1.1 Compare and contrast different types of social engineering techniques
- Phishing
- Smishing
- Vishing
- SPAM
- SPAM over Instant Messaging (SPIM)
- Spear Phishing
- Dumpster Diving
- Shoulder Surfing
- Pharming
- Tailgaiting
- Eliciting Information
- Whaling
- Prepending
- Identity Fraud
- Invoice Scams
- Credential Harvesting
- Reconnaissance
- Hoax
- Impersonation
- Watering Hole Attack
- Typosquatting
- Pretexting
- Influence Campaigns
- Hybrid Warfare
- Social Engineering
- Principles (Reasons for Effectiveness)
- Authority
- Intimidation
- Consensus
- Scarcity
- Familiarity
- Trust
- Urgency
Let’s take a minute to define some terms
- A threat is something that can hurt you.
- A vulnerability is a flaw that the threat can use to gain access. By itself, a threat can’t do anything, but when the threat discovers a vulnerability it may take advantage of it.
- When the threat takes advantage of a vulnerability, we call that an exploit.
Look at the real world: bacteria are everywhere. Normally, bacteria are all over your skin, but can’t hurt you. They are a threat. But if you get injured – even a papercut – that is a vulnerability that the bacteria can use to get inside and infect you. The infection is an exploit.
We can’t get rid of all the threats, but we can identify and monitor them. If we think about the types of threats that are out there and the types of vulnerabilities that they like to exploit, then we can take steps to harden our defences. Threats, vulnerabilities, and exploits will be a common theme in this book.
Social Engineering
Social engineering is the attempt to use psychological methods to manipulate individuals into providing confidential information or access to systems.
Unlike malware, social engineering relies on human emotion
- Wanting to be liked
- Fear
- Wanting to help
- Intimidation
- Familiarity
- Hostility
A good book on social engineering is Social Engineering: The Art of Human Hacking by Christopher Hadnagy.
Phishing
Phishing is the attempt to obtain sensitive data by pretending to be a trusted entity. Phishing usually occurs through e-mail or telephone. Phishing is usually sent as a mass e-mail to thousands or millions of people.
Typically, a user will receive an e-mail asking them to sign in to their bank account or other account (PayPal, eBay, Amazon). The e-mail is fake, and the website that the e-mail leads to is fake (but appears to be real).
Typical phishing e-mails will say
- Your account has been compromised and you must log in to correct the issue
- Your account will be suspended if you don’t log in
- You have received a large payment (Interac eTransfer) and you must log in to accept the money
The hacker may register a domain that looks like the legitimate one. For example, the user may register www.paypa1.com instead of www.paypal.com. Or the hacker may register a domain that is completely unrelated to the original website and attach a subdomain that looks like the legitimate site. For example, the hacker registers fakewebsite.com and attaches the “www.paypal” subdomain to it, making www.paypal.com.fakewebsite.com. The users will see the first part of the URL “www.paypal.com” and think they are on a legitimate site, even though the user’s browser went to fakewebsite.com.
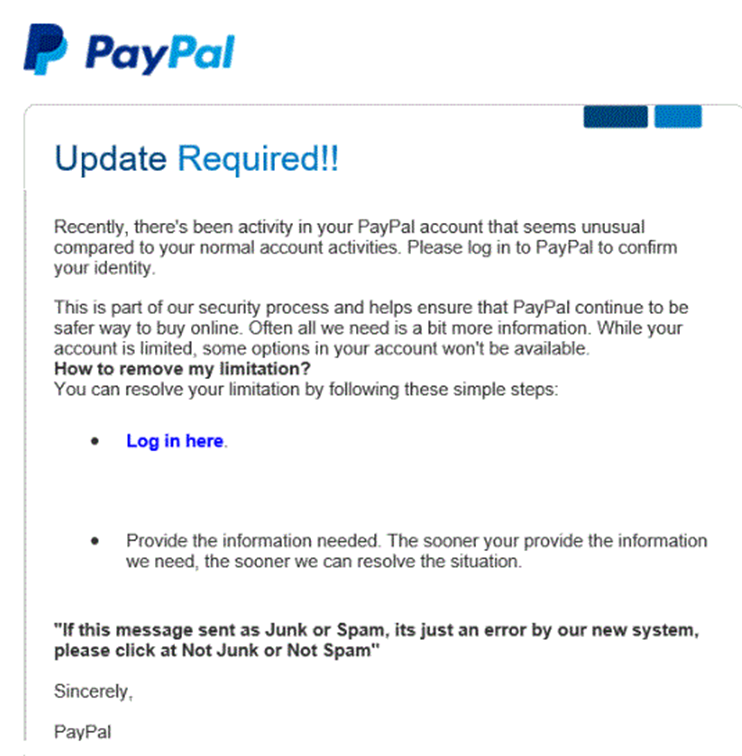
How do we prevent phishing?
- Proper user education to identify suspicious e-mails.
- Knowledge that legitimate e-mails from banks and other sites will contain the user’s full name while phishing e-mails will not (unless the sender has access to the user’s data)
- Phishing e-mails and/or websites may (but not always) contain poor grammar or spelling
- Phishing websites will not contain the correct URL. Users should always check that they have visited the correct URL.
- Knowledge that legitimate e-mails from banks and other sites will contain the user’s full name while phishing e-mails will not (unless the sender has access to the user’s data)
- Automated systems that detect and filter phishing e-mails. These systems are built into most web browsers and e-mail systems and verify that the e-mails originated from legitimate sources and that the websites are legitimate.
Smishing
Smishing is like Phishing but uses the SMS (text messaging) system. Technically, it could use other messaging applications like WhatsApp.
How to prevent?
- Don’t respond to text messages that are from numbers you don’t recognize
- Don’t click links sent via text message. If a phone is compromised, it may be used by attackers to send smishing messages to people in its contact list.
Vishing
Vishing is like Phishing but uses the telephone (VoIP) network. The thieves will place phone calls that appear to come from legitimate entities such as the IRS, a bank, or a credit card company. The thieves will attempt to obtain sensitive data such as credit card numbers or bank account numbers.
Common features
- The scammer will threaten the victim with legal action or arrest if they do not comply
- The scammer will ask the victim to purchase gift cards from a store and send them the numbers
- The scammer will speak with a foreign accent or bad grammar
How to Prevent?
- If a user receives a telephone call from somebody who is seeking sensitive information, they should
- Verify that the number is in fact legitimate
- Hang up and call the number back (as caller IDs can be spoofed)
- Verify that the caller will require the information (for example a bank will never ask a client for his/her PIN)
- Provide the required information through the legitimate online website of the purported requester (such as IRS.gov)
- Verify that the number is in fact legitimate
SPAM
SPAM is unsolicited marketing e-mails. The content of the SPAM may be legitimate or fraudulent. Billions of SPAM messages are sent each day at a very low cost.
How to prevent?
- Use a SPAM filter
- Do not provide your e-mail address to sites unless you trust them
- Report SPAM messages – this allows internet service providers to block traffic from IP addresses that are sending SPAM or allowing SPAM to be sent from their location
SPAM over Instant Messaging (SPIM)
SPIM is like SPAM but sent over instant messaging applications such as WhatsApp. An attacker may guess addresses (phone numbers) at random or hijack the contacts/directory from a legitimate but compromised phone. Most messaging applications have methods to stop SPIM because they can detect high volumes of messages.
Spear Phishing
Spear Phishing is like phishing, but it targets specific groups or people. The more precise the targeting, the higher the response rate.
A normal phishing attack could target millions of users. For example,
- A hacker could send a fake e-mail appearing to be from Bank of America to 1,000,000 e-mail addresses
- From those 1,000,000 addresses, only 250,000 might work
- The SPAM filter would block 200,000 from those 250,000
- From the 50,000 only 10,000 might have accounts at Bank of America
- 80% of those users might be smart enough to detect the phishing scam, in which case only 2,000 people respond
- The attack is shut down early on, and many users are unable to respond, so the hackers only collect data from 500 users
- The success rate is about 0.005%. Although it is low, the return on investment might be high. It may cost the hackers a few hundred dollars out the e-mail, but they might be able to collect at least $100 from each user (for a total of $50,000).
In spear phishing, the hackers identify specific customers of Bank of America for example. They may use a list stolen from the bank. The hackers customize the e-mail to include the name and other personally identifying information of each recipient. As a result, the SPAM filter will be less likely to identify the e-mail as SPAM, and the user will be more likely to respond.
Dumpster Diving
Dumpster Diving involves searching the garbage of a target. Individuals frequently throw out documents, USB drives, computer hard drives, and other items containing sensitive information.
Dumpster Diving is not necessarily illegal because items are considered public property/abandoned once put in the trash. Police and private investigators also use Dumpster Diving to collect evidence. If the dumpster is located on private property, it may be considered trespassing.
A company that is suspects it is being spied on might consider filling the dumpster with fake documents or with USB drives that are full of malware. This could serve to trick the enemy or identify them.
Dumpster Diving can occur within an office. For example, an office worker put sensitive papers into a trash can in his office during the day. These are later collected and stolen by a contracted janitor in the evening.
How to prevent
- Shred all sensitive documents before disposing of them. Use a cross-cut shredder. Vertical shreds can be put back together.
- There are multiple directives for shredding sensitive documents and computer storage components including DoD 5220.22. The type of shredding (the size of the shreds) depends on the sensitivity of the information; the more sensitive the information, the smaller the shreds.
- Require all employees to maintain a clean desk. All sensitive documents must be locked before the employee leaves for the day.
Shoulder Surfing
Shoulder Surfing is when a thief looks over the shoulder of a victim. Shoulder surfing can occur at a computer or at an ATM. The thief may watch the screen or the keyboard.
Shoulder surfing happens at offices, in airports, and on public transportation.
How to prevent
- Install shields at ATMs and debit/credit card terminals
- Install privacy screens on computers/laptops.
- If using a laptop on an airplane or other public place, the user should avoid doing anything sensitive and/or be wary of his/her neighbors/surroundings.

Pharming
Pharming causes a user’s computer to redirect to websites controlled by the attacker.
When you attempt to visit a website, your computer calls up a DNS server to find the address of the website. The DNS server is a directory that looks up the human-readable domain name (google.com) and finds the computer-readable IP address of the website (8.8.8.8).
It is difficult to manipulate the DNS server (as we will find out later). But the attacker can manipulate the “hosts” file on your computer. The hosts file allows you to hardcode a DNS entry, in which case, the computer will not consult the DNS server. For example, the attacker set up a malicious server on 9.10.11.12 and host a website that looks like the Bank of America website. Then the attacker would modify the hosts file on your computer to direct Bank of America traffic to 9.10.11.12.
Now, when you type in the domain name for Bank of America, your computer will not query the DNS server for the correct IP address – it will use the address in the hosts file. You will then see content from the attacker’s server (an illegitimate version of the BoA website), which can be used to steal your information.
Modification of the hosts file will usually not trigger an alert by the antivirus program.
How to prevent?
- Ensure that user access control is enabled, which can prevent unauthorized access to the hosts file
- Regularly check the content of the Windows hosts file
- Check the certificate on each website to ensure that it is issued to the owner of the website. In this example, the hacker may be able to forge the BoA website but probably won’t be able to secure it with an Extended Validation https certificate. The attacker may be able to secure it with a standard https certificate.
Tailgaiting
Tailgaiting is an attempt to obtain unauthorized access to a physical facility.
Many offices, industrial facilities, and data centers are controlled via electronic proximity card and/or biometric locks. When a legitimate user unlocks an entrance with their access card and/or biometric lock, an intruder can follow them into the building. Tailgaiting works because
- A person might hold the door open for a person who is walking behind him (doing otherwise might be considered rude)
- A person might not wait to verify that the door closed and locked behind him, and another person might follow him. The door lock might not work properly, in which case the door does not fully close.
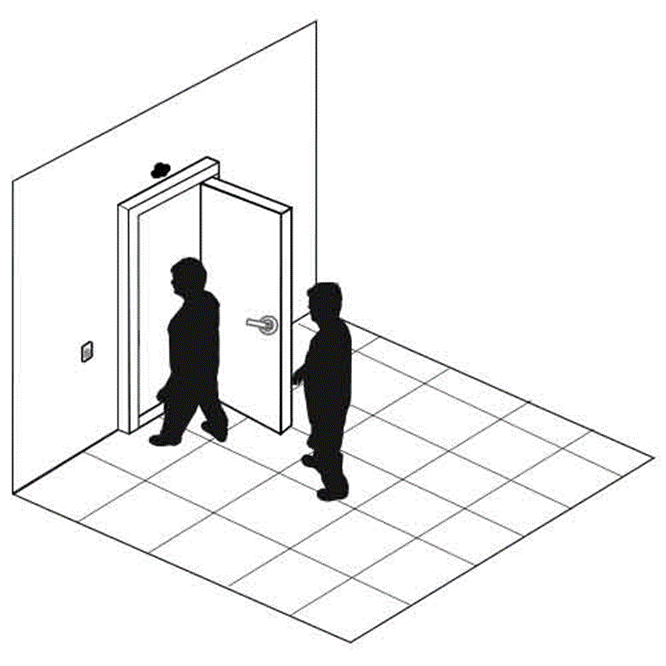
How to prevent
- Proper user education to enforce the use of access cards and prohibit tailgating. Users should know that not holding the door is not considered rude.
- Install a security guard at each entrance or monitor entrances with security cameras
- In more extreme cases, installation of man trap doors might be necessary. A man trap door allows only one person to enter at a time. The man trap door contains cameras with artificial intelligence to detect the number of people inside and permits entry to only one individual at a time.

Eliciting Information
Eliciting Information is a technique that an attacker can use to gather information covertly. The social engineer can obtain this information through casual conversation without alerting the victim. That is because people are stupid.
- People like to talk about themselves and show off. People like to complain about their jobs or brag about their achievements. If you give somebody attention, they will tell you many things about their job and work environment. For example, a security guard might complain that some of the cameras in his office don’t work.
- A person may give away sensitive information to a person who they are trying to impress. The secretary might show you where they keep the vault.
- You can deliberately give the victim some false statements about the information you are trying to gather, and they will correct you. You can also play dumb and they will teach you.
Whaling
Whaling is like Phishing, but targets high-value individuals such as celebrities, CEOs or other executives. Whaling is specifically targeted to the high-value individual. Whaling takes more effort to execute, but the response rate is higher, and the amount of money stolen from each user is higher. Many high-net worth individuals have access to credit cards with high limits.
Another scheme involves a scammer visiting a store such as Best Buy and attempting to illegally purchase expensive electronics (on credit) in the name of a celebrity. The scammer disappears with the electronics and the store is never paid. The store should have verified that the buyer legitimately represents the celebrity.
How do we prevent whaling?
- Proper user education
- 100% identity verification of the person who is seeking information.
- A high-net worth individual should understand that he is at much higher risk of exploitation either through fraud or extortion schemes. This person should employ people who specialize in detecting and preventing these threats.
Prepending
Prepending is adding something malicious to the beginning of what is assumed to be a safe file or application. When the application is run, both the safe item and the malicious item are executed.
Identity Fraud
Identity Fraud is an act of stealing an individual or corporation’s identity and using it to steal information, steal money, or destroy their reputation. It is common for a thief to use the identity of a dead person.
Examples of Identity Fraud
- Using another person’s driver’s license and/or social security number to borrow money from a bank and not paying it back.
- Using another person’s social security number to obtain a credit card, and then spending the money on the credit card and not paying it back.
- Using the identity of a corporation to obtain goods or services from another corporation, with no intention of paying for them.
Invoice Scams
An Invoice Scam is when a scammer sends your business an invoice for goods or services that you did not agree to purchase.
- The scammer sends you goods that you did not agree to buy. Then the scammer sends you a bill. The scammer tries to convince you that you or one of your coworkers agreed to purchase the goods. This is an easy scam when the business is large because the person paying the invoice might not know the person who is presumed to have purchased the supplies.
For example, the scammer sends you office supplies and tells you that “Bob Jones in Sales” ordered them. Bob Jones never agreed to buy the office supplies, but you feel intimidated or assume that somebody at your business ordered them and agree to pay the invoice.
Another example is when the vendor insists on placing your name in an industry “directory”. Sometimes, the vendor calls you to renew your subscription in having your business information placed in the directory, even though you did not sign up in the first place. - The scammer sends you an invoice for goods that were never purchased or received. Your accounting department pays the invoice thinking that it is legitimate.
For example, you receive an invoice from Bob’s Office Supplies, but Bob’s Office Supplies never sent you any goods and you never agreed to buy anything from them. - The scammer sends you an invoice but pretends to be a legitimate vendor.
For example, you buy office supplies from Staples. The scammer finds out (maybe by intercepting a real invoice) and sends you a fake invoice, which appears to be from Staples. The fake invoice has different payment instructions. You pay the invoice, but the payment goes to the scammer.
Some warning signs that the vendor is pulling a scam
- They try to offer you something for free and ask that you return the favor
- They ask you to buy something small or take a free sample, but in the fine print, you are agreeing to make a larger purchase
- They offer you something expensive that you can’t afford, and when you refuse, they show you something more affordable which appears reasonable in comparison with the original offer
- They use peer pressure. They tell you that all your competitors have made the same purchase. You don’t want to be left behind.
- They use flattery or complement you. They try to make you feel smart by making the purchase.
- They act with authority. They claim that they are an official supplier to the government.
- They make the offer seem like it is only available for a limited time or that there are limited quantities of the product available.
- They try to get you excited about the offer.
We can prevent these types of fraud by following this process
- There must be an approval process for purchasing
- The approval process starts by having a list of approved vendors
- Each vendor’s identity, qualifications, and payment details must be verified and recorded in the procurement system
- An employee making a purchase must obtain approval from a manager. Purchases of a large value must be approved by more than one manager
- We issue a Purchase Order to the vendor when we want to buy something
- When the goods are delivered, the vendor sends an invoice to our accounting department
- The accounting department verifies the following
- The invoice is from a legitimate vendor
- The invoice is in response to a valid Purchase Order
- The goods or services being billed for have been received
- The dollar amount on the invoice is the same as the dollar amount on the Purchase Order
- The payment details match those in the system
- The invoice is from a legitimate vendor
- A manager approves the invoice for payment
- The accounting department pays the invoice using the details in the system
- The entire process should be automated so that there are no ways to bypass the system and approve or pay for an invoice off the record
Credential Harvesting
Credential Harvesting is the process of stealing a large volume of usernames and passwords. It can be done through the use of malware, phishing scams, or hackers stealing credential databases.
We can prevent harvesting by
- Educating employees about phishing scams
- Securing systems to prevent malware infections
- Ensuring that databases containing credentials are secure and encrypted
- Storing passwords as salted hashes. A salted hash cannot be reversed to the original password.
- Forcing users to use multi-factor authentication so that a compromised password cannot be used to log in.
Reconnaissance
A Reconnaissance attack is when a hacker covertly gathers information about a system or organization. The hacker may sell this information or use it to orchestrate a future attack where information is stolen, or damage is done. The information may be about the computer system or about the physical building security.
The hacker might gather
- Information about the business or its processes
- Information about key employees and their habits
- The type of physical and digital security in place
- The type of security credentials in use
- The operating systems in use
- The makes and models of network and computer equipment in use
- The configuration of each piece of equipment
- Whether any equipment has unpatched vulnerabilities
We can prevent a reconnaissance attack by ensuring that our systems are patched and by teaching employees not to disclose information to outsiders. Key employees also need to be educated to detect when they are being followed or spied on. If your organization is large enough, you may need to assign security guards to members of your executive team.
Hoax
A hoax is a fake threat. A user might respond to the hoax in a way that weakens security. A hoax might take the form of a
- Death of an important person
- Impending attack/war
- Adverse weather/tornado
- Potential security threat
Impersonation
Impersonation is acting like another person. The thief will pretend to be a person known to the victim (or employed in a position known to the victim) and steal information from the victim through trickery.
Impersonation can occur via e-mail, telephone, or in person.
The type of impersonation
- IT help desk person (the thief acts like a member of the IT help desk and calls the victim asking for access to the computer or access to some information that the victim possesses)
- Manager/CEO (the thief acts like a member of senior management and uses their position of authority to obtain information)
- Co-Worker (the thief acts like a co-worker, and uses their friendship to obtain information)
- Government Official/Law Enforcement (the thief acts like a member of law enforcement and uses threats or intimidation to obtain information)
- Contractor/Janitor (the thief acts like a contractor and obtains unauthorized access to the building and then steals information)
The thief will normally have obtained information that the victim will know (information about a project, co-worker, manager, etc.). By name-dropping and information-dropping, the thief will appear legitimate to the victim.
How to prevent
- Proper user education.
- Ensure that a user verifies the ID of each person they interact with (if not known personally) before providing any information. The company should foster a culture where verifying the identity of another employee (even that of a senior manager) is encouraged and not considered rude.
- 100% identification verification of each contractor requiring access to the building or to the customer’s system.
Watering Hole Attack
In a watering hole attack, a thief plants a form of malware on a frequently visited website. The users visit the website and download the malware.
A watering hole attack typically takes advantage of a zero-day exploit. It allows malware to download in the background without any indication to the user.
How to prevent
- Proper antivirus can prevent many watering hole attacks
- Website operators should ensure that their servers and code are up to date
- Watering hole attacks that take advantage of zero-day exploits cannot be prevented
Typosquatting
There are many forms of hijacking, where a hacker takes over a user’s experience after he has logged in. Hijacking can be simple or complicated. Hijacking attempts include
- Clickjacking. In clickjacking, a user visits a website and clicks on something different from what he expected. A hacker could inject code to create transparent overlays on a website. Or a hacker could modify the code.
- One popular clickjacking method involves advertisements.
Many website owners’ partner with Google AdSense. Google AdSense provides each owner with a code containing their account number. The website owner places the code in any spot where they would like advertising to appear. When the website loads, the code queries Google’s servers and inserts an advertisement. Google handles all advertising sales. When visitors click on the ads, revenue is generated (Google and the website owner split the revenue).
A hacker can sign up for Google AdSense and swap the website owner’s code with their own code. This does not happen at the server level, but instead at the web browser level (the user’s computer is infected with malware that detects AdSense advertisements and swaps the code). When the user clicks on the advertisement, the hacker’s AdSense account is credited, and the website owner is deprived of the revenue without ever realizing it.
- One popular clickjacking method involves advertisements.
- Session Hijacking. In a session hijacking, the user has an existing TCP/IP session with a server. The hacker hijacks the session and continues to communicate with the server (pretending to be the user).
- URL Hijacking. In a URL hijacking, the hacker edits a browser URL. The original domain name might stay the same, but the hacker could modify a portion of the URL after the domain.
- For example, the hacker could modify the URL to redirect the victim to a different website or to execute a script on the existing website.
- For example, the hacker could modify the URL to redirect the victim to a different website or to execute a script on the existing website.
- Typo Squatting. In Typo Squatting, a hacker purchases domain names that are like popular domain names.
- For example, the hacker purchases gooogle.com (which is similar to google.com). The hacker points gooogle.com to their own server, where they serve malicious content (advertisements, viruses, phishing scams, etc.) A visitor who accidentally types in gooogle.com visits the wrong website and his computer is infected or he is tricked into giving up sensitive information.
How to prevent
- Brand owners can register domain names that are common misspellings of their own names. Brand owners with trademarks can litigate against hackers who are typo squatting against their names without any legitimate purpose.
- Users should verify carefully that they are entering in the correct URLs and that no malicious content has been added.
The Anticybersquatting Consumer Protection Act prohibits the registration of a domain name that is a trademark (or confusingly similar to a trademark) if the registration was made in bad faith. A person injured by the registration may bring action in federal court.
15 USC § 8131 prohibits the registration of a domain name that is a person’s name without that person’s consent, if the registration was made for profit.
The act does not prohibit freedom of speech; thus, a user may register a domain name that is critical of an organization or brand that includes that organization’s trademark.
Truth in Domain Names Act makes it a federal crime to register a domain if the domain is used to trick visitors into viewing obscenities. John Zuccarini was the first person charged under the act.
Pretexting
Pretexting is an idea in social engineering where the attacker creates a scenario that convinces the victim to trust him or to divulge information. Sometimes, the pretext causes the victim to contact the attacker first.
Principles (Reasons for Effectiveness)
Why do social engineering attempts work? There are many reasons.
- Authority
- The person on the other end of the phone call/in person acts with authority. People are afraid to challenge those who appear to be in a position of authority (such as members of senior management).
- Authority can be established by confidence, tone of voice, clothing, and/or uniforms.
- People are afraid to challenge authority because of perceived negative consequences (getting fired)
- The consequences do not have to be explicitly stated by the thief. They can be implied, or the user might simply assume what they are based on the alleged authority.
- Social engineering authority attacks can be prevented by enforcing policy against all users, regardless of their position. The company must create a culture where verifying the identity of another person is encouraged, regardless of that person’s position.
- For example, the thief could pretend to be a member of senior management and convince the victim that she could lose her job if she does not comply. The thief could demand that the victim provide him with corporate financial information, or wire money to a third party.
- The person on the other end of the phone call/in person acts with authority. People are afraid to challenge those who appear to be in a position of authority (such as members of senior management).
- Intimidation
- Intimidation uses the threat or idea of negative consequences if the person fails to comply.
- The thief does not have to make any direct threats, but instead may cause the victim to believe that negative consequences will occur (or the victim may assume that negative consequences will occur if they fail to comply).
- For example, the thief could pretend to be a police officer and convince the victim that she will be arrested if she does not comply. The thief demands that the victim disclose sensitive data relevant to an investigation.
- Intimidation uses the threat or idea of negative consequences if the person fails to comply.
- Consensus
- Consensus involves a group-decision.
- If a social engineer is unable to convince a specific person to perform an action, he could attempt to convince others in that person’s social circle. Those other people could convince the victim to proceed.
- For example, the thief could convince the victim that her co-workers completed the same action.
- Consensus involves a group-decision.
- Scarcity
- Scarcity means that something is unavailable or in limited supply.
- If the victim values something that is scarce, they may forgo normal procedures and fall into the trap to obtain that item.
- For example, the victim wants a rare (sold out) toy at Christmas time. The thief convinces her that he can supply the toy if she provides him with her credit card/banking information (which he uses fraudulently). The victim never receives the toy.
- Scarcity means that something is unavailable or in limited supply.
- Familiarity
- The victim feels familiar with the situation and proceeds because nothing seems out of place.
- The thief can convince the victim to focus on ideas that are familiar, by dropping names, projects, or other tasks into the conversation.
- Although the victim does not know the thief, she is led to believe that he is a legitimate co-worker.
- The victim feels familiar with the situation and proceeds because nothing seems out of place.
- Trust
- The victim trusts the thief and proceeds with their own free will.
- The victim believes that the person they are talking to or the site that they have visited is legitimate.
- The thief may take time to build this trust, especially with a high-value target. The greater the victim trusts the thief, the more the victim will be willing to do.
- The victim trusts the thief and proceeds with their own free will.
- Urgency
- Urgency is like scarcity
- Urgency builds on the idea that there is a limited time to act.
- People hate losing money more than they hate not making money.
- For example, the victim could be told that money is about to be withdrawn from their bank account and they only have a few minutes to stop it (by providing their banking information to the thief). Normally, the victim would take their time to check that the person they are speaking with is legitimate but bypasses these risk controls because of the urgency.
- Urgency is like scarcity
Laws Relevant to Social Engineering
As mentioned previously, the Computer Fraud and Abuse Act applies to most forms of unauthorized access to a computer system.
In the cases of fraud over the telephone, in person, or over a computer (e-mail, social media, text, etc.), 18 USC § 1343 – Wire Fraud – applies. Note the three conditions that the Defendant must have
- Obtained money or something of value
- Done so by false or fraudulent pretences
- Used the ‘wires’ in a way that affected interstate or foreign commerce
State laws of fraud, larceny, or theft may apply when interstate or foreign commerce is not affected. But most fraudulent schemes occur over the internet and/or on a large scale, making the federal law apply.
