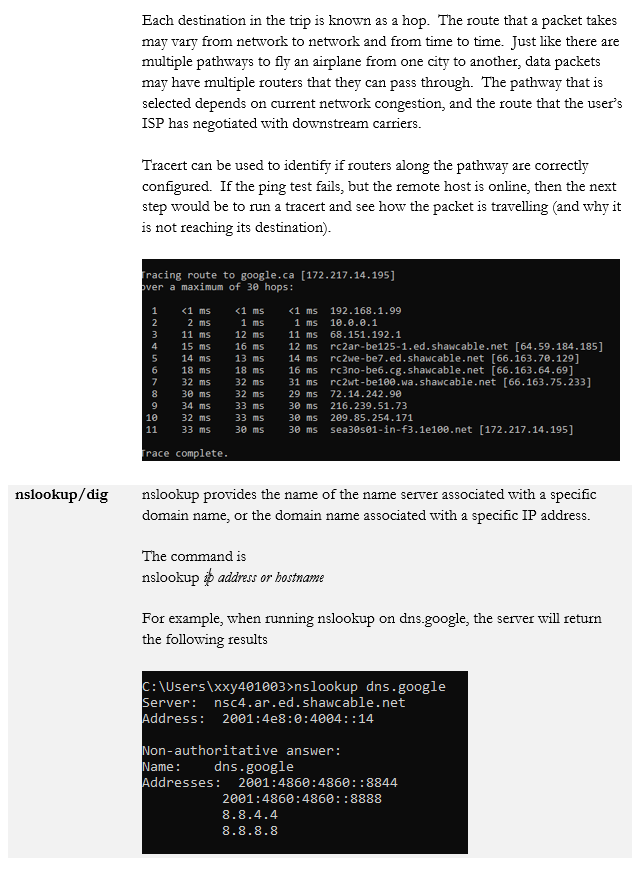
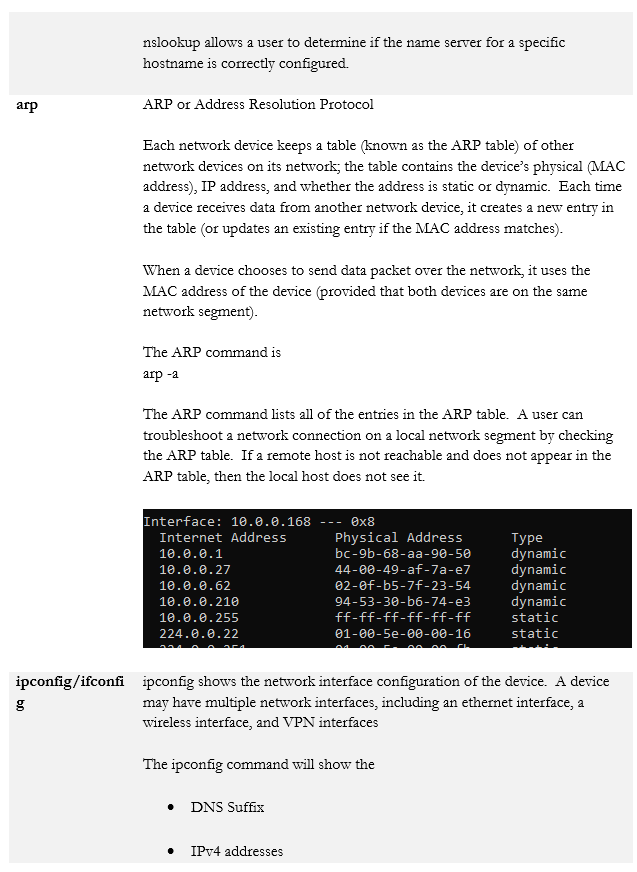
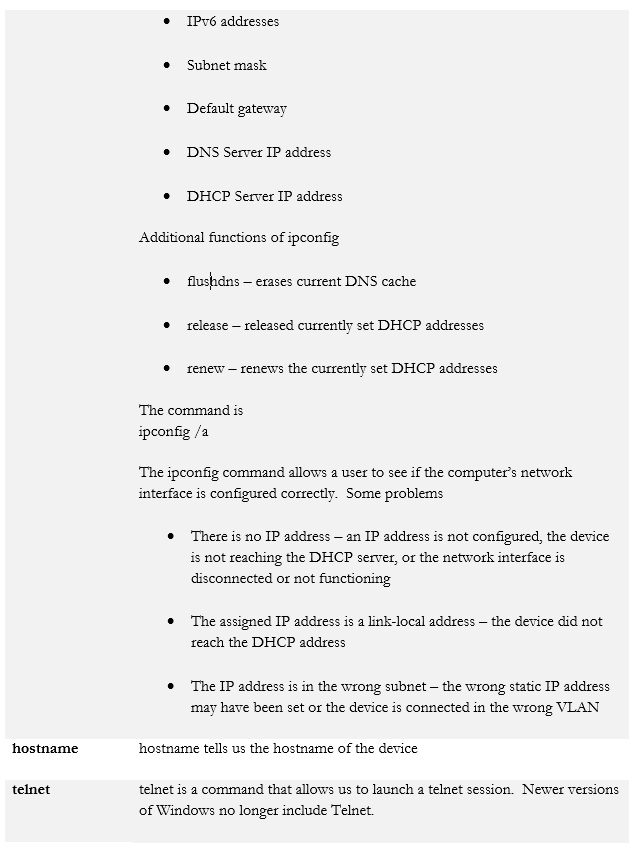
When we’re logged in to a router or switch, there are some commands we can run. Across the multiple makes and models of routers, switches, firewalls, and wireless access points you will encounter, there can be thousands of commands. It is not possible to list all of them here, but they generally follow a pattern.