4.1 Given a scenario, use the appropriate tool to assess organizational security
- Network Reconnaissance and Discovery
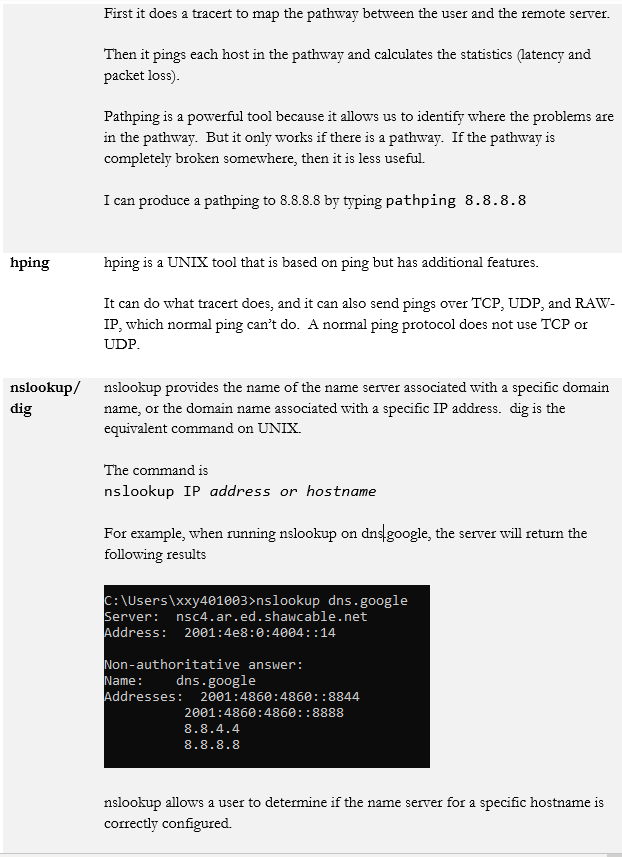
- tracert/traceroute
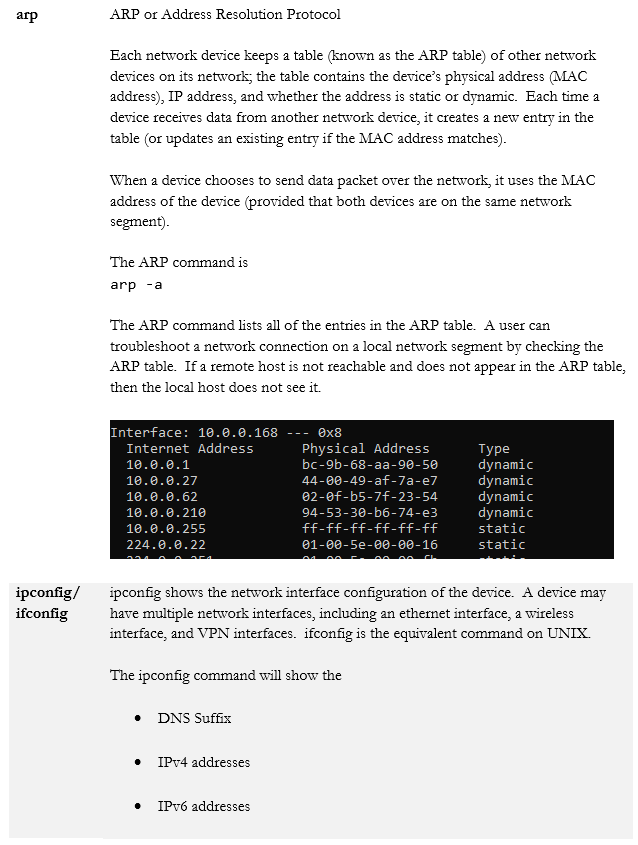
- nslookup/dig
- ipconfig/ifconfig
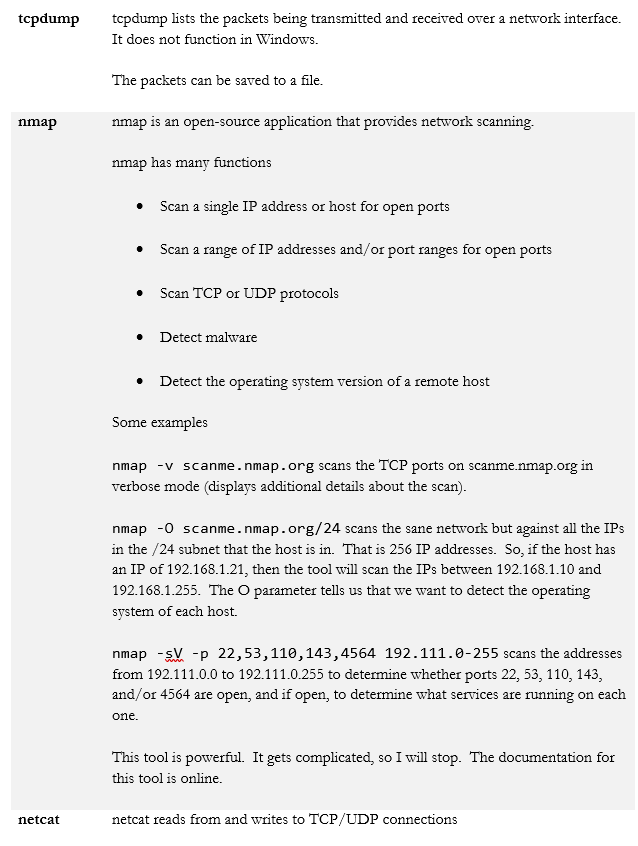
- nmap
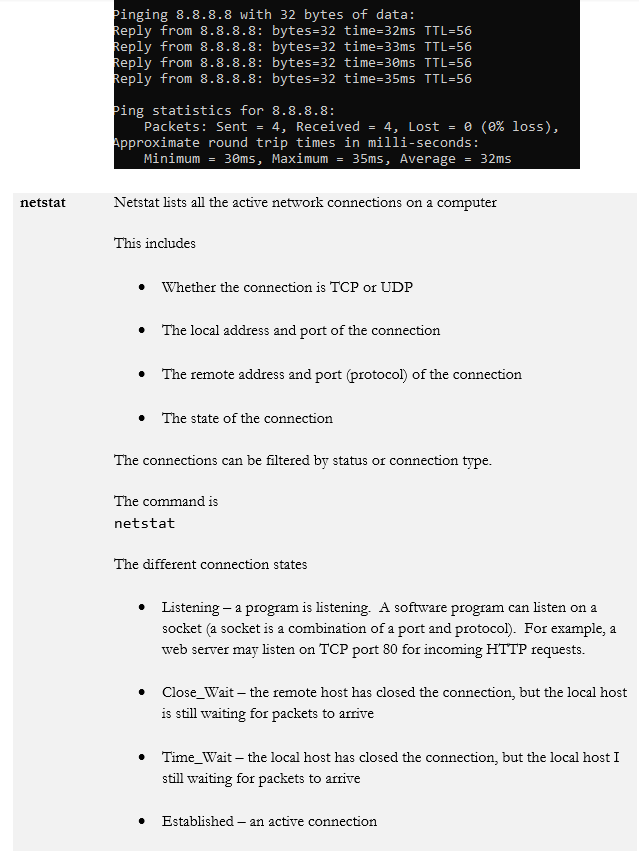
- ping/pathping
- hping
- netstat
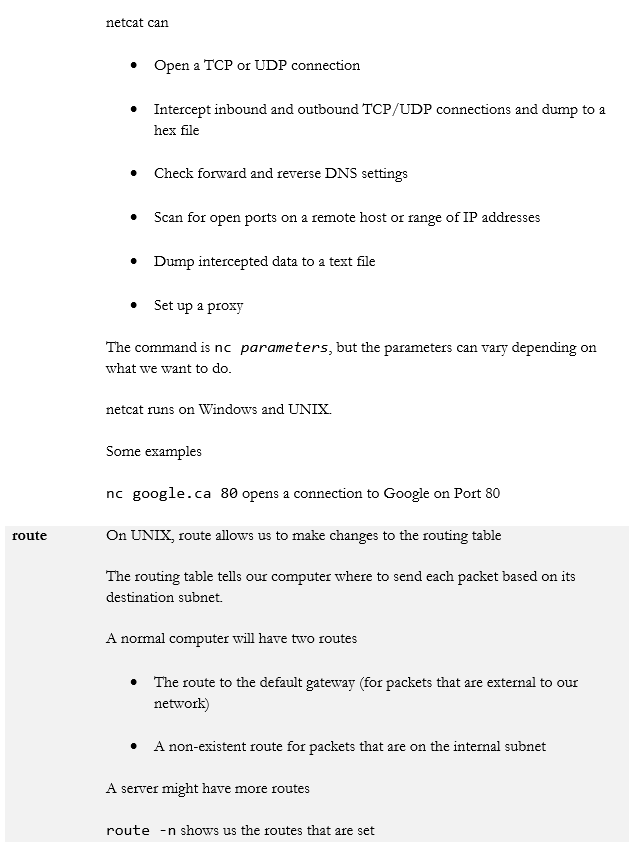
- netcat
- IP Scanners
- arp
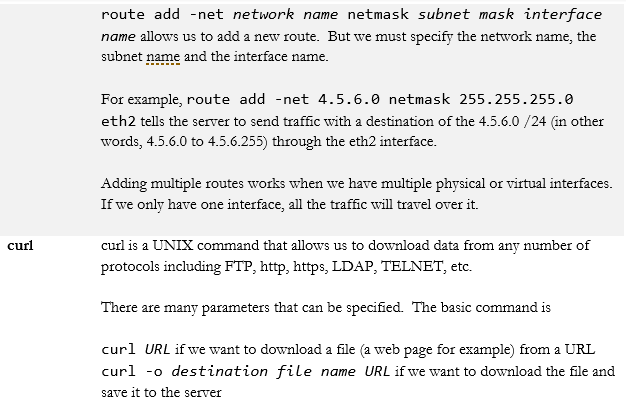
- route
- curl
- theHarvester
- sniper
- scanless
- dnsenum
- Nessus
- Cuckoo
- File Manipulation
- head
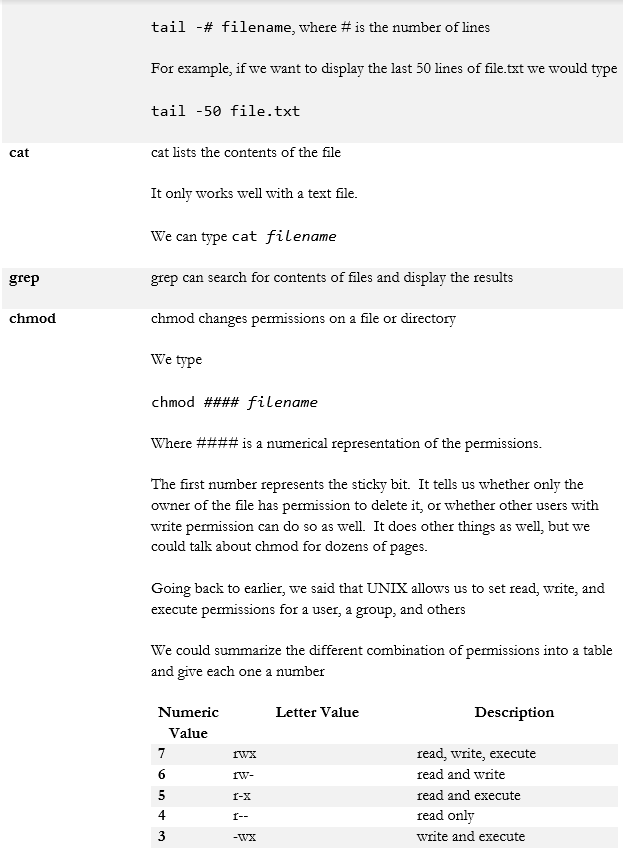
- tail
- cat
- grep
- chmod
- logger
- Shell and Script Environments
- SSH
- PowerShell
- Python
- OpenSSL
- Packet Capture and Replay
- Tcpreplay
- Tcpdump
- Wireshark
- Forensics
- dd
- Memdump
- WinHex
- FTK Imager
- Autopsy
- Exploitation Frameworks
- Password Crackers
- Data Sanitization
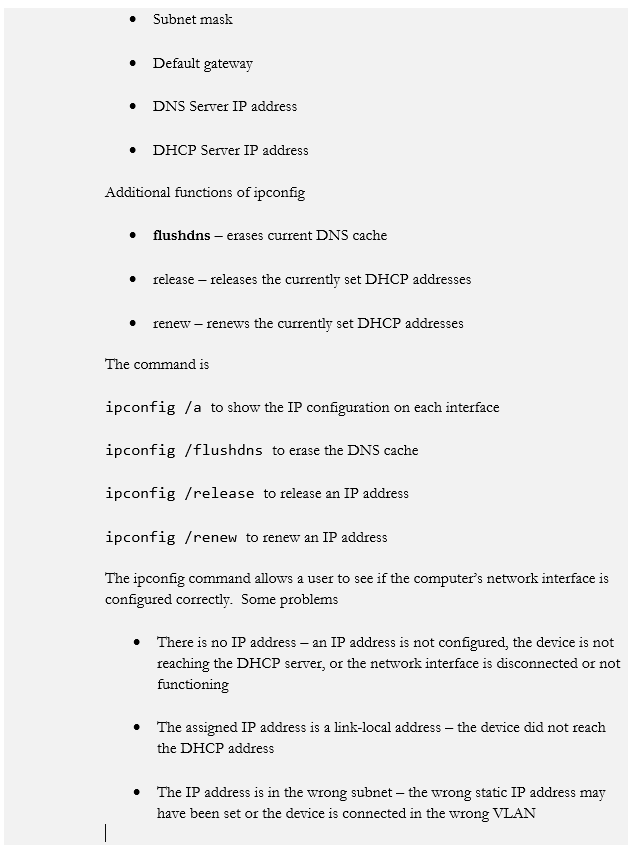
Network Reconnaissance and Discovery
We’ve gone over the different security threats, architecture, and methods for keeping our network secure. We hope that no bad things will happen, but they will. So now we need to identify some tools for responding.
We will start with some basic commands that are already in your computer. Some of these commands assume that you understand basic networking and subnet masks.

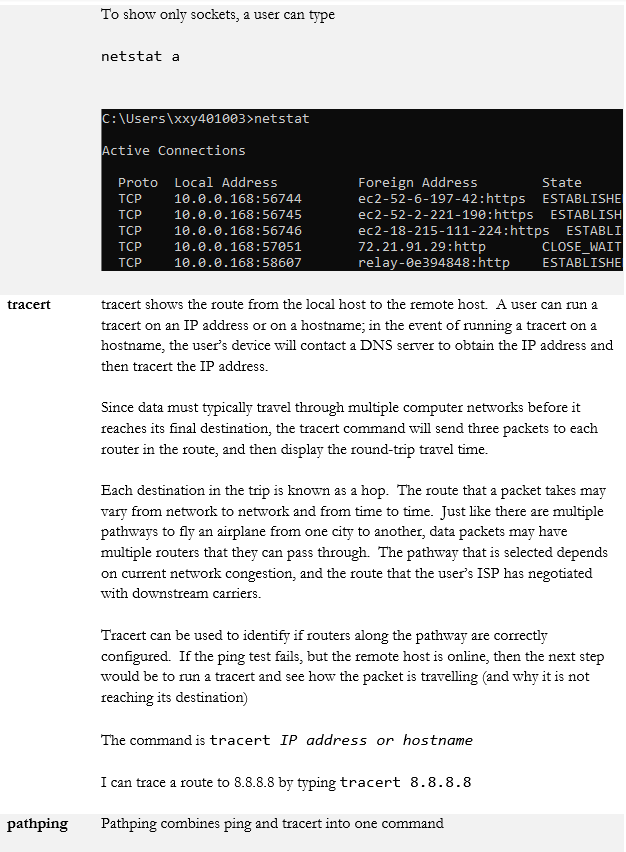
Some people have developed additional tools to help with scanning networks
- IP Scanners. An IP Scanner can be a command line tool or a GUI tool that searches an IP address or a range of IP addresses for open ports. For each device, it can tell us
- The open ports on the device
- The IP address and MAC address of the device
- The device’s operating system
- The hostname
- The open ports on the device
Angry IP Scanner is a free, open-source GUI scanner.
- theHarvester. theHarvester is a tool that can scan open source data sources for e-mail addresses, employee information, usernames, and passwords. We can use it when conducting a passive reconnaissance in a penetration test. We can also use it to see what kinds of data about our organization is out there.
- Sn1per. Sn1per is another automated tool that can scan a target for vulnerabilities. It combines many other open-source tools such as amap, arachni, amap, cisco-torch, dnsenum, enum4linux, golismero, hydra, metasploit framework, nbtscan, nmap smtp-user-enum, sqlmap, sslscan, theHarvester, w3af, wapiti, whatweb, whois, nikto, and wpscan.d.
It is powerful because it can- Check for basic data such as whois and ping
- Check for open ports
- Brute force DNS information
- Check for subdomains of a website
- Detect and analyse a web application firewall
- Check for SSL vulnerabilities
- Check for compromised web applications
- Automatically brute force any service running on the target host
- Check for basic data such as whois and ping
- Scanless. An open-source Python script that can perform a port scan via different online scanners.
- Dnsenum. An open-source Perl script that can gather DNS information about a domain name. This includes
- Available DNS information (A records, MX records, etc.)
- Identify subdomain names from Google
- Calculate the subnet width of the IP address linked to the domain name and then run a reverse lookup on the entire IP subnet to see what other domain names are present.
- Available DNS information (A records, MX records, etc.)
- Nessus. Nessus is a paid program that runs vulnerability assessments on a network. It contains a database of regularly-updated vulnerabilities. We can install it on a local server or in the cloud. As of the time of writing, the database contains over 66,000 common vulnerabilities. It also contains over 166,000 plugins.
- Cuckoo. Cuckoo Sandbox is an open source program that can analyse malware. Some of the things that it can do
- Automatically analyse a malicious file and determine whether it contains malware (and what type of malware)
- Determine whether an API call is legitimate
- Analyse network traffic
- Analyse volatile memory of an infected virtual system
- Automatically analyse a malicious file and determine whether it contains malware (and what type of malware)
Since it is open source, we can modify it to fit our needs.
File Manipulation
We also have some file manipulation tools that are part of UNIX.



Shell and Script Environments
- SSH. Secure Socket Shell (or Secure Shell) allows a user to connect to a remote computer. SSH authenticates the identity of the remote computer to the user and the user to the remote computer.
SSH creates a tunnel between the user and the remote computer. The user will require an SSH client such as PuTTY, and the remote computer will require an SSH daemon.
Each remote computer must be set up to accept SSH logins (typically over port 22). Network firewalls must be configured to allow traffic over port 22. The user’s IP address should be whitelisted on the firewall (do not allow SSH connections from any IP address).
Once logged in, we can use SSH to run different commands just as if we were physically logged in to the computer. Most UNIX operating systems run on the command line by default. - PowerShell. PowerShell was developed by Microsoft to allow an administrator to program common tasks. A PowerShell script can do almost anything that an administrator can do when logged in to a Windows computer, including creating user accounts and installing applications.
We can also use PowerShell to log in and make changes to a remote server or Microsoft Azure and Azure Active Directory. - Python. Python is a programming language that can run on any operating system – including Windows, Mac, and UNIX. Python scripts can provision servers, install applications, create user accounts and perform other administrative functions. An operating system will not recognize a Python script unless the Python software is first installed.
- OpenSSL. OpenSSL is an open-source library for implementing SSL on a web server. It allows us to do so without much code because the encryption and decryption functions are already written into the library.
Packet Capture and Replay
- Tcpreplay. Tcpreplay is a set of tools for replaying and analysing network data that has been previously captured.
If we are monitoring a network connection, we can record all the traffic as individual packets. Then we can replay them (run them back over the network) to see how a NIDS or NIPS would react. We can replay them at full speed or slowly. - Tcpdump. Tcpdump is a tool for capturing and saving network traffic. It runs on the command line. There are many possibilities. We can capture all traffic on an interface, or we can isolate traffic by port, protocol, network, or IP address. We can find traffic based on the hostname, cookie contents, http contents, DNS, or FTP.
- Wireshark. Wireshark is a free tool that can capture and analyse network traffic in real time. It can inspect and filter traffic from hundreds of protocols. It can also decrypt many protocols. The data can be saved for further analysis.
To make wireshark work well, we need to install it on a computer that is connected to a mirrored switch port or a tap. If we are capturing wireless data, then we need a wireless adapter that is set to promiscuous mode.
Forensics Tools
We will discuss forensics practices in a later section, but there are some tools that we need to have. One of the most important tools gives us the ability to create an image. An image is a digital copy of the data a physical device such as a hard disk drive.
- dd was one of the oldest forensics tools created. It ran on UNIX. It allows you to make an image of a physical device from a command line. It isn’t very good, but some advanced versions have been created.
- memdump allows us to dump the contents of the computer’s memory into a file. We can dump the entire contents or the contents associated with a specific process. We can take the dump file and analyse it later, but now we have a permanent record of volatile memory.
- WinHex is a tool that allows us to view the contents of a file in hexadecimal format. It lets us view the actual 0’s and 1’s of a file. Why is this good? Two common scenarios
- A suspect deletes a file. When you delete a file, the computer deletes the corresponding entry from the file allocation table, and the space where the file was is marked as being “free space”. The actual file is still there until a new file is created and the space is required. Then the old file contents are overwritten. Sometimes only parts of the file are overwritten.
It’s like if you have an index of books in a library. We can delete the book from the index, but the book is still on the shelf until somebody needs the space and replaces it with a new book.
If we made an image of an entire hard disk drive, we are reading all the 0’s and 1’s from it directly. If we open the image in WinHex, we can view the raw data, including the deleted data.
WinHex also shows us the hexadecimal translation of those 0’s and 1’s. Remember that 0’s and 1’s can be converted into actual letters and numbers. This allows us to review deleted content and fragments of deleted content.
There are tools that specifically scan for deleted files, but they are not always great at finding fragments, especially when a large portion is lost.
- Many programs (especially phones) store data in databases. A database stores its data in a file (or multiple files). For example, your iPhone stores text messages in a database file. When you delete a text message, your iPhone doesn’t automatically delete the message. Instead, it marks the message for deletion.
When the database gets too big, the database runs a tool to erase the content marked for deletion. Sometimes, the database overwrites messages marked for deletion, and we are left with fragments of messages. We can open the database in WinHex and view the fragments. - WinHex is powerful and supports
- Editing content on a disk directly
- Various file systems including FAT 16, FAT 32, NTFS, CDFS
- RAID
- Editing contents of RAM directly
- Ability to search binary and HEX for key words
- A suspect deletes a file. When you delete a file, the computer deletes the corresponding entry from the file allocation table, and the space where the file was is marked as being “free space”. The actual file is still there until a new file is created and the space is required. Then the old file contents are overwritten. Sometimes only parts of the file are overwritten.
- FTK Imager is a tool that allows us to produce images of different physical devices. It is free. The paid version is called Forensic Toolkit and includes features to
Essentially, it provides you with a single platform to manage and analyse data for a single investigation. It can quickly gather and highlight important data. But it is not a substitute for other tools like WinHex. You might use FTK as a starting point, but you might need to dig deeper.
- Autopsy is free open source forensics program that does what FTK does. It has different modules that can be used to analyse specific types of content, such as mobile data. Autopsy does not have a tool that creates the images, so we must first use another tool to create the different images and load them into autopsy.
- UFED is a tool (software-based or hardware-based) that can create images of mobile devices. It can also bypass user locks, encryption, and passcodes. UFED can also download data from social media and cloud accounts.
Not every device can be unlocked, but out of all the mobile forensics tools, UFED is the most effective and most regularly updated. - I recommend Sanderson Forensics’ Toolkit because it contains advanced features for analysing SQLite databases. Most mobile device content is stored inside SQLite database files.
Exploitation Frameworks
An exploitation framework is a hacking tool that can be used to simulate an attack on a network. A network security tester can run the exploitation framework to simulate an attack and identify areas of weakness. A hacker can use the exploitation framework to attack the network.
Metasploit is a popular exploitation framework written in Ruby. Metasploit has over 1500 common vulnerabilities, with additional vulnerabilities being added. The framework is used to infiltrate networks, collect data, and launch additional attacks once inside.
Password Crackers
A password cracker allows a user to crack a password. Password crackers can be online or offline:
- An online password cracker is one that is connected to a live system. For example, attempting to crack a password on a Windows computer connected to an Active Directory domain controller, or attempting to crack a password on an Apple iPhone. In an online attack, the host is verifying each password attempt, and may lock the account or self destruct after several incorrect attempts.
- An offline password cracker is not connected to a live system. For example, attempting to crack a password on a ZIP file or a password-protected Excel document. The ZIP file or Excel document does not know how many attempts a user has made. A user might take an online system and turn it into an offline system
- For example, a Windows computer connected to an AD domain controller will cache the most recent correct passwords on the computer. A hacker could disconnect the computer from the AD controller by removing the network cable, and then attempt to guess the password.
- For example, a computer will self destruct after ten incorrect password attempts. The computer records the number of incorrect attempts on a file. If the hacker had access to the file system or physical hard disk drive, he could make a copy of the computer’s data, try the password attempts on the copy, allow it to self destruct, make another copy, and then try again, repeating the process until the correct password is obtained.
An offline attack can be avoided with a TPM. When the TPM stores the password, then the TPM can keep track of each password attempt.
- For example, a Windows computer connected to an AD domain controller will cache the most recent correct passwords on the computer. A hacker could disconnect the computer from the AD controller by removing the network cable, and then attempt to guess the password.
There are several strategies for cracking a password
- Brute force; the cracker tries every combination of password. A computer or cellular phone may lock the account/self destruct if too many incorrect passwords have been attempted. The brute force cracker may have rules for the type of characters included (numbers, letters, special characters, etc.)
- Educated guess; the cracker tries common passwords such as the name of the user’s dog, the name of the user’s children, etc..
- Algorithm exploitation. A password cracker may attempt to exploit the underlying algorithm that has secured the password. If the password is stored as a hash, and the mathematics underlying the hash is weak, then mathematical methods may be used. Rainbow tables are a popular method for cracking password hashes.
If the system itself is weak, then cracking the password may not be the best method for gaining access. We might be able to find a back door.
If the users themselves are weak, then stealing the password from a user through social engineering may be a better method.
Data Sanitization
A data sanitization tool is a software or hardware device that erases data from a storage device. Data can be stored on
- Hard Disk Drives & Solid-State Drives
- Cellular phones
- Surveillance cameras
- Network switches, routers, and access points
A data sanitization tool might be software-based, or hardware based. For example, erasing data on a hard disk drive is commonly accomplished with a degausser. Erasing data on a hard drive installed in a computer can be completed with a bootable USB containing a data sanitization application.
It is important to choose a data sanitization tool that is best for the device being erased. Sometimes it is not possible to erase a device without physically destroying the device.
An organization may have a specific policy for destroying data. A government organization may have a specific policy for destroying data that is the law.
The Department of Defense uses DoD 5220.22-M Wipe Method to erase data. This process writes random data overtop of the drive three times, each time verifying the data that was written.
