2.6 Explain the security implications of embedded and specialized systems
- Embedded Systems
- Raspberry Pi
- Field-Programmable Gate Array (FPGA)
- Arduino
- Supervisory Control and Data Acquisition (SCADA) / Industrial Control System (ICS)
- Facilities
- Industrial
- Manufacturing
- Energy
- Logistics
- Internet of Things (IoT)
- Sensors
- Smart Devices
- Wearables
- Facility Automation
- Weak Defaults
- Specialized
- Medical Systems
- Vehicles
- Aircraft
- Smart Meters
- Voice Over IP (VoIP)
- Heating, Ventilation, Air Conditioning (HVAC)
- Drones
- Multifunction Printer (MFP)
- Real-Time Operating Systems (RTOS)
- Surveillance Systems
- System on Chip (SoC)
- Communication Considerations
- 5G
- Narrow-Band
- Baseband Radio
- Subscriber Identity Module (SIM) Cards
- Zigbee
- Constraints
- Power
- Compute
- Network
- Crypto
- Inability to Patch
- Authentication
- Range
- Cost
- Implied Trust
Embedded Systems
An embedded system is a computer that is inside a larger device. Embedded systems are installed inside consumer electronics and inside critical systems such as medical equipment and control units for nuclear power plants. Many of these systems are vulnerable for the following reasons
- They represent a high value target for hackers (a hacker could exploit a vulnerability in a nuclear power plant and hold it ransom, or a hacker could discover a security hole in a popular consumer electronic and hijack thousands, or millions of devices).
- Embedded systems are targets for nation state actors, who have virtually unlimited resources, access to zero-day exploits, and access to experienced hackers. Disruption to an embedded system can be done for political purposes.
- An embedded system may be in a remote area and its firmware cannot be readily updated. Some device manufacturers do not include a mechanism for updating firmware, either as planned obsolescence, to reduce costs, or to prevent end users from modifying their equipment.
Some popular systems
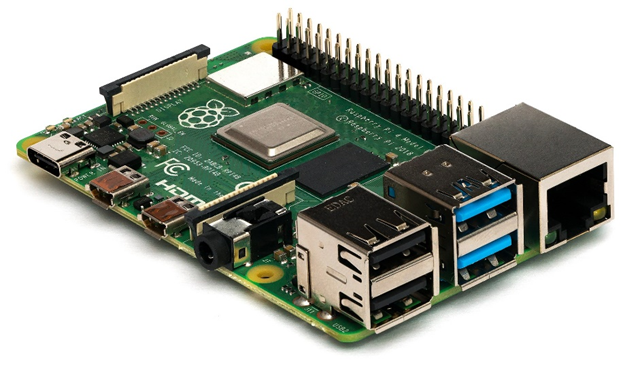
- Raspberry Pi. The Raspberry Pi is a small computer that can be integrated into commercial applications. It costs less than $50.
- Features
- Up to 8 GB of RAM
- Ethernet Port
- Wi-Fi
- USB ports
- No hard drive. We can store the operating system on an SD card. We can also connect a USB drive for additional storage.
- Up to 8 GB of RAM
- There are 30 pins on the right side of the system board. We can connect input and output devices to each pin.
- For example, we can connect an input like a thermostat and an output like a control for a heater. Then we can program the Raspberry Pi to monitor the thermostat signal and tell the heater to raise the temperature when things get cold.
- We must teach the Raspberry Pi to interpret the signal from the thermostat. The thermostat signal is usually a constant voltage with a different amperage to signal a change.
- We must also teach the Raspberry Pi to provide an output signal that the controller can understand.
- Features
- Field-Programmable Gate Array (FPGA). An FPGA is a microchip that can be soldered onto a printed circuit board. The chip receives inputs and using the programmed logic inside it, produces an output. The chip receives power from the circuit board.
Below is a circuit board, and the grey rectangular objects are FPGAs. To program an FPGA, we must connect wires directly to the device or to the printed circuit board.

- Arduino. An Arduino is similar to a Raspberry Pi but it is less powerful. It contains inputs and outputs for different devices. We must program the Arduino via a programming language and compile it. We connect to the Arduino via a USB or serial port and upload the application that is required.

Supervisory Control and Data Acquisition (SCADA) / Industrial Control System (ICS)
SCADA stands for Supervisory Control and Data Acquisition while ICS stands for Industrial Control System. These systems are found at power plants, factories, utilities, and other critical forms of infrastructure.
An ICS is designed to operate reliably 24 hours per day, 7 days per week for many years, without interruption. Multiple ICSs can be combined to operate redundantly. An ICS may consist of many PLCs – Programmable Logic Controllers. A PLC is a special type of industrial computer that collects input from sensors, uses an algorithm to make decisions, and send an output to different control units.
For example, a PLC could be connected to a water pump that is filling a tank with water, and a sensor that is monitoring the tank’s water level. The PLC continuously monitors the tank’s water level. When the tank is empty, the PLC directs the pump to pump water, and when the tank is full, the PLC directs the tank to turn off.
Multiple ICSs can be connected to a SCADA system. The SCADA system collects data regarding a process. For example, the SCADA system can collect data from an oil refinery to determine the quantity of crude oil being turned into gasoline and can collect data from thousands of steps along that process. This data is typically sent to a control room where operators can analyse the data and detect discrepancies.
The different components of the SCADA system can be housed close together or may be far apart. SCADA system components may communicate over a standard IP network via copper or fiber links.
Ideally, a SCADA system should be air gapped and isolated from any commercial network. This is not always possible because a SCADA system may control facilities that are physically separated by hundreds of kilometers. For example,
- SCADA system that controls the traffic lights in a major metropolitan city
- SCADA system that controls the power grid in the North Western United States
- SCADA system that monitors multiple oil refineries in a state
The SCADA system’s communications should be
- Securely encrypted
- Air gapped and isolated from any commercial network, where possible
- On a dedicated WAN connection where air gapping is not possible due to distances
Yet there are many SCADA systems in use today that are accessible remotely (due to the negligence of the installer or manufacturer), some without a password. It is possible to locate these systems simply by running a port/IP scan.
SCADA should be physically isolated from the commercial network. For example, a nuclear plant should not allow any part of the SCADA network to interact with the plant’s commercial network.
SCADA systems should not communicate wirelessly unless necessary, and where extreme precautions have been taken to ensure that all data is encrypted.
Many components inside the SCADA system may communicate without encryption. An air-gapped SCADA network can be easily disrupted if a malicious user has physical access to any SCADA network equipment or wiring. A malicious individual could splice the wiring between two SCADA system components and
- Disrupt the communication. For example, a conveyor belt is being used to load a truck with fertilizer. A hacker could cut the wire between the PLC and the conveyor belt motor, in which case no trucks could be filled. This behavior would disrupt operations.
- Spy on the communication. For example, a hacker could spy on the content of the communication to determine the quantity of oil being refined; the hacker could use this data to predict oil prices on the open market and place trades.
- Substitute inaccurate data inside the communication. For example, SCADA systems are used to control traffic lights in many major cities. These systems connect over unencrypted wireless systems or analog telephone lines. A hacker could disrupt the traffic patterns and bring intersections to a halt.
According to NIST Guidelines for SCADA Systems (NIST Special Publication 800-82), good SCADA security should
- Restrict logical access to an ICS network (using firewalls, multiple network layers, a DMZ, and unidirectional gateways)
- Restrict physical access to an ICS network
- Protect ICS from exploitation (install and test patches when available, disable unused ports and services, restrict user privileges to only those that need it, monitor and audit use of the system, check for file integrity)
- Restrict modification of data
- Detect security incidents (detect security events before they become incidents, detect failed ICS components and overloaded resources)
- Maintain functionality during adverse conditions (ensure that there is no single point of failure, that critical components have redundant counterparts, that the failure of a specific component does not create additional traffic or cascading effects, that if the system is to operate in a degraded state it does so gracefully)
- Restore the system after an incident (organization should have an incident response plan which includes key roles for all individuals involved, a well documented system, back up of all configuration, readily available replacement parts, and support from manufacturers and vendors)
An example of a virus that affects SCADA systems is Stuxnet. The Stuxnet virus
- Infected computers and hid its presence through a root kit
- Infected the firmware on USB drives inserted on those computers (the firmware on a USB drive does not contain any user storage and is typically inaccessible by any form of operating system or antivirus program)
- Searched for and infected any computer running the Siemens Step7 software application (which controls PLCs)
- Once a PLC is located, it modified the code on the PLC so that it would cause damage, but returned normal values to the computer (so that the operator was unaware as to the harm that was being caused)
Smart Devices/IoT
Smart Devices include the Apple Watch and the Nest thermostat. The harm resulting from a single smart device’s exploitation is small, but since the most popular devices have millions of units deployed, a hacker could exploit many of them.
Recently, the smart devices have been exploited to launch botnets.
The main reason smart devices can be exploited is because they come with weak default settings (a username and password that are easily guessed) and end users do not or cannot change them.
Smart Devices are found in the following areas
- Sensors – Devices like thermostats, motion sensors, and intrusion alarms.
- Smart Devices – Devices like smart locks and refrigerators
- Wearables – Devices like the Apple Watch or Google Glass
- Facility Automation – Devices that monitor building systems like air quality
Harm to a special purpose device such as a medical device, a vehicle, or an aircraft can cause loss of life. It is important to keep these devices physically isolated from the network.
This is not always possible because
As of 2008, all vehicles must contain a device known as a CAN bus. The CAN bus allows the different vehicle computer systems to talk to each other. Now that the vehicle can talk to an external server, it can be hacked. Hackers have demonstrated that they can hijack vehicles remotely and cause them to accelerate.
In the past, a utility company would send a person to your house each month to read the meter. Now they can use a Smart Meter. The Smart Meter is connected to your internet, or to a cellular network. It automatically provides the utility with the reading so that they don’t have to send somebody to your house. A smart meter can be hacked. Since it connects back to the utility’s network, if you can gain access to the smart meter, you might be able to gain access to the utility’s network.
Hackers have also demonstrated that the in-flight entertainment systems on airplanes are connected to the aircraft cockpit systems, and only separated by a firewall instead of a physical network. That means it might be possible for a passenger to hijack an airplane through the inflight entertainment system.
Camera Systems
A Camera System is important for physical security. Cameras in sensitive places can be hijacked. It is important that
- Each camera is physically secure so that it cannot be removed or manipulated
- The connection between the camera and its monitoring station is encrypted
- The camera software is secured. Cameras connected to the internet can be exploited by botnets.
Voice Over IP (VoIP)
More people are switching to VoIP for their telecommunications needs. That means that their voice calls are transmitted over the internet. Disruption to a VoIP network is bad because people won’t be able to communicate or place emergency calls. Even if a hacker does not directly disrupt the VoIP network, they can cause disruptions over the internet in general, which can affect the quality of the VoIP calls.
Heating, Ventilation, Air Conditioning (HVAC)
HVAC stands for Heating, Ventilation, and Air Conditioning. HVAC systems can be connected to computerized controls, which can be connected to the internet for several reasons
- Allows multiple buildings to be monitored at the same time
- Allow configuration changes to be made remotely
In 2013, Target stores was hacked when an HVAC contractor’s credentials were compromised. Specifically,
- Target posted detailed information about its network architecture on its own vendor portal and allowed Microsoft to publish detailed case studies with the same information
- Target uses a vendor management application known as SAP Ariba
- SAP Ariba is connected to other Target computer systems
- In particular, it is connected to Active Directory and Single Sign On
- A user with access to SAP might have access to other Target systems
- SAP Ariba is connected to other Target computer systems
- The hacker sent a phishing e-mail to Fazio Mechanical, one of Target’s HVAC contractors
- The hacker installed Zeus malware (a keylogger) on Fazio’s computers and waited until it detected Fazio’s login credentials (which provided access to Target’s systems)
- Fazio did not use an antivirus program or may have used the free version of Malwarebytes. In any event, the antimalware application did not detect the Zeus malware.
- The hackers used Fazio’s login credentials to gain access to SAP Ariba, and then used their SAP Ariba access to gain access deeper into Target’s network
- The hackers deployed malware known as Trojan.POSRAM which infected Target’s point of sale systems
- The malware scraped the RAM of each point of sale system, looking for credit card data
- The malware sent the data to a compromised server on Target’s internal network (since a point of sale system is unable to directly access the internet)
- The malware scraped the RAM of each point of sale system, looking for credit card data
- The hackers then copied the stolen credit card data from the internal server to an external server
- After the data breach, Target agreed to
- Improve monitoring and logging of system activity
- Improve firewall rules and policies
- Limit or disable vendor access to their network
- Reduce privileges on over 445,000 Target personnel and contractor accounts
- Expand the use of two-factor authentication
- Improve monitoring and logging of system activity
- This attack was fully preventable
- Fazio did not have good anti-malware software
- Target’s POS did not have good anti-malware software
- Target provided its contractors with logins that did not include two-factor authentication
- Target provided its contractors with access to systems that they did not require
- Fazio did not have good anti-malware software
Drones
Drones are used by private companies and by the military. The use of drones is regulated by most countries. Drones used for commercial and personal use must have an operator who can always see the drone. Drones used for military purposes may be controlled by people thousands of miles away.
The question is
- Can the communication between the drone and the controller be intercepted?
- Can the hacker create enough radio noise that the drone stops communicating with the controller?
- If the drone is being controlled over the internet, can the hacker intercept or disrupt that communication?
Multifunction Printer (MFP)
MFPs are a common source of exploitation. One reason is that Wi-Fi Direct technology allows you to connect directly to a printer, and this technology is usually weakly implemented. Hackers connect to printers to steal documents that have already been printed but not erased from memory.
Real-Time Operating Systems (RTOS)
An RTOS, or Real-Time Operating System is one that processes data in real time. Devices that run RTOS’s include PLCs and other devices that could not afford to fail.
An RTOS must not have any memory leaks. It must be able to run forever without a reboot. The RTOS can also fail if something interferes with its ability to deliver a response in real time. Therefore, an RTOS must operate at the highest levels of security.
System on Chip (SoC)
An SoC is a system on a chip. A system on a chip is a complete set of components – processor, memory, storage – integrated into one unit.
SoCs can be found in many types of devices such as medical devices. The use of a SoC can be risky, but sometimes an organization has no choice.
- The software on a SoC cannot be modified.
- It is difficult or impossible to determine how the SoC works because the circuitry and software is proprietary. The SoC will not accept monitoring or an antivirus program.
- It might be impossible to determine if a SoC that has been exploited by a hacker
- If the SoC operates a critical device such as a medical monitor, an MRI, or an ultrasound machine, deactivating the device may be impossible. It may take months to find a suitable replacement.
Communication Considerations
- Cellular. Many systems deployed in the field use the cellular network to communicate. That means that the device must contain a cellular modem and a SIM card. The current version is 5G but some devices may use 4G or 3G. We have to pay for the use of the cellular network. It might not be cost effective to purchase a cellular subscription for each device.
- Narrow-Band. A Narrow-Band is a radio network that can transmit data over a long distance. We might use the Narrow-Band if we want to set up our own monitoring station instead of using the cellular network.
- Baseband. Baseband refers to other types of communication including Ethernet and Wi-Fi. IoT devices can use baseband when they are deployed in an environment where such a network is in place.
- Zigbee. Zigbee is a communication protocol that is used by many residential-grade IoT devices such as smart thermostats. Typically, one device acts as a gateway – it connects the Zigbee devices to the ethernet network. The rest of the Zigbee devices create a self-forming, self-healing mesh that allow all of them to reach the gateway, even if some are far.
Constraints
Let’s review why embedded systems are difficult to work with
- Power. The embedded system is one that must consume minimal power. The system might be installed somewhere that does not have power, in which case it must run on batteries. Or it might be taking power from the device that it is embedded in.
- Compute. The device will have a processor of limited capacity. When we mass produce embedded devices, we want to keep the cost as low as possible. That means that we need to minimize the resources contained in each device. We don’t need a powerful processor or lots of RAM for a thermostat that is only measuring the temperature.
- Network. The device may be limited in terms of whether or how it can connect to a network.
- Crypto. The embedded system might not use any encryption algorithm to store or transport data. That means it is easy to hack.
- Inability to Patch. Many embedded systems do not accept firmware updates. There might not be a way to connect to the system and update it.
- Authentication. The device may not have any security that prevents unauthorized users from gaining access and modifying the firmware or settings. The device may have no password, or a default password that can’t be changed.
- Range. The device may have a limited range of communication.
- Cost. The cost of the system must be low.
- Implied Trust. People just trust embedded systems. They just assume that the device is safe and that it can’t be hacked. It’s not something that people usually think about.
How to prevent our embedded systems from being hacked
- Thoroughly research the manufacturer’s reputation and expertise before purchasing any equipment
- Attempt to locate products that use open source firmware and that can be updated
- Develop a mitigation strategy such as a stockpile of replacement products from another vendor
- Change the default settings on each device
